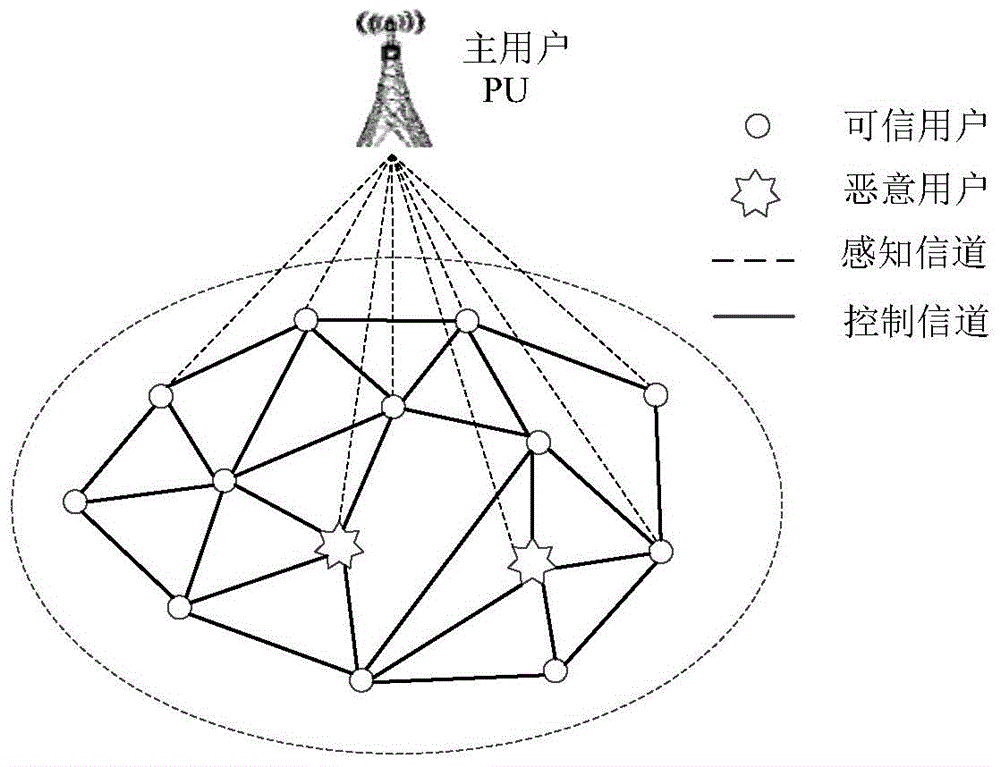
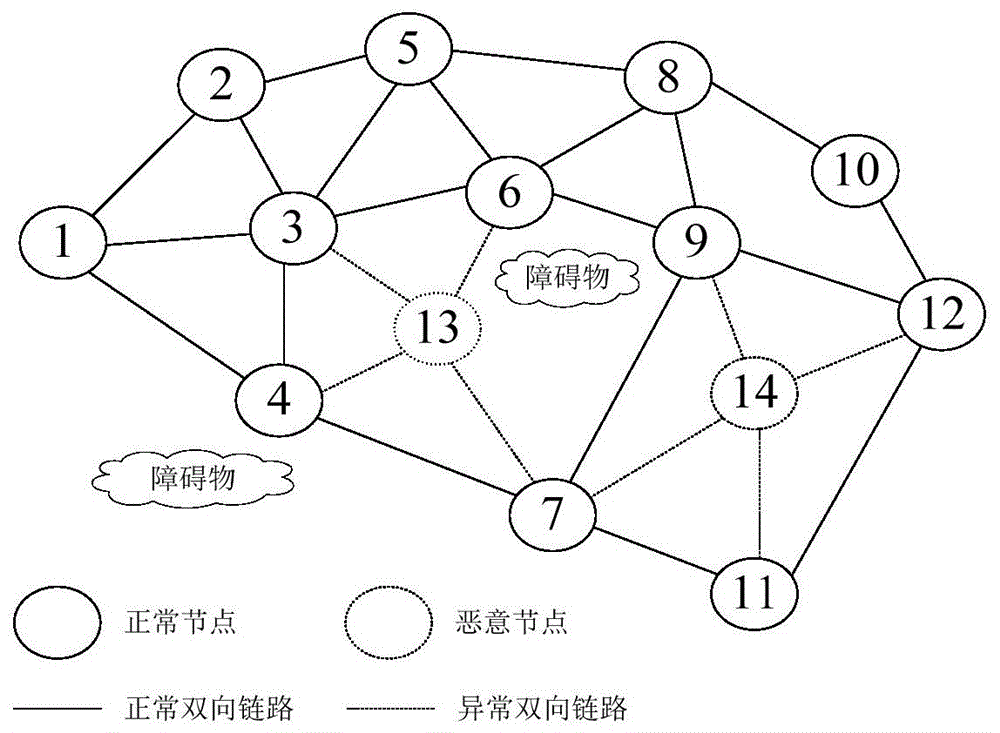
Method and device for resisting spectrum sensing data falsification through distributed cognitive radio network
A cognitive wireless network and sensing data technology, which is applied in the field of distributed cognitive wireless network against tampering sensing data attacks, can solve problems such as iterative process disorder, difficulty in resisting SSDF attacks, and too harsh assumption conditions, and achieve the effect of improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach
