A method to ensure the security of buyers and sellers in online transactions
A network transaction, the technology of both parties, applied in the field of network transactions, can solve the problem that the seller cannot obtain the payment, the defect, the buyer cannot use the serial number of the point card, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
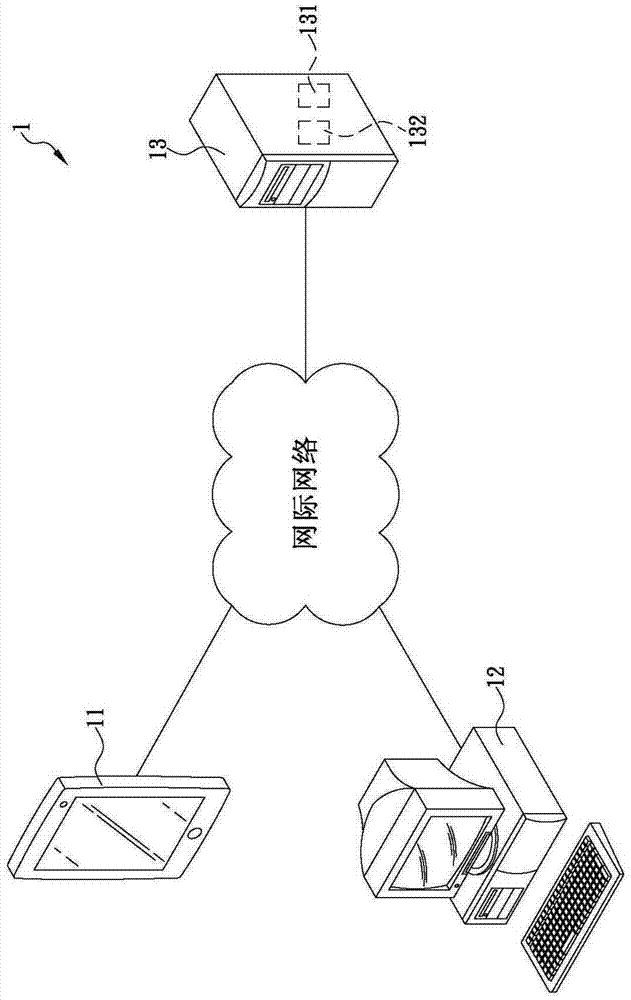
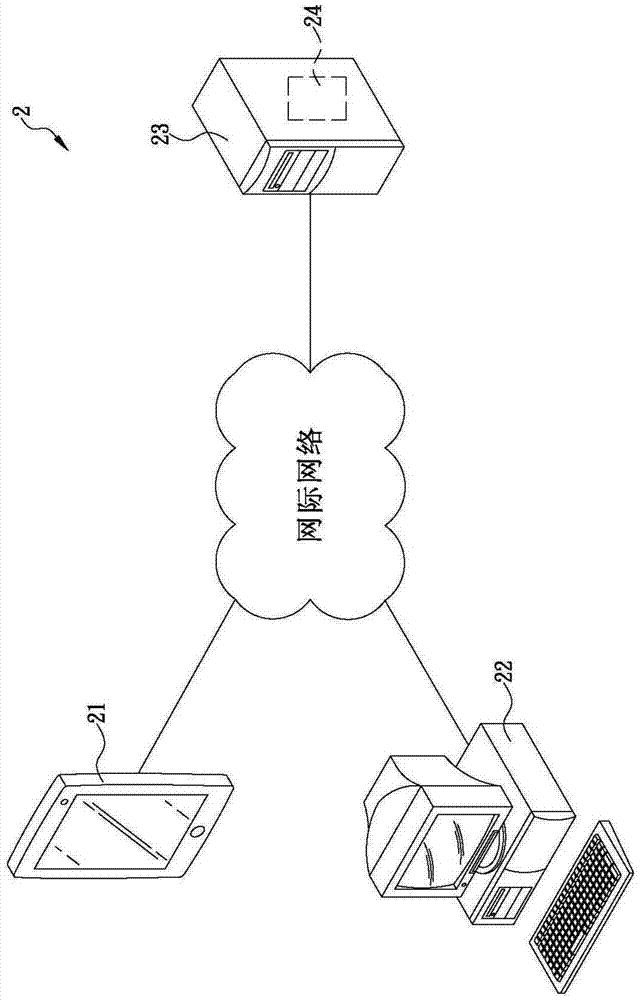
[0043] The present invention is about a method that can guarantee the security of buyers and sellers in network transactions, please refer to figure 2 , in a first embodiment of the present invention, the method is applied to a network transaction system 2, the network transaction system 2 includes a first terminal device 21, a second terminal device 22, a third-party server 23 and a The verification unit 24, in this embodiment, the verification unit 24 is located in the third-party server 23, but, in other embodiments of the present invention, according to the business model requirements of the industry, the verification unit 24 can be located in a In the game manufacturer's server, Chen Ming first.
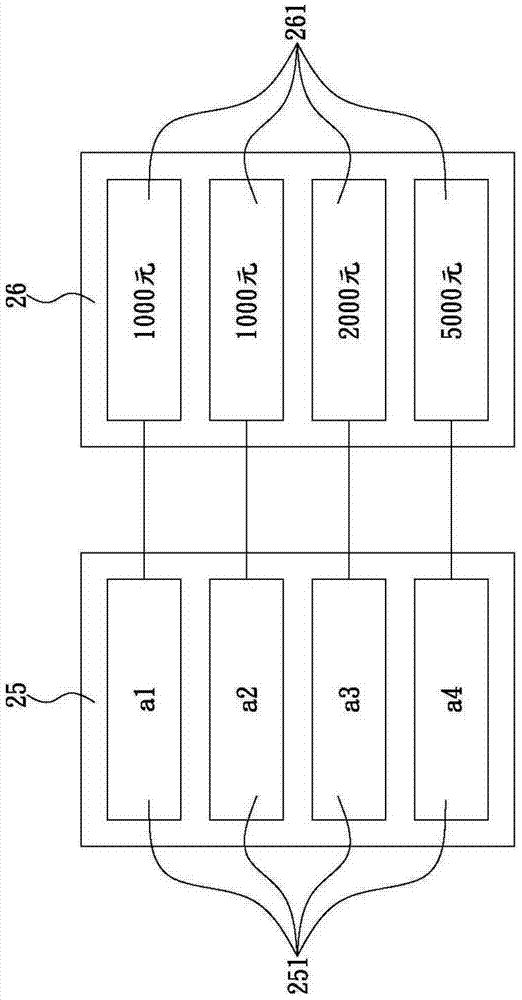
[0044] Inherited, see figure 2 and image 3 As shown, the third-party server 23 can be connected to the terminal devices 21 and 22 respectively through the Internet, and is provided with an account data 24 and a payment data 25. The account data 25 includes multiple accounts...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com