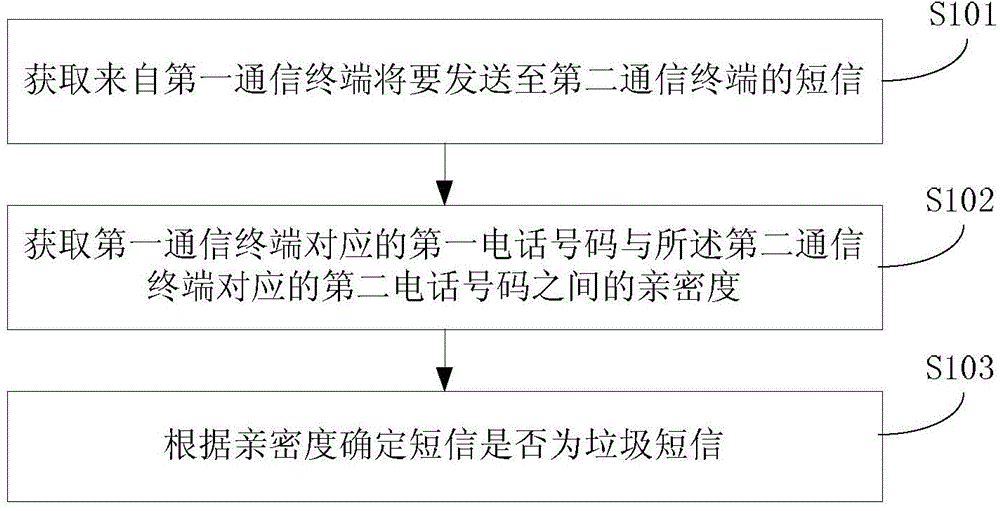
Spam short message identification method, device and equipment
A technology of spam short message and identification method, applied in the field of communication, can solve the problem of not being able to intercept spam short messages
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
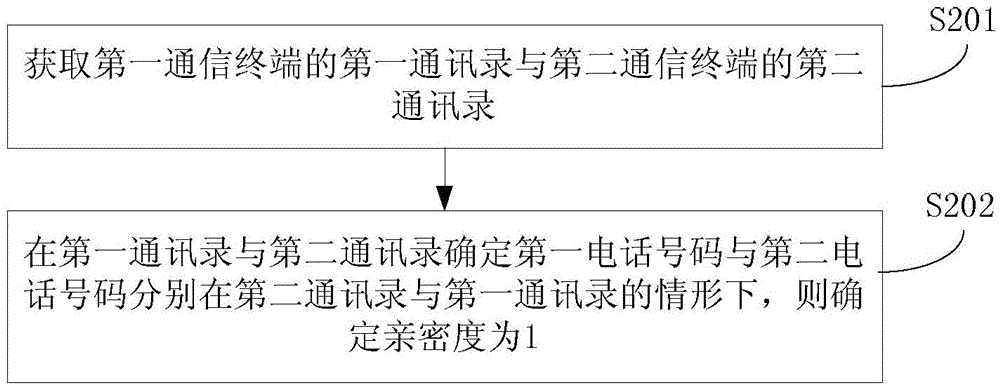
[0124] Embodiment 1 Using the above method provided by the embodiment of the present disclosure, the method for determining intimacy when the first phone number and the second phone number are friends in the address book, such as figure 2 As shown, do the following:
[0125] In step S201, the first address book of the first communication terminal and the second address book of the second communication terminal are acquired.
[0126] In one embodiment, the first address book and the second address book have been respectively backed up by the first user and the second user in the server on the network side; The second communication terminal sends a request message for obtaining the address book, and the first communication terminal and the second communication terminal return their respective address books to the server after receiving the request message.
[0127] In step S202, if the first address book and the second address book determine that the first phone number and the...
Embodiment 2
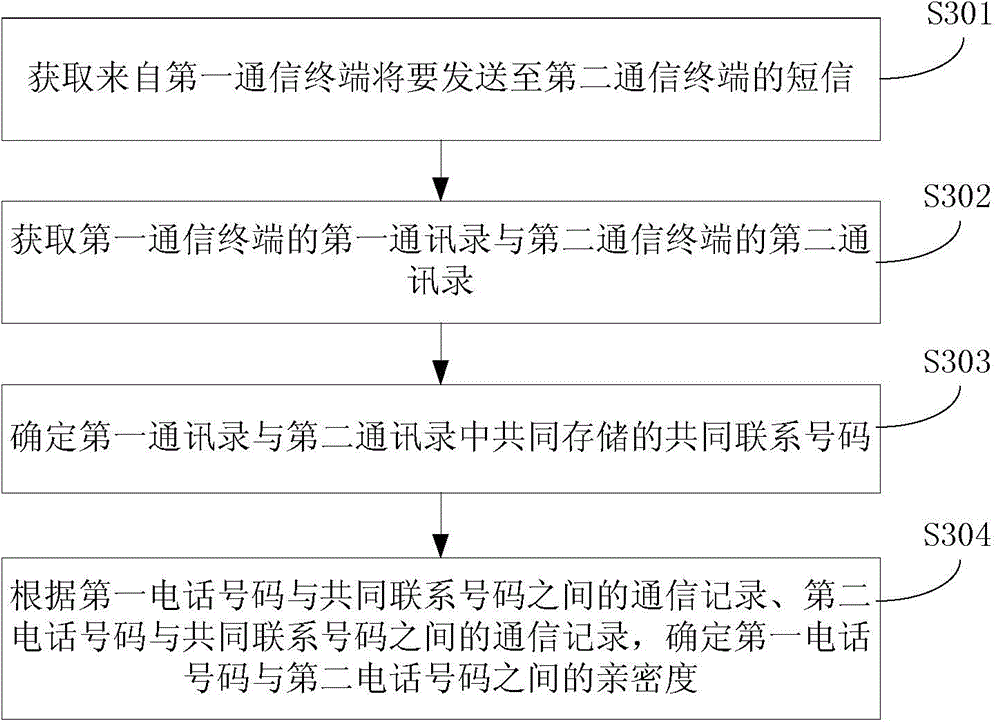
[0130] Embodiment 2 Using the above-mentioned method provided by the embodiment of the present disclosure, the intimacy between the two communicating parties is determined when the first phone number and the second phone number are not friends of each other or at least one of them is not a friend of the other party, as shown in Figure 3A As shown, do the following:
[0131] In step S301, a short message to be sent from a first communication terminal to a second communication terminal is acquired.
[0132] In step S302, the first address book of the first communication terminal and the second address book of the second communication terminal are obtained.
[0133] In step S303, the common contact number stored in the first address book and the second address book is determined.
[0134] In step S304, the degree of intimacy between the first phone number and the second phone number is determined according to the communication records between the first phone number and the comm...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com