Method and device for proving privacy protection attribute of RFID protocol
A privacy protection and attribute technology, applied in the field of Internet of Things communication technology and security, to improve computing efficiency, prevent tracking problems, and achieve the effect of privacy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
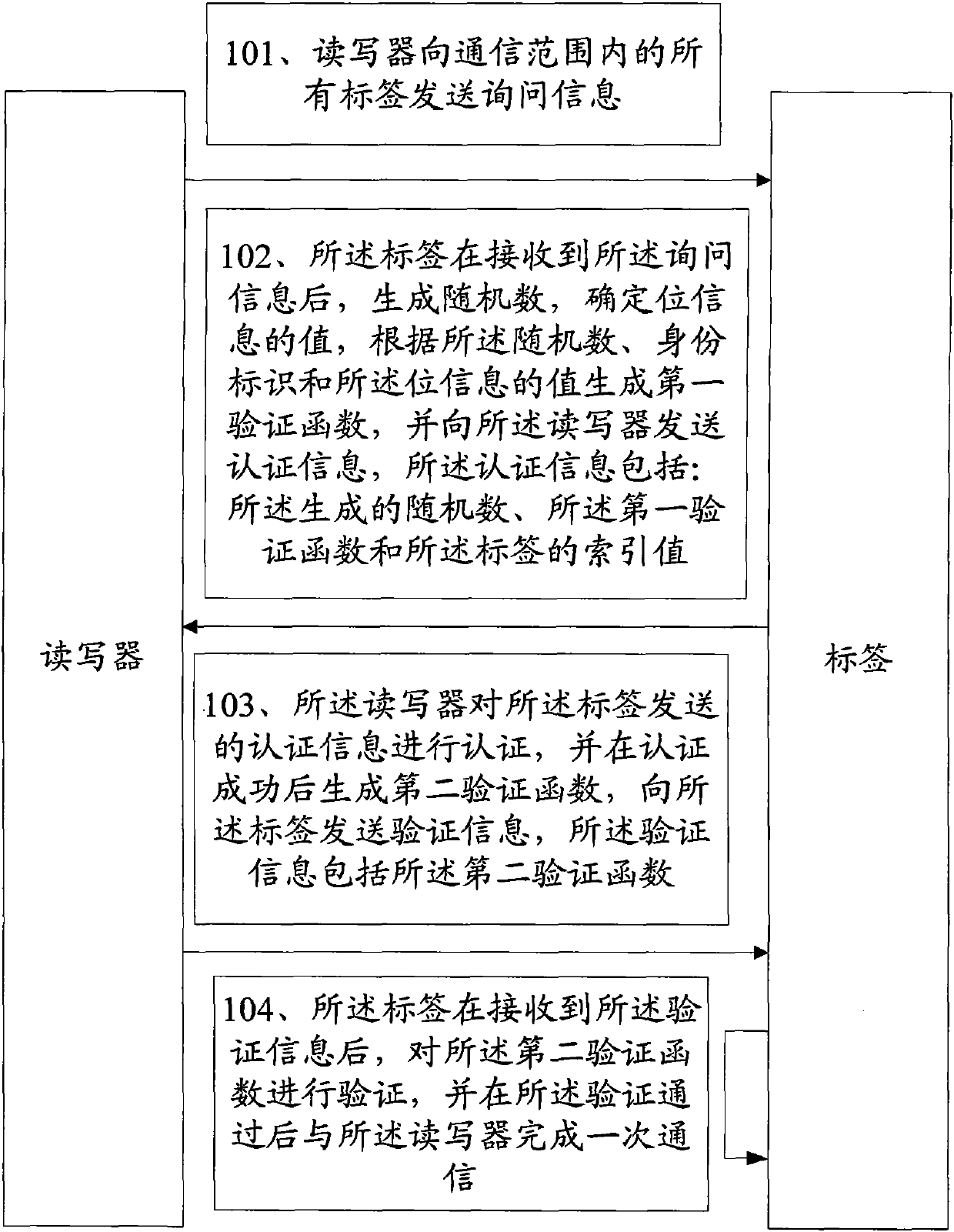
[0037] see figure 1 , a communication method in the Internet of Things is provided in this embodiment, including:
[0038] 101. The reader sends inquiry information to all tags within the communication range;
[0039] 102. After receiving the query information, the tag generates a random number, determines the value of the bit information, generates a first verification function according to the random number, the identity mark, and the value of the bit information, and sends a request to the reader The writer sends authentication information, where the authentication information includes: the generated random number, the first verification function, and the index value of the tag;
[0040] 103. The reader / writer authenticates the authentication information sent by the tag, and generates a second verification function after successful authentication, and sends verification information to the tag, where the verification information includes the second verification function;
...
