Cross-site scripting attack defense method and device, application server
A cross-site scripting attack and application server technology, which is applied in the computer field, can solve problems such as low efficiency and heavy workload, and achieve the effect of reducing workload and improving efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
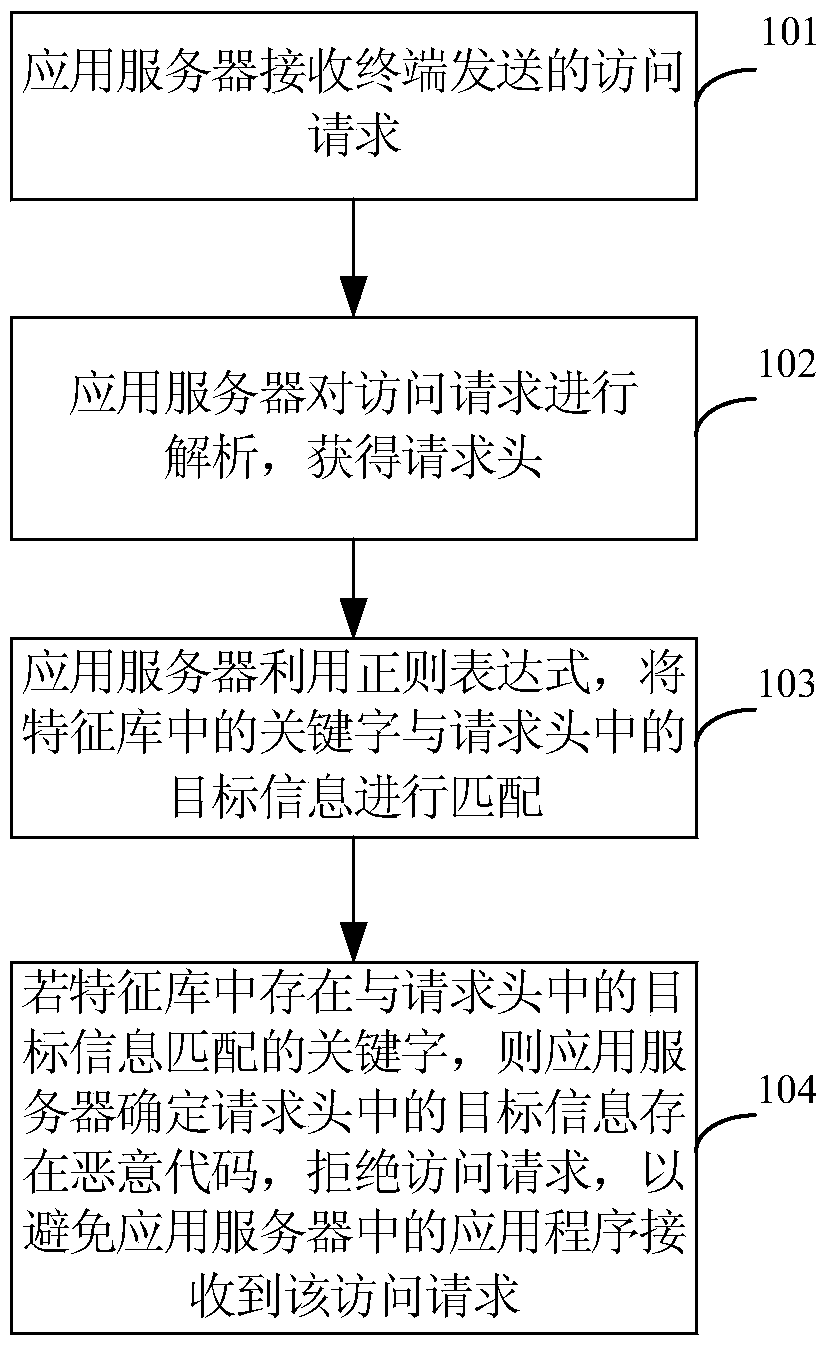
[0021] figure 1 A schematic flowchart of a cross-site scripting attack defense method provided by an embodiment of the present invention, as shown in figure 1 shown, including:
[0022] 101. The application server receives the access request sent by the terminal.
[0023] Wherein, the access request is used to request access to the application program in the application server.
[0024] Before step 101, the application server analyzes the malicious codes of historical XSS attacks, obtains the keywords of the malicious codes, and establishes a feature library storing the keywords of the malicious codes.
[0025] 102. The application server parses the access request to obtain the request header.
[0026] Wherein, the request header includes the target information input by the terminal through the form of the Web page.
[0027] 103. The application server uses a regular expression to match the keywords in the feature library with the target information in the request header. ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com