A centralized DNS security monitoring method applied to routers
A security monitoring and router technology, applied in transmission systems, electrical components, etc., can solve problems such as adverse effects, stable network operation and application security threats, and achieve the effect of low deployment cost
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
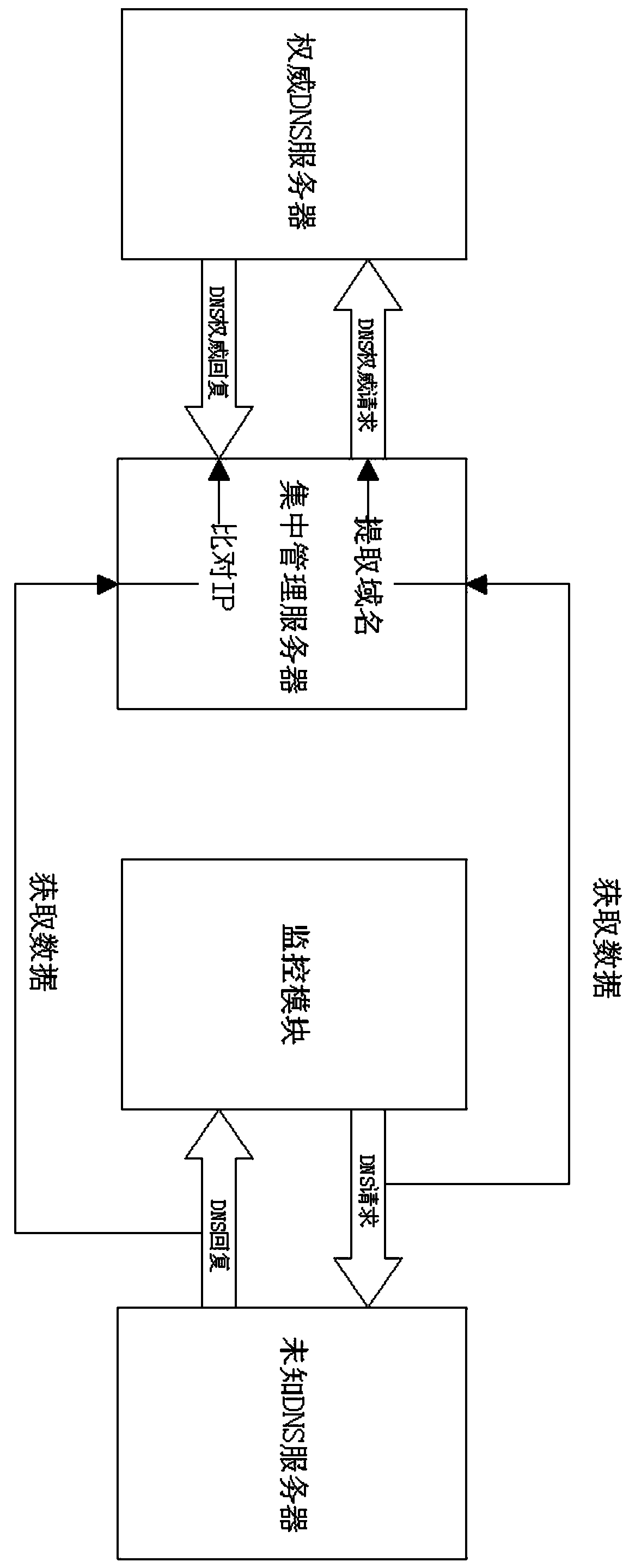
[0022] A centralized DNS security monitoring method applied to routers, comprising the following steps:
[0023] Step 1): By deploying the monitoring module on the router, when the router initiates a DNS resolution request to the DNS server each time, the monitoring module records the detailed data of the request and transmits it to the centralized management server;
[0024] Step 2): The centralized management server records the detailed data of the request, and then the centralized management server extracts the domain name field in the detailed data of the request, and uses the domain name field as the domain name to initiate a DNS resolution authoritative request to the authoritative DNS server, and when it receives a reply from the authoritative request Then record the reply data of the authoritative request;
[0025] Step 3): When the router receives the reply data requested from the DNS server, the monitoring module records the requested reply data and transmits it to t...
Embodiment 2
[0028] This embodiment is further optimized on the basis of the above embodiments. Further, in order to better realize the present invention, the following steps are included:
[0029] Step 1-1): By deploying the monitoring module on the router, when the router initiates a DNS resolution request to an unknown DNS server each time, the monitoring module records the detailed data of the request and transmits it to the centralized management server;
[0030] Step 2-2): The centralized management server records the detailed data of the request, and then the centralized management server extracts the domain name field in the detailed data of the request, and uses the domain name field as the domain name to initiate a DNS resolution authoritative request to the authoritative DNS server. After requesting the reply data, record the authoritative reply data;
[0031] Step 3-3): When the router receives the response data to the request from the unknown DNS server, the monitoring module ...
Embodiment 3
[0034] This embodiment is further optimized on the basis of the above embodiments. Further, in order to better realize the present invention, the unknown DNS server is specifically determined by the network configuration of each router, and the configuration is set by the router administrator. Addresses, IP addresses may be tampered with due to attacks.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com