A wireless network security access method, device and terminal
A security access and wireless network technology, applied in the field of devices and terminals, wireless network security access methods, can solve the problems of low security and reliability, poor applicability, etc., to avoid network intrusion, enhance security and reliability Sex, protection from infestation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
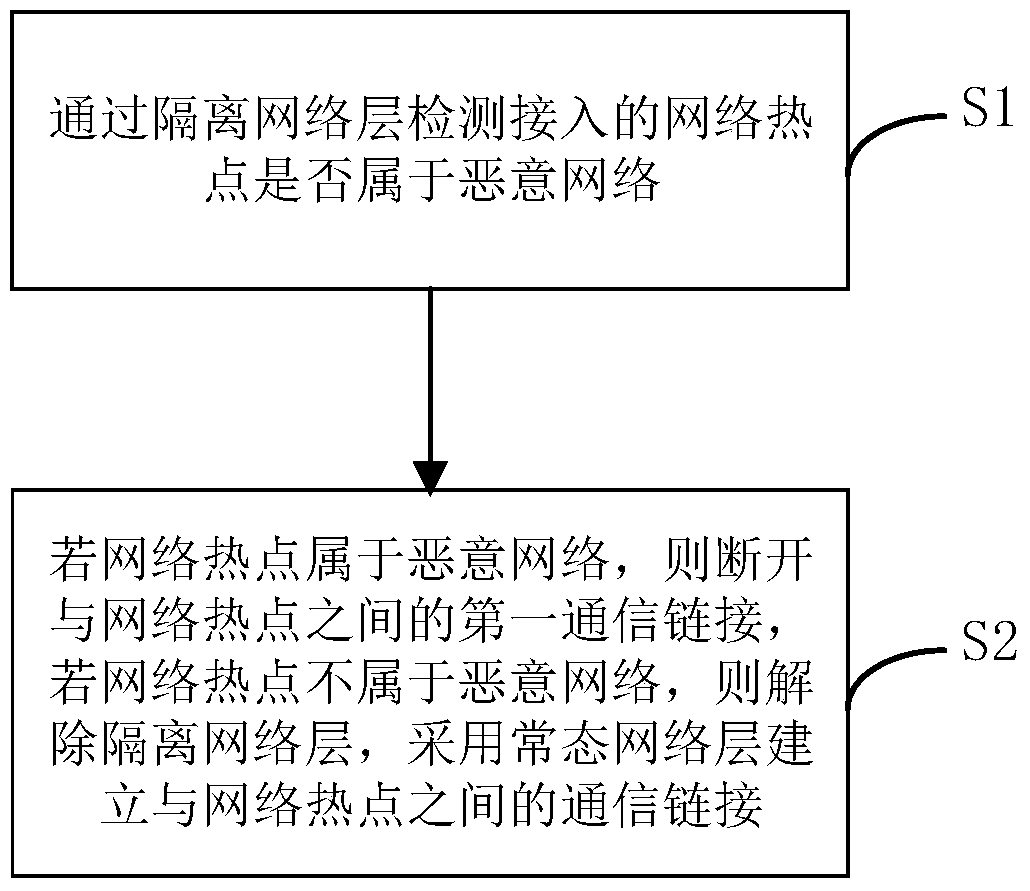
[0052] figure 1 It is a flow chart of the wireless network security access method proposed by the present invention. The method includes:
[0053] S1, by isolating the network layer to detect whether the accessed network hotspot belongs to a malicious network. It can be understood that the wireless network secure access method proposed in this embodiment is applicable to smart devices with network access functions such as smart phones and tablet computers. Wherein, the isolated network layer may be a virtual network layer built on a basic network or a normal network. There is a corresponding isolation mechanism between the network data of the isolated network layer and the local machine, through which the external network data can prevent the occurrence of dangerous events such as malicious network intrusion on the local machine.
[0054] Further, set the corresponding isolation network layer for the object that needs to be protected on this machine. For example, if only th...