Embodiment 2
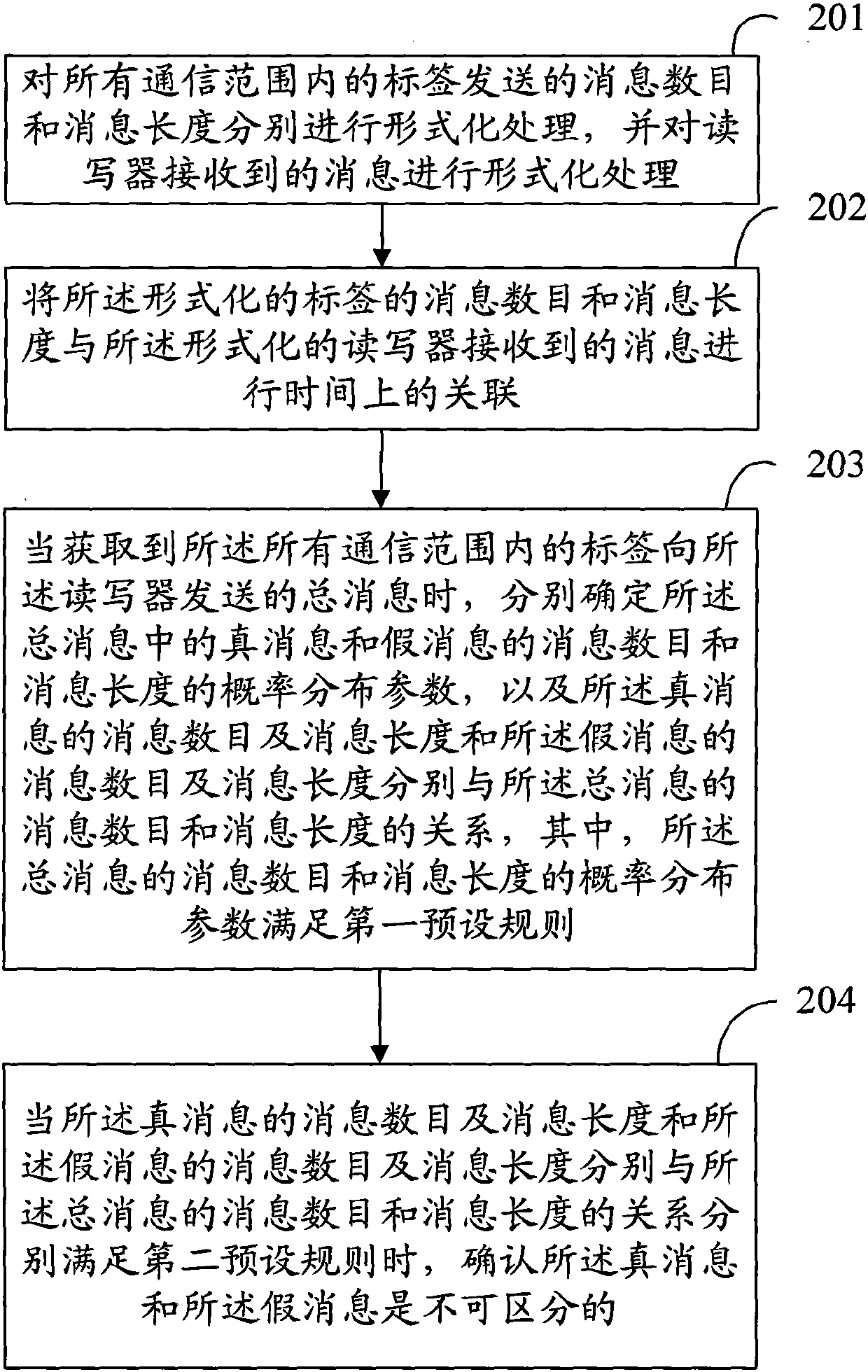
[0049] see figure 2 , the embodiment of the present invention provides a method for proving the privacy protection attribute of the RFID protocol, including:
[0050] 201. Formally process the number of messages and message lengths sent by all tags within the communication range, and formally process the messages received by the reader / writer;
[0051] 202. Time-associate the message number and message length of the formalized tag with the messages received by the formalized reader-writer;
[0052] 203. When the total messages sent to the reader by the tags within the communication range are obtained, determine the probability distribution parameters of the number of true messages and false messages in the total messages and the probability distribution parameters of the message lengths, and The relationship between the message number and message length of the true message and the message number and message length of the false message and the message number and message lengt...
