Method for guaranteeing self-security of JAVA program
A self-safe and procedural technology, applied in the field of cryptography and information security, can solve problems such as illegal acquisition and achieve high security effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0039] The invention proposes a method for protecting the security of the JAVA program itself by adopting the national secret algorithm.
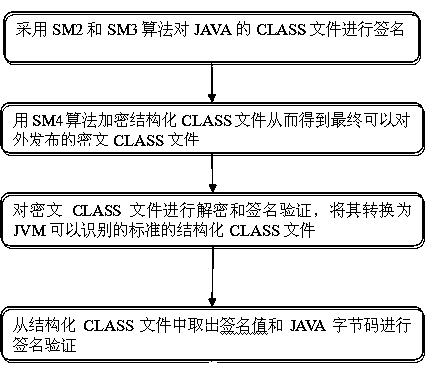
[0040] The design concept of this method is: first use the national secret algorithm SM2 and SM3 to sign the JAVA CLASS file, and then use the national secret algorithm SM4 to encrypt the CLASS file, effectively preventing the CLASS file from being decompiled and maliciously tampered with.
[0041] like figure 1 Shown, the present invention comprises the steps:
[0042] Step 1: Use the SM2 and SM3 algorithms to sign the CLASS file of the JAVA program, and combine the signature value and the CLASS file into one file in a fixed format to obtain a structured CLASS file.
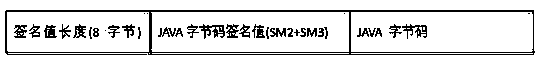
[0043] like figure 2 As shown, the structure of the structured CLASS file is: signature value length (8 bytes), JAVA bytecode signature value, and JAVA bytecode. The signature value is obtained by SM2 and SM3 algorithms.
[0044] Step 2: Encrypt the structured CLASS file...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com