Secret image sharing method based on pixel mapping matrix embedding
A pixel mapping and secret image technology, applied in the field of information security, can solve the problems of large carrier image size, large share size, large camouflage image, etc., and achieve the effect of improving transmission speed, improving embedding ability, and enhancing embedding ability.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0022] Combine below Attached picture The present invention is further described.
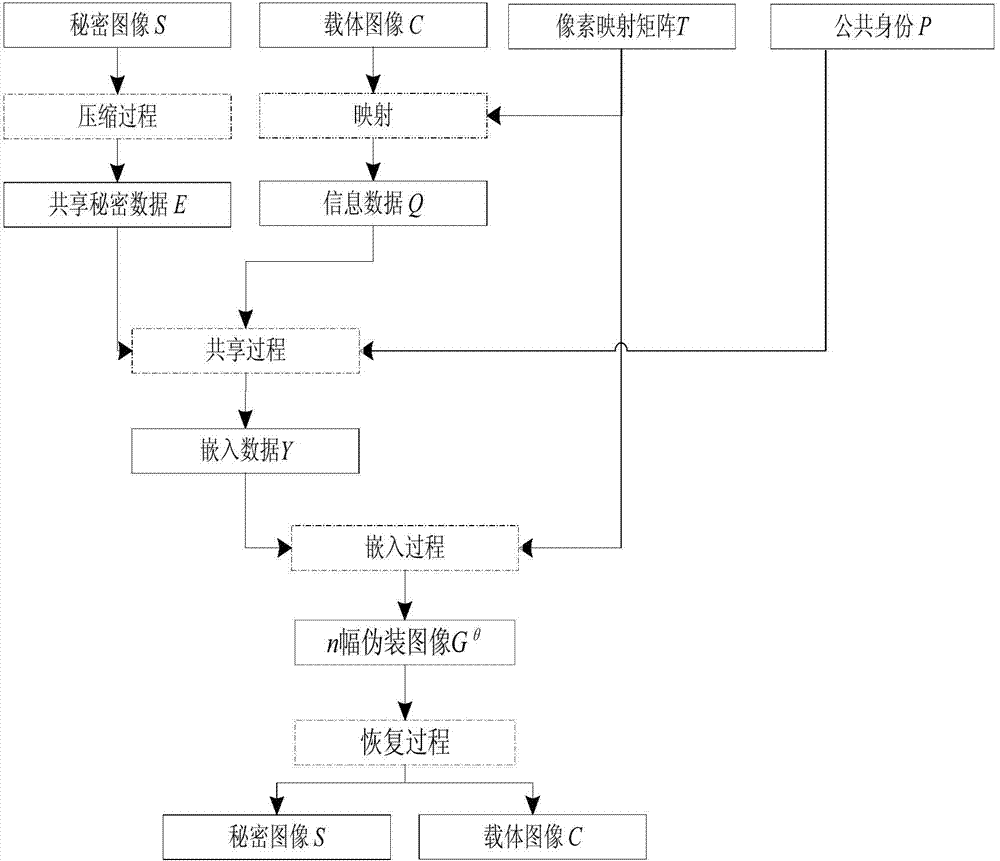
[0023] refer to figure 1 , the implementation steps of the present invention are as follows:
[0024] Step 1, input secret image S, cover image C, pixel mapping matrix T and public identity P.
[0025] The secret image S is the image that needs to be protected; the carrier image C is used to hide the secret image S; the pixel mapping matrix T specifies the embedding rules for embedding the secret image S into the carrier image C, and it also specifies the mapping rules for generating the information data Q ; The public identity P is the identity of the participants, and each participant holds a public identity.
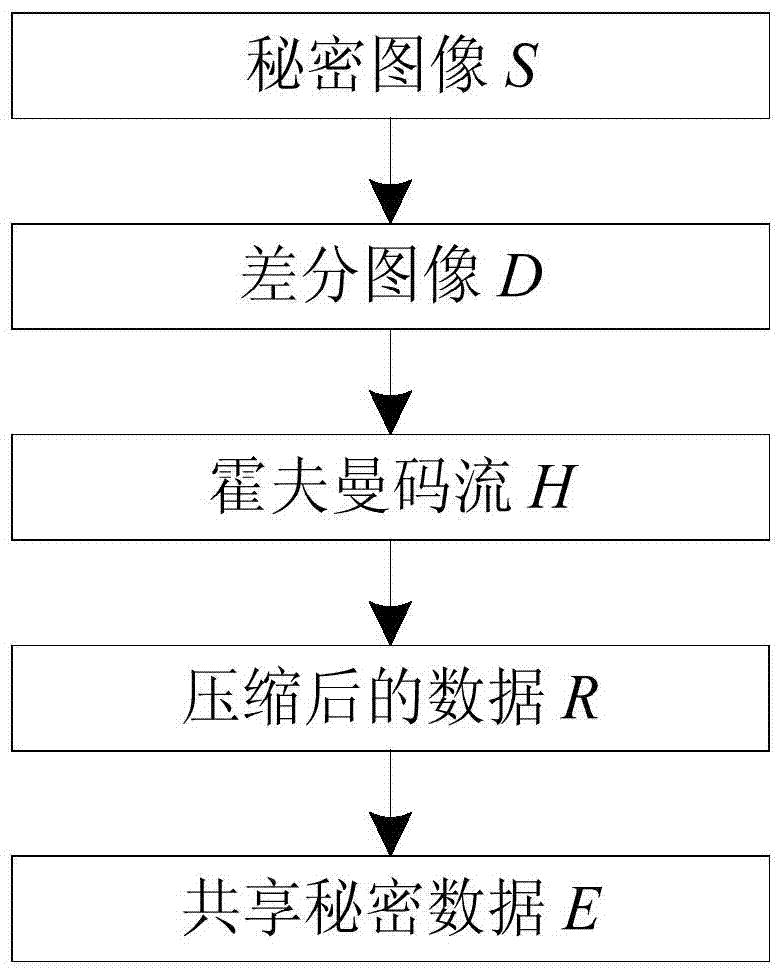
[0026] Step 2, compress the secret image S.
[0027] refer to figure 2 , the specific implementation of this step is as follows:
[0028] 2a) Perform differential encoding on the secret image S to obtain a differential image D;
[0029] 2b) Arrange the elements of the dif...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com