Embodiment 3
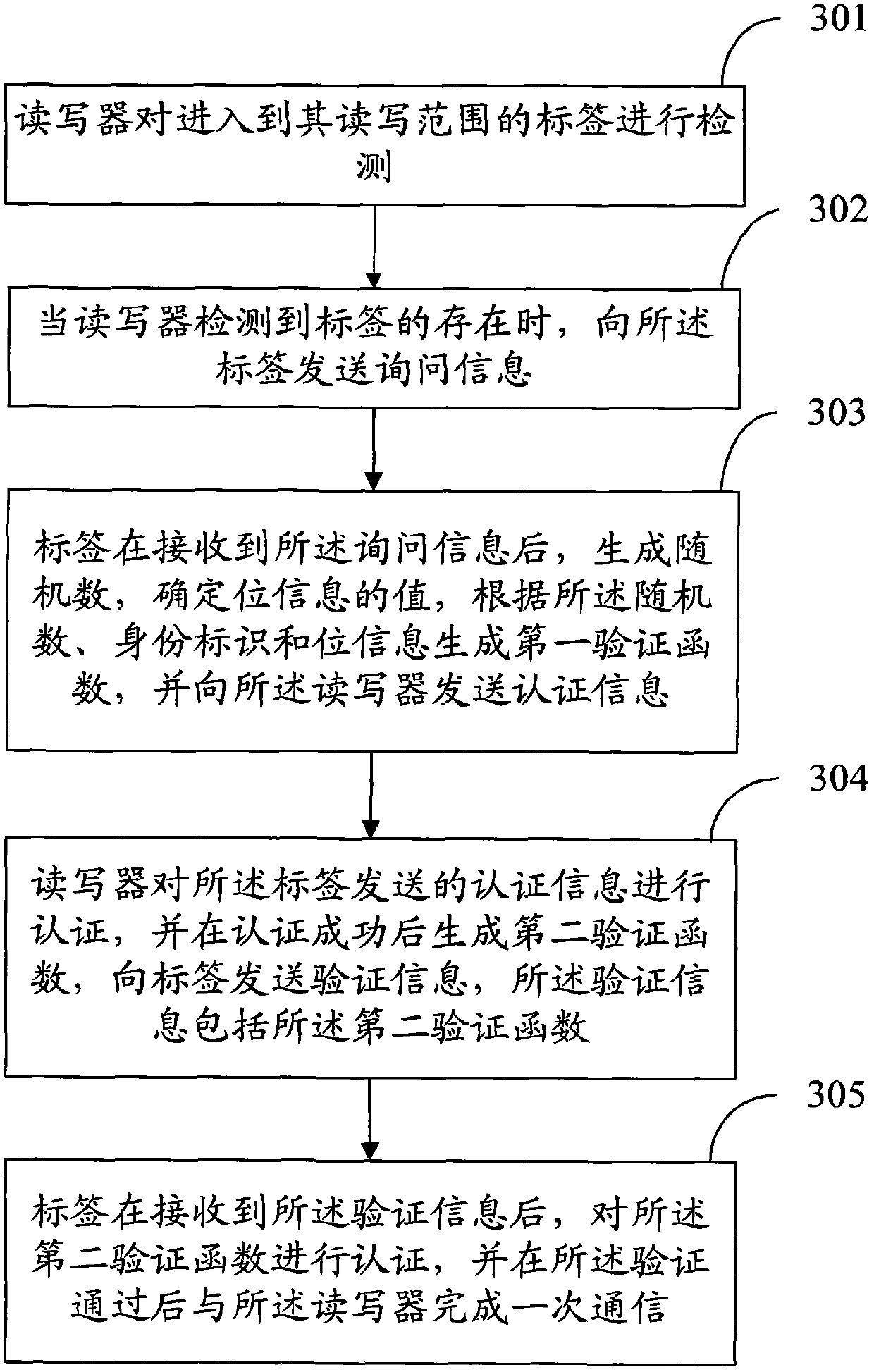
[0058] An embodiment of the present invention provides a communication method in the Internet of Things. The application scenario of this embodiment includes: multiple tags enter the reading and writing range of the reader, and the reader communicates with the multiple tags. Inside the tag includes: ID, key k, index Index, and hash function h(), encrypted pseudo-random function F ki () and bit information bit. In this embodiment, the reader-writer and the background database are considered as a whole. When the protocol is initialized, the reader internally stores the tuple (Index i , ID i , k i ), the value of the preset bit information bit and the pseudo-random function F ki (). see image 3 , the method flow includes:
[0059] 301. The reader / writer detects the tags entering its read / write range.
[0060] In this embodiment, the reader / writer detects the surrounding environment to confirm whether a tag enters its read / write range. The specific detection method is si...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com