Active hiding method of router identity feature information
A technology of identity feature information and feature information, which is applied in the field of active hiding of router identity feature information, can solve problems such as router identity leakage, and achieve the effect of increasing the difficulty of identification.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
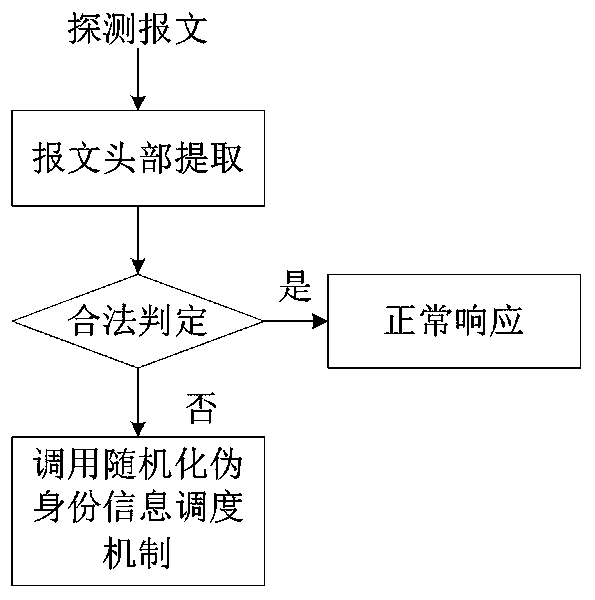
[0020] Embodiment one, see Figure 1~2 As shown, a method for actively hiding router identity feature information includes the following steps:
[0021] Step 1. Analyze the detected detection message to determine whether the detection message is legal. If it is a legal detection message, the router normally responds with correct characteristic information. Otherwise, determine that the detection message is an illegal detection message, and extract the illegal Detect message information, go to step 2;
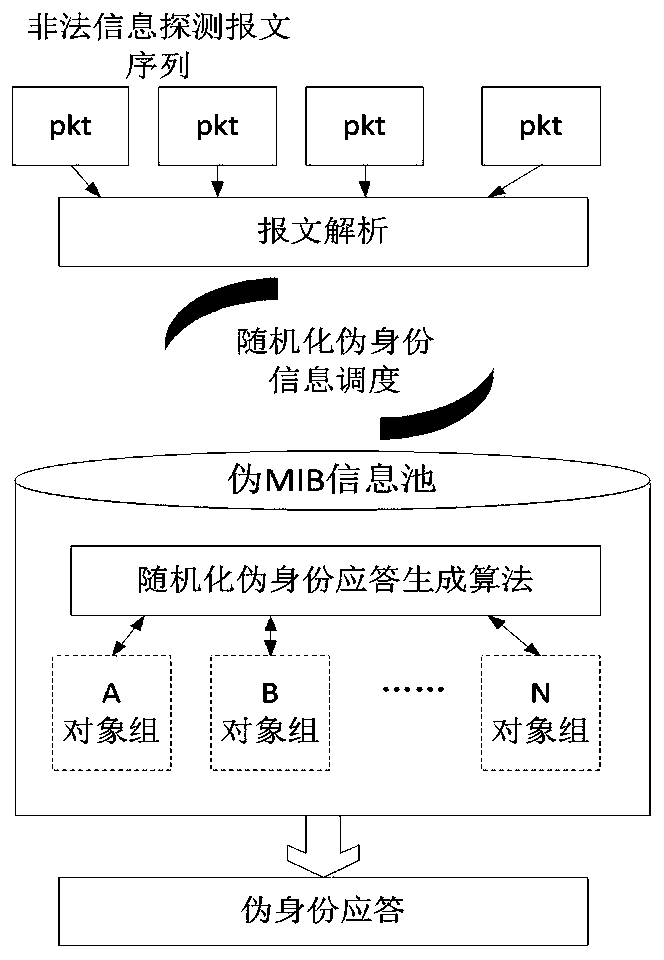
[0022] Step 2. For the illegal detection message information extracted in step 1, take randomization pseudo-identity response generation algorithm to generate corresponding pseudo-identity information, select the corresponding pseudo-identity information object group in the pseudo-MIB information pool;
[0023] Step 3. According to the pseudo-identity information generated in step 2, random and unpredictable pseudo-identity response information is dynamically generated through ...
Embodiment 2
[0025] Embodiment 2 is basically the same as Embodiment 1, except that the pseudo-MIB information pool is randomly generated in the router management plane according to the standard MIB tree structure, and responds to corresponding illegal detection messages according to pseudo-identity information .
Embodiment 3
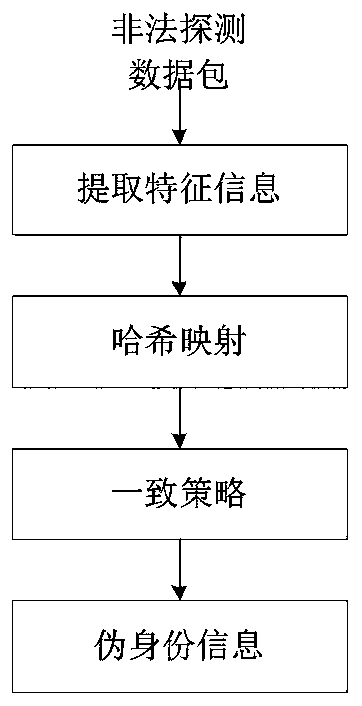
[0026] Embodiment 3 is basically the same as Embodiment 1, except that the extraction of illegal detection message information in step 1 includes extraction of feature information of illegal detection messages, and the feature information includes IP addresses and detection content features.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com