Embodiment 2
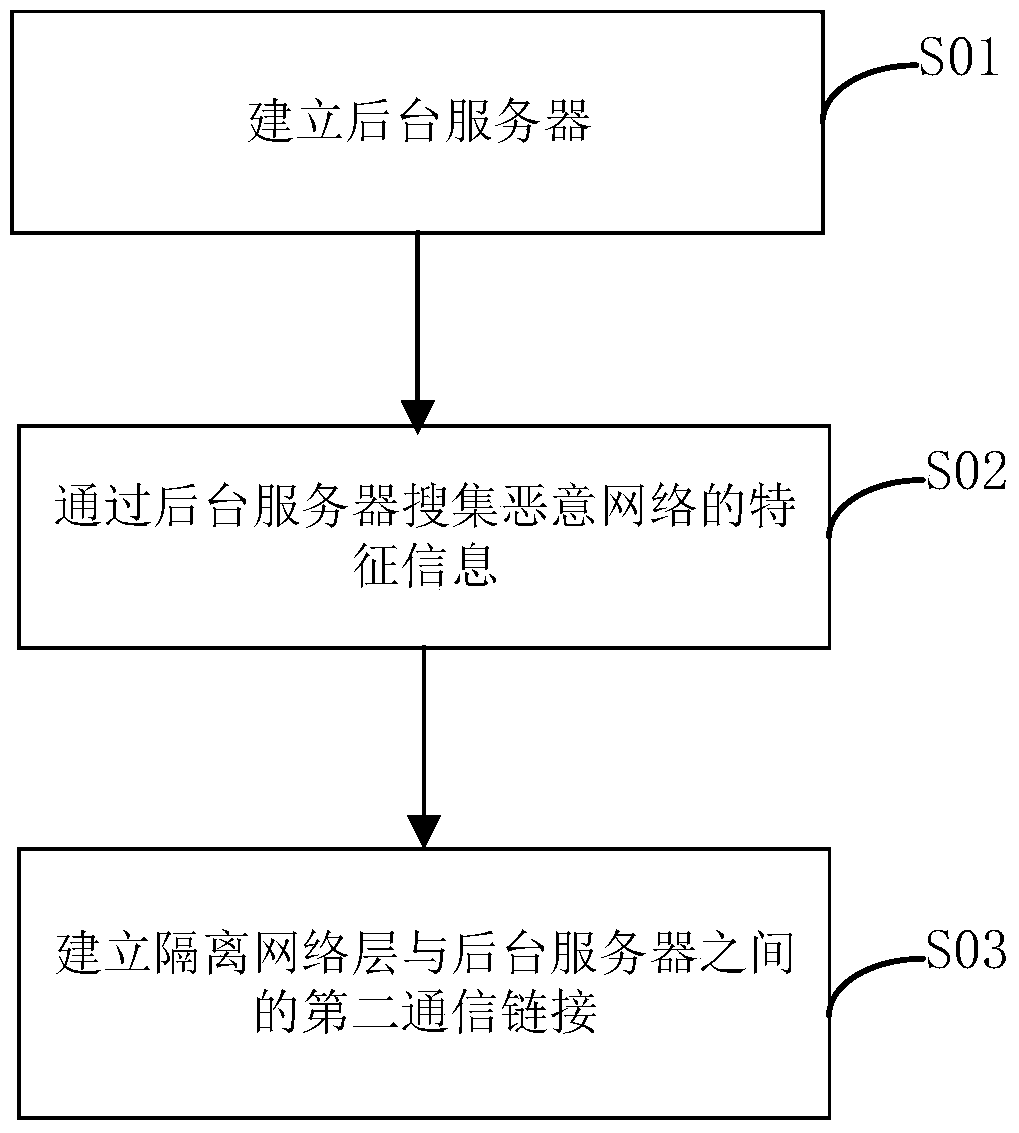
[0061] figure 2 It is a flow chart of the wireless network secure access method proposed by the second preferred embodiment of the present invention. Based on the first embodiment above, before detecting whether the accessed network hotspot belongs to a malicious network by isolating the network layer, it also includes:
[0062] S01, establishing a background server. It can be understood that the background server may be a cloud server or a background function module that runs independently of the device and can run independently. The same data processing, data analysis and data update operations as those of the cloud server are realized through the background function module.
[0063] S02, collecting characteristic information of malicious networks through a background server. The characteristic information of a malicious network may be signature information, keyword information, screenshot information, address information, malicious link information, and blacklist inform...
