Power consumption attack method based on convolutional neural network and selection message method
A convolutional neural network and power attack technology, applied in neural learning methods, biological neural network models, neural architectures, etc., can solve problems such as power consumption curve observation, reduce attack accuracy, implement simplicity, and reduce attacks The effect of complexity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0024] The power consumption attack method based on the convolutional neural network and the selected message method of the present invention will be described in detail below with reference to the embodiments and the accompanying drawings.
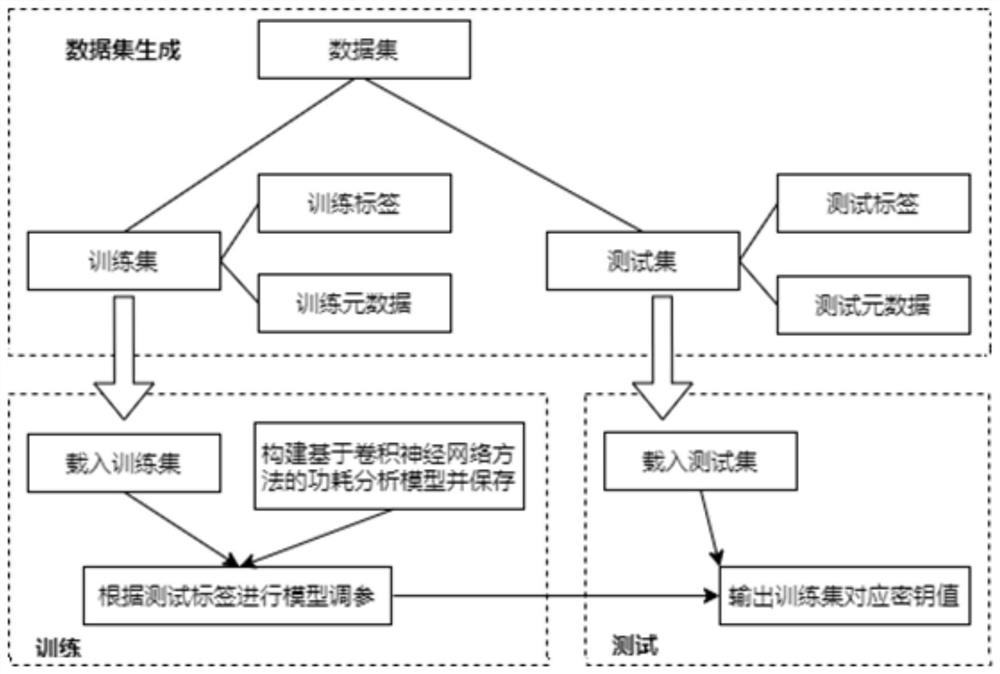
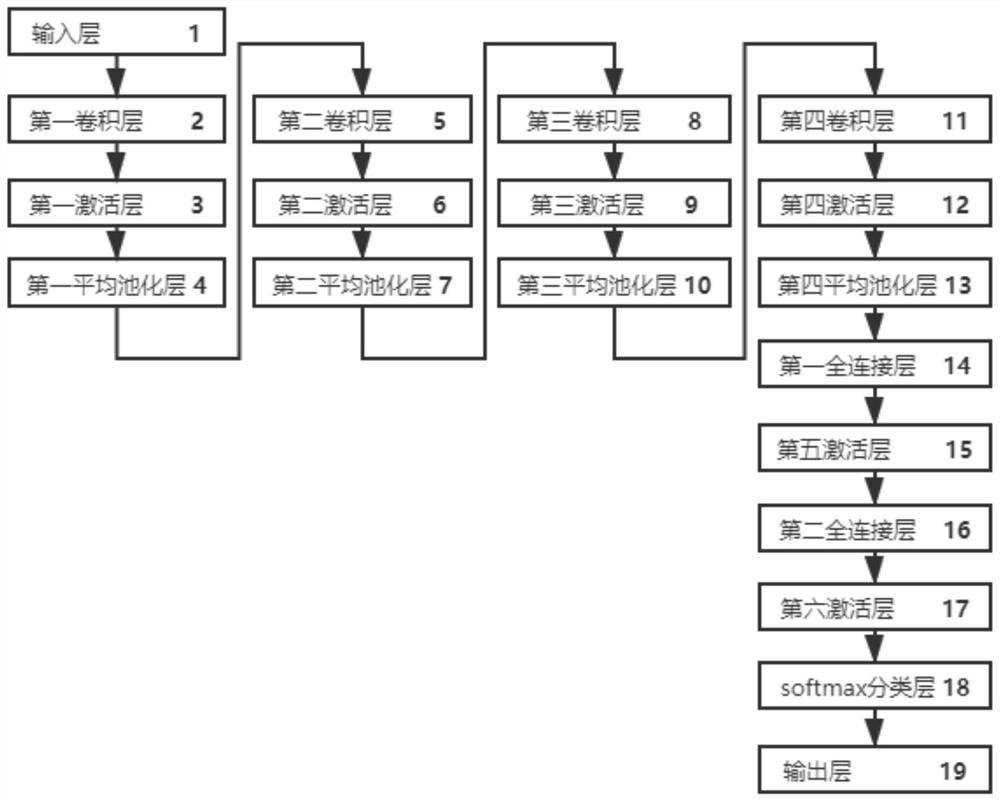
[0025] Such as figure 1 As shown, the power consumption attack method based on the convolutional neural network and the selected message method of the present invention includes the following steps:
[0026] 1) Build a data set based on the public key encryption algorithm (RSA), including a training set and a test set; including:
[0027] Select the message number 1 as the encrypted input message, and input it into the encryption program blinded Boscher modular exponentiation algorithm in the field programmable array FPGA; execute the encrypted program blinded Boscher modular exponentiation algorithm on the field programmable array FPGA, and collect the voltage function during execution Consumption data, that is, to obtain the voltage a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com