Trusted webpage forensics system and trusted webpage forensics method based on three-layer trusted webpage forensic model
A trusted network and model technology, applied in the field of web data forensics and reconnaissance, can solve problems such as loss of criminal evidence, fixed storage devices, and lack of applicability to different organizations, achieving a balance of sensitivity, good practicability, and high reliability. The effect of credit forensics services
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
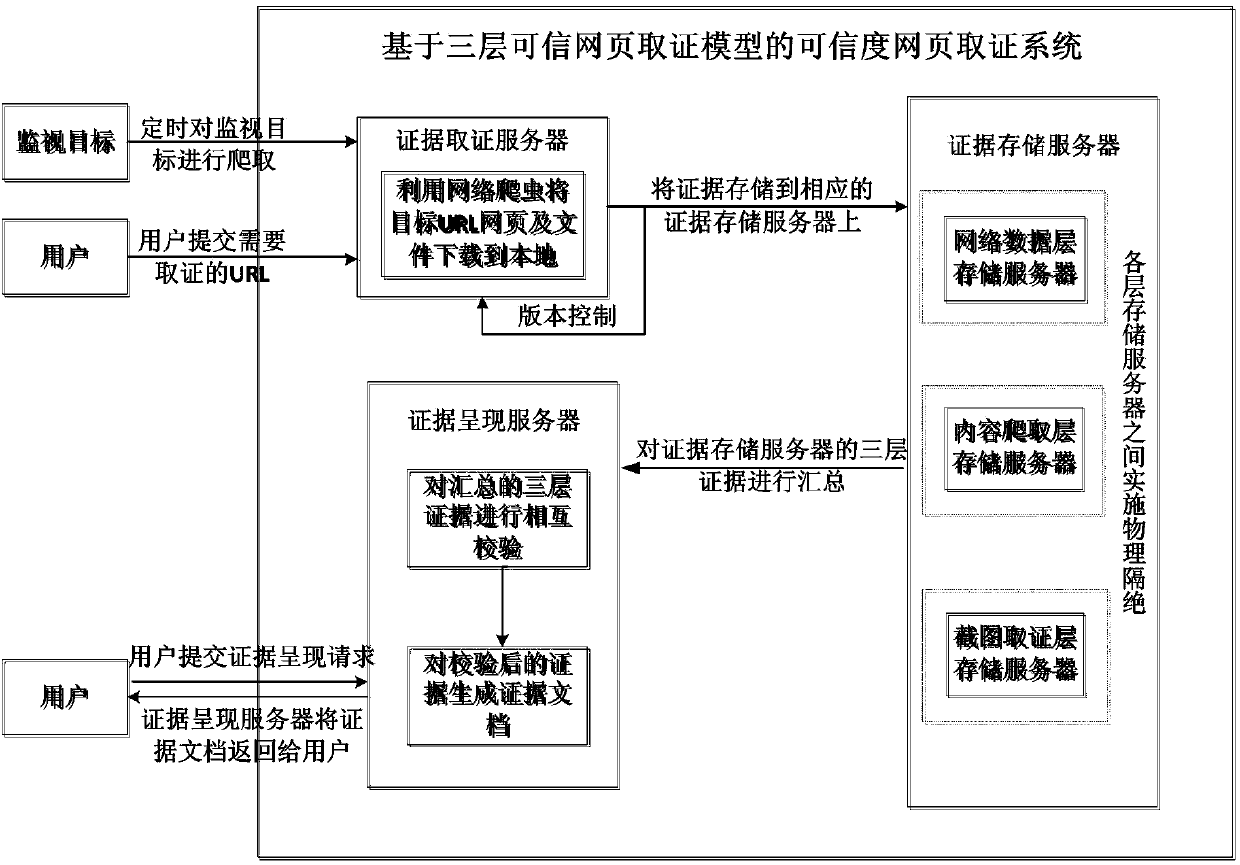