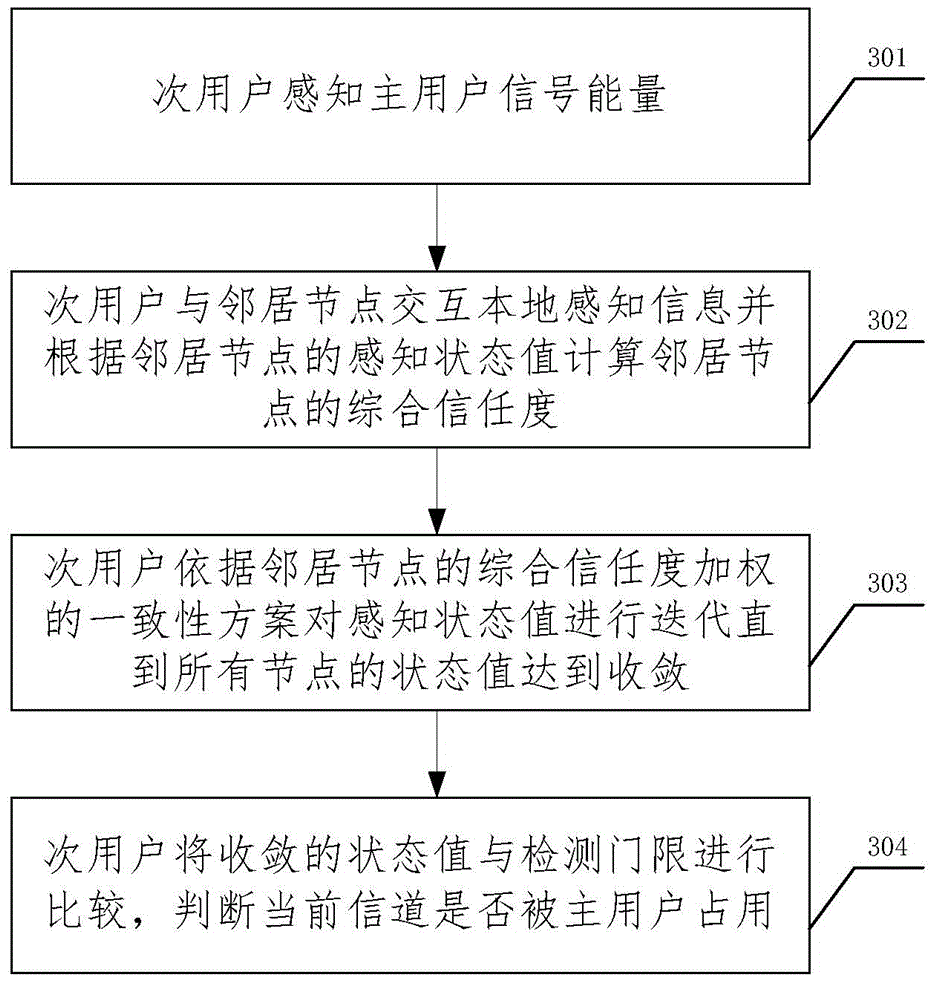
[0149] As a preferred implementation manner, the consistency iteration based on trust degree weighting in the present invention includes:
[0150] The energy state value of neighbor nodes received by secondary user i Perform weighted iterative operations:
[0151] X i t = X i t - 1 + λ Σ j ∈ Ne i Tr i , j t ( X j t - X i t )
[0152] in, and Respectively represent the state value of the i-th secondary user at time t and time t-1, λ i...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com