Method and system for detecting credential stuffing attacks
A network access and path technology, applied in the field of network security, can solve problems such as user loss, achieve the effect of improving security and avoiding adverse consequences
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0034] Such as figure 1 As shown, the present invention provides a method for detecting credential stuffing attacks, the method comprising the following steps:
[0035] S11: The server receives the user's network access request and parses it to determine the source IP, destination IP, login attribute information and user information of the network access request. The user information includes user account number and password, and the login attribute information is the login that the network access request parses out path. Specifically, the network access request includes an HTTP request or an HTTPS request. If it is an HTTPS request, the client needs to preset a decryption certificate for the HTTPS request in the system to support the HTTPS decryption operation.
[0036] S12: The user configures a preset login path and a threshold of login times by himself. Specifically, the user can configure the preset login path by himself according to the configuration strategy, so that ...
Embodiment 2
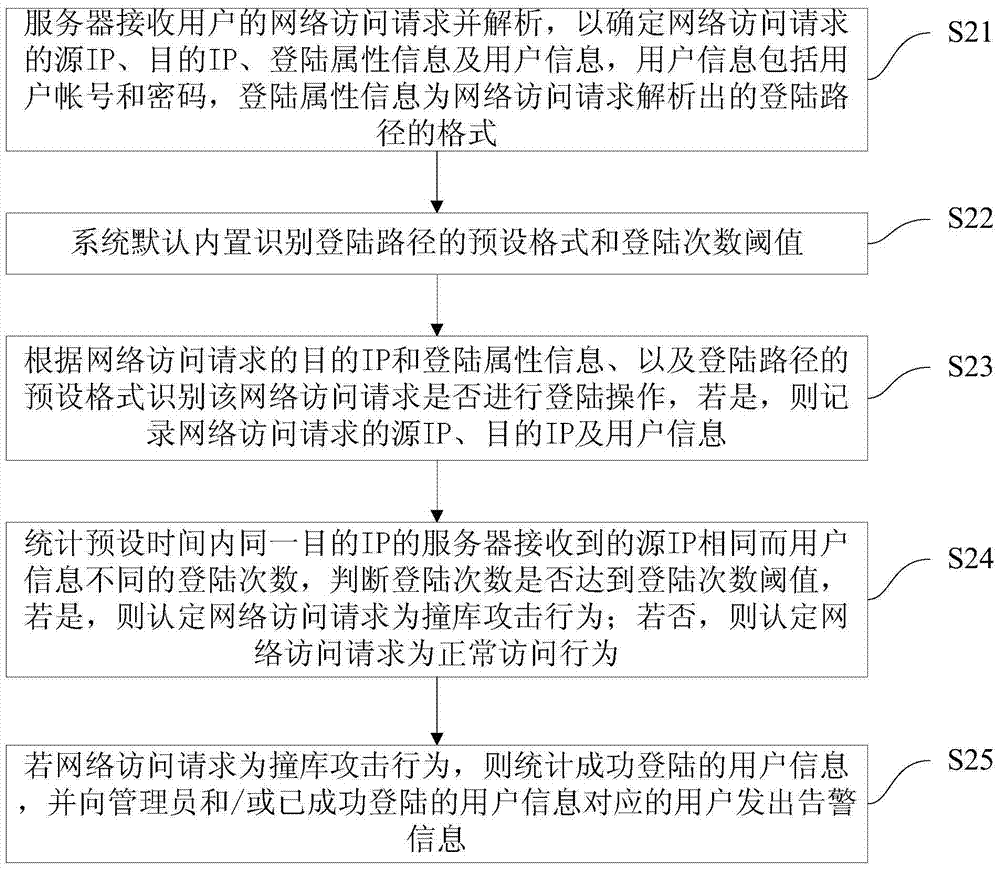
[0045] Such as figure 2 As shown, the present invention provides another method for detecting credential stuffing attacks, which method includes the following steps:
[0046] S21: The server receives the user's network access request and parses it to determine the source IP, destination IP, login attribute information and user information of the network access request. The user information includes user account number and password, and the login attribute information is the login that the network access request resolves. The format of the path. Specifically, the network access request includes an HTTP request or an HTTPS request. If it is an HTTPS request, the client needs to preset a decryption certificate for the HTTPS request in the system to support the HTTPS decryption operation.
[0047] S22: By default, the system has built-in preset formats for identifying login paths and thresholds for login times. Specifically, the user does not need to configure the default login...
Embodiment 3
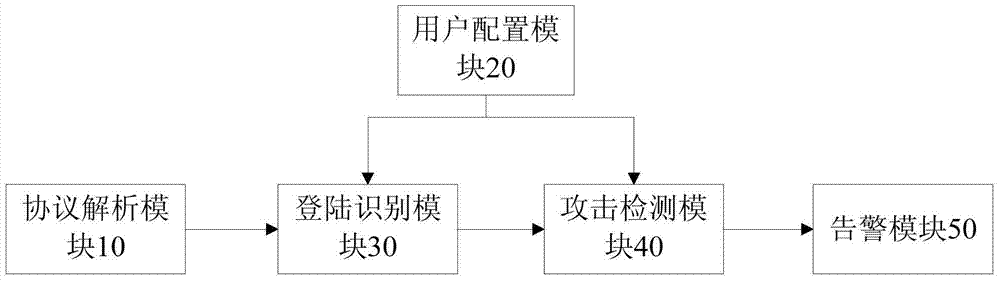
[0054] Such as image 3 As shown, the present invention also provides a system for detecting credential stuffing attacks, which includes:
[0055] The protocol analysis module 10 is used to receive and analyze the user's network access request to determine the source IP, destination IP, login attribute information and user information of the network access request. The user information includes user account number and password. Specifically, the network access request includes an HTTP request or an HTTPS request. If it is an HTTPS request, the client needs to preset a decryption certificate for the HTTPS request in the system to support the HTTPS decryption operation. Understandably, the login attribute information may be a login path or a format of a login path.
[0056] The user configuration module 20 can be used to configure the preset login path and the threshold of login times; the default format and the threshold of login times for identifying the login path can also b...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com