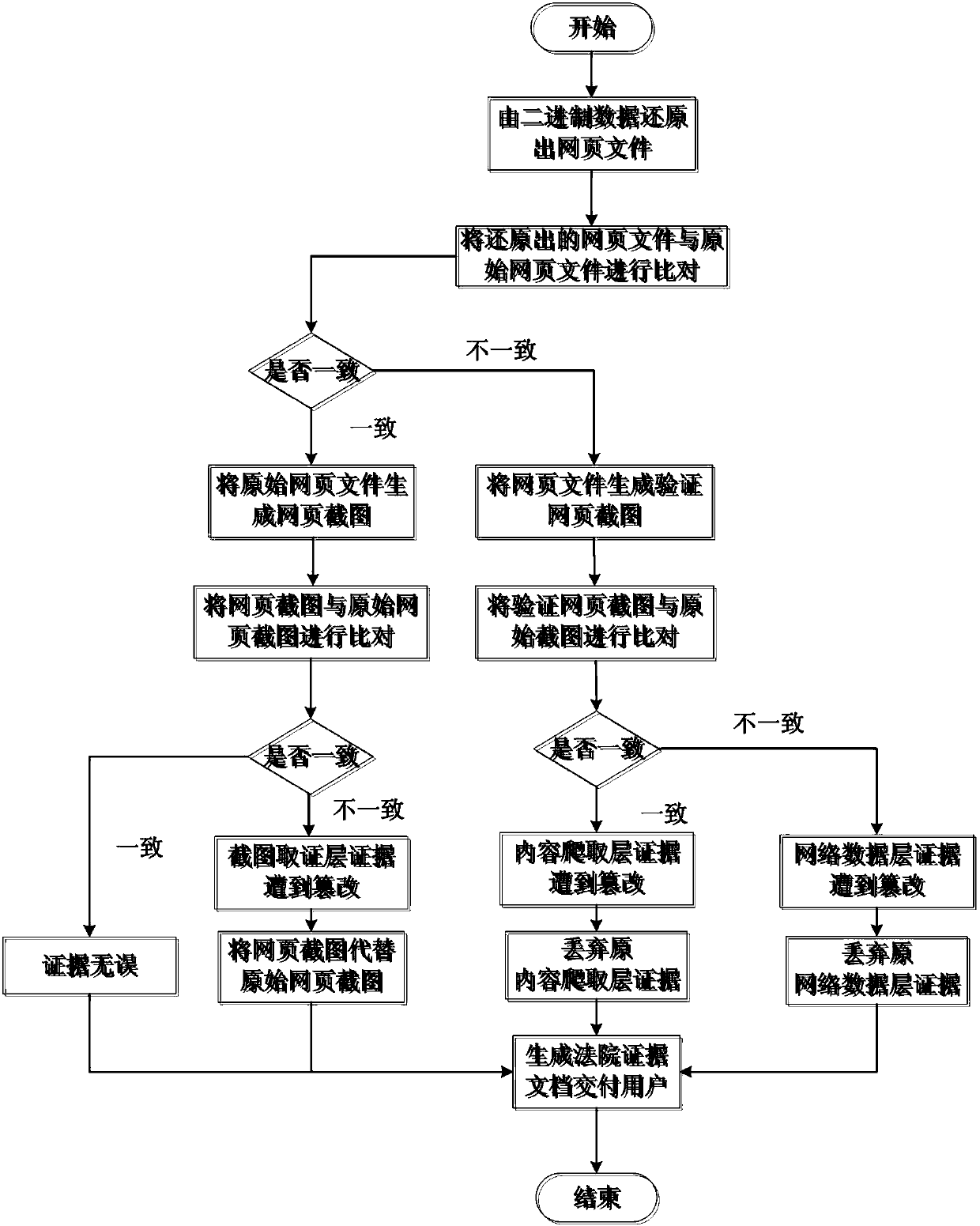
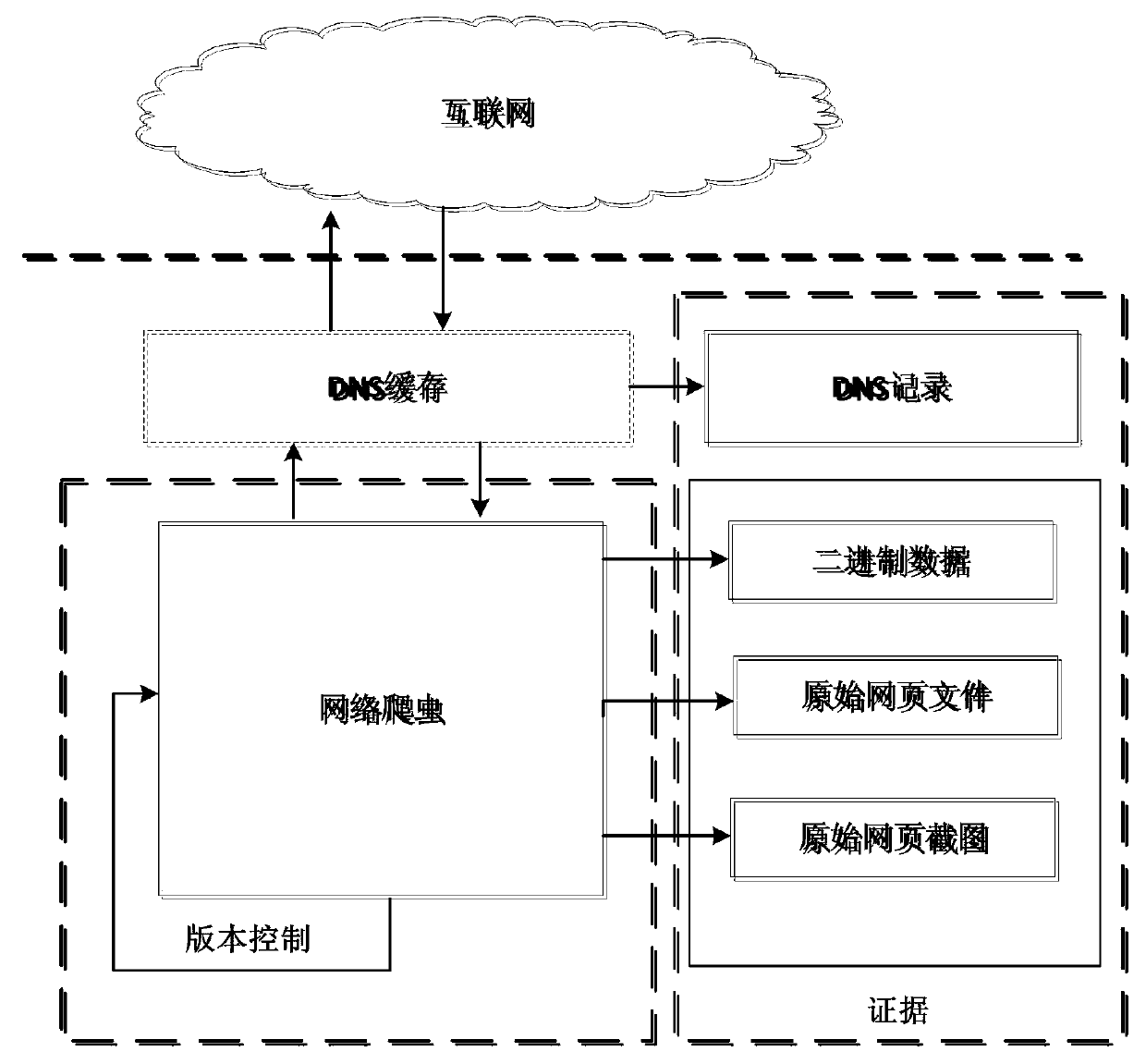
[0031] In this embodiment, the feature of the three-layer trusted webpage forensics model in a trusted webpage forensics system based on the three-layer trusted webpage forensics model is that the webpage forensics process is designed into three layers, from bottom to top are network data layer, The content crawling layer and the screenshot forensics layer perform data acquisition at different levels, and cross-validate the stored evidence at different levels; at the same time, restore the original web pages from the acquired web page components and display them in the local browser shown in reality. The bottom network data layer is responsible for recording network communication data, which are all original binary; the content crawling layer is responsible for saving related webpage files; the screenshot forensics layer takes screenshots of crawled webpages and saves them as pictures. Such as Figure 4 As shown, through the three-layer forensics model of this system, the evi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com