User identity authentication method and device
A technology of user identity and verification method, which is applied in the direction of user identity/authority verification, message/email/notification, etc., can solve the problems that the execution efficiency needs to be further improved, and achieve the effect of improving execution efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
[0024] This embodiment provides a technical solution of a user identity verification method. The technical solution can be implemented by a user terminal, which can be connected to the Internet through 2G, 3G, 4G, WIFI, etc., so as to perform data communication with the server of the application program through the above connection method.
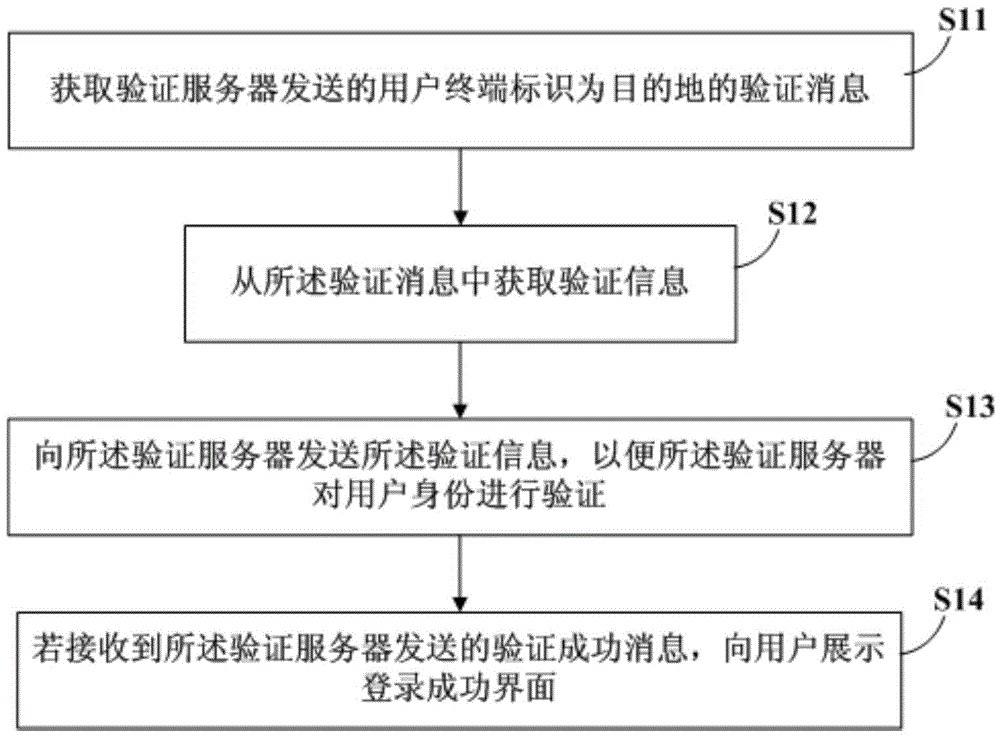
[0025] see figure 1 , the user authentication methods include:
[0026] In S11, acquire a verification message sent by the verification server and identified as a destination by the user terminal, where the verification message includes a verification text message or a verification multimedia message.
[0027] Many application clients installed on user terminals require users to log in before using them. Generally speaking, users at least need to enter their own passwords when performing login on the client side. Since the user is likely to forget his password, the user often enters a wrong password during the password input operation. ...
no. 2 example
[0046] Based on the above-mentioned embodiments of the present invention, this embodiment further provides a technical solution for obtaining verification information in a user identity verification method. In this technical solution, processing the verification text message to obtain the verification information includes: using a hash algorithm to obtain a data digest of the verification text message, and using the data digest as the verification information.
[0047] Specifically, processing the verification text message to obtain the verification information includes:
[0048] In S20, a hash algorithm is used to obtain a data digest of the verification text message, and the data digest is used as the verification information.
[0049] Specifically, after obtaining the verification text message sent by the verification server, the client uses a hash algorithm to perform hash transformation on the obtained verification text message, and uses the transformed result as the data...
no. 3 example
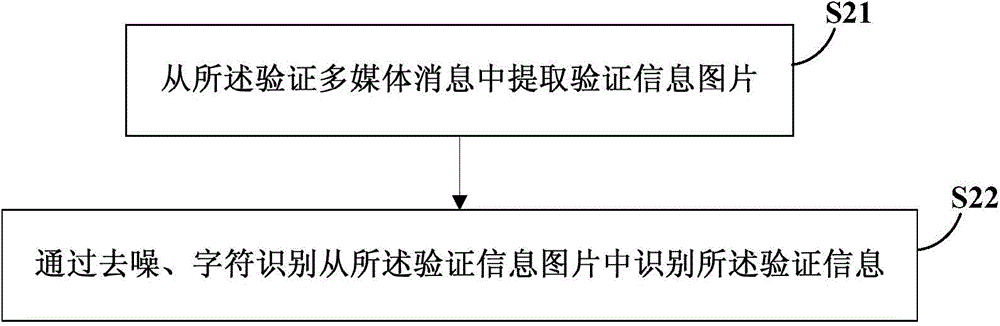
[0052] Based on the above-mentioned embodiments of the present invention, this embodiment further provides a technical solution for obtaining verification information in a user identity verification method. In this technical solution, extracting the verification information from the verification multimedia message includes: extracting the verification information picture from the verification multimedia message; identifying the verification information from the verification information picture through denoising and character recognition .
[0053] see figure 2 , in this embodiment, extracting the verification information from the verification multimedia message includes:
[0054] In S21, the verification information picture is extracted from the verification multimedia message.
[0055] The verification multimedia message includes a verification information picture. The verification information is displayed in the verification information picture. Therefore, to obtain the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com