Embodiment 3
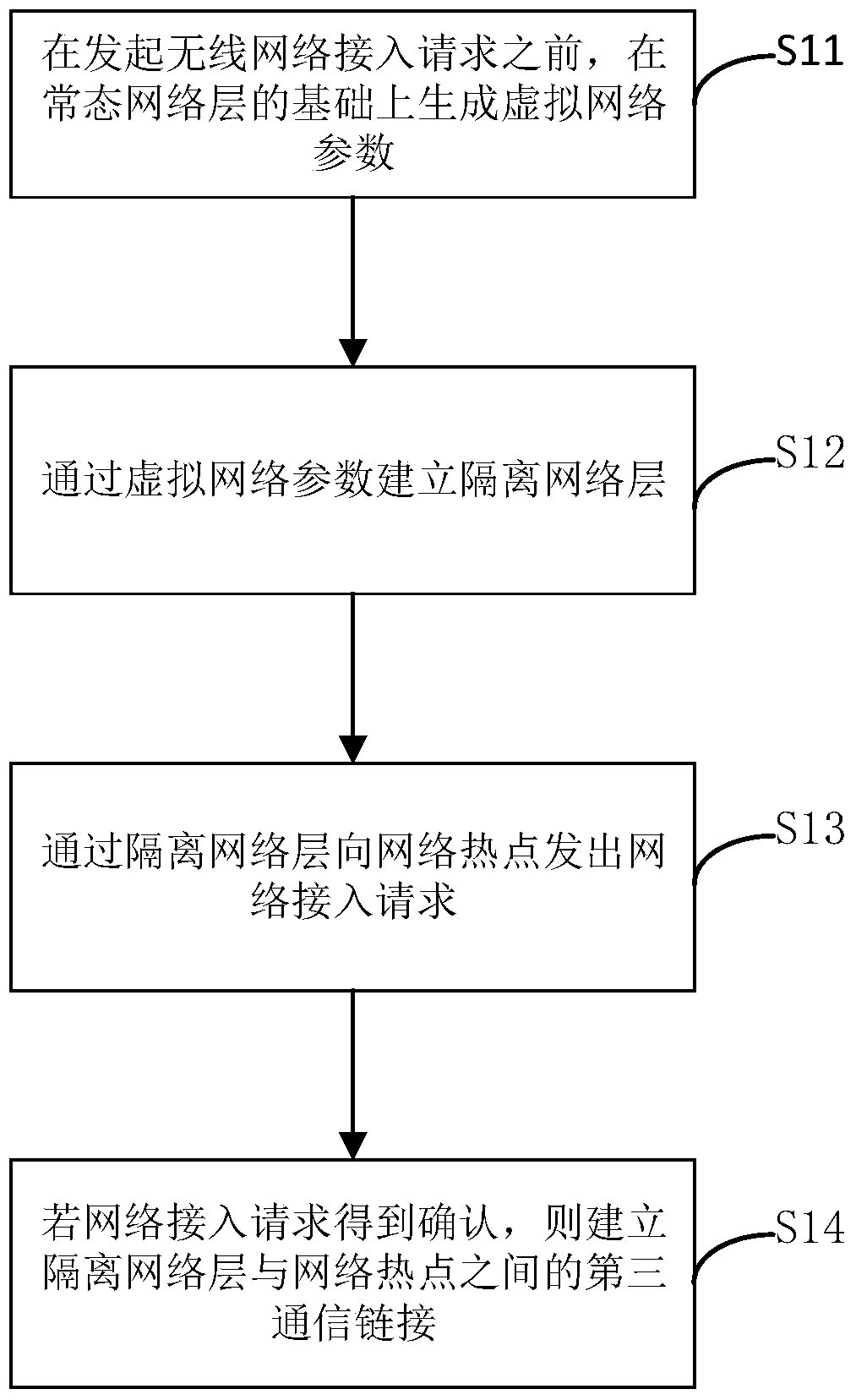
[0069] image 3 It is a flow chart of the wireless network security access method proposed by the third preferred embodiment of the present invention. Based on the first and second embodiments above, detecting whether the accessed network hotspot is a malicious network by isolating the network layer specifically includes:
[0070] S11. Before initiating a wireless network access request, generate virtual network parameters on the basis of a normal network layer. For example, a virtual network is established on the basis of a normal network layer, specifically, a virtual network card address, a virtual communication address, a virtual communication protocol, and the like of the virtual network are established.
[0071] Further, the virtual network parameters may be generated locally or provided by a third-party security service organization.
[0072] S12. Establish an isolation network layer by using virtual network parameters. Establishing a network layer by using network p...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com