Trust management method based on backward inference
A trust management and trust value technology, applied in the field of trust management based on reverse reasoning, can solve the problems of poor recognition of fake nodes, reduce the probability of node whitewashing, and not consider fake entities, etc., to achieve guaranteed accuracy and accurate evaluation results , the effect of narrowing the difference
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0050] The present invention will be described in further detail below in conjunction with the accompanying drawings.
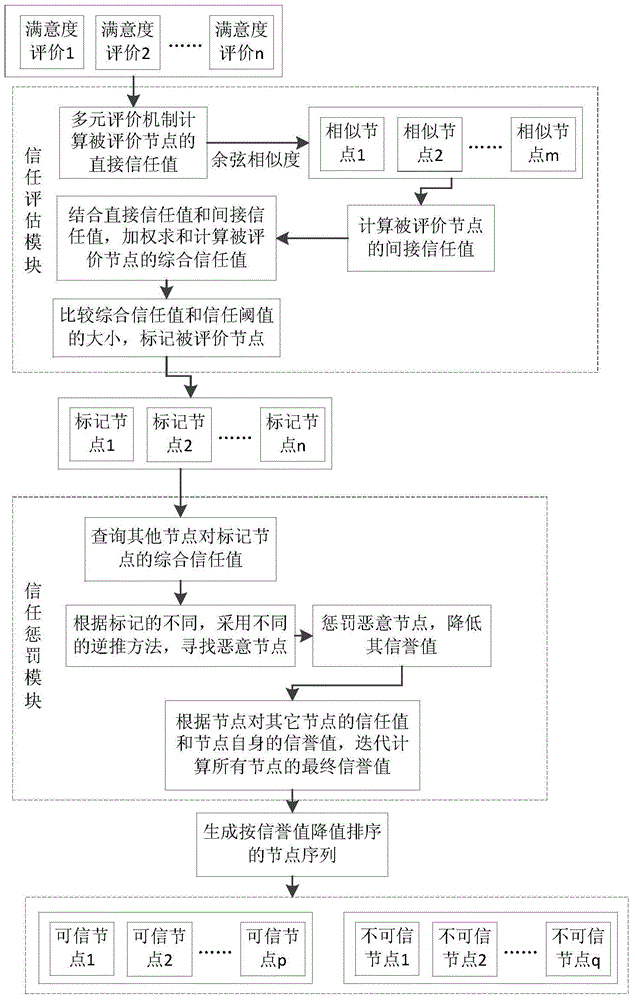
[0051] The trust management system and method based on reverse reasoning proposed by the present invention breaks through the traditional trust evaluation thinking, adopts reverse deduction thinking, and searches for malicious nodes in reverse according to the trust value of nodes. This method can effectively identify malicious nodes, especially those with deceptive behavior The masquerading nodes, and reduce their trust value, prevent malicious nodes and masquerading nodes from deceiving other nodes, thereby ensuring the security of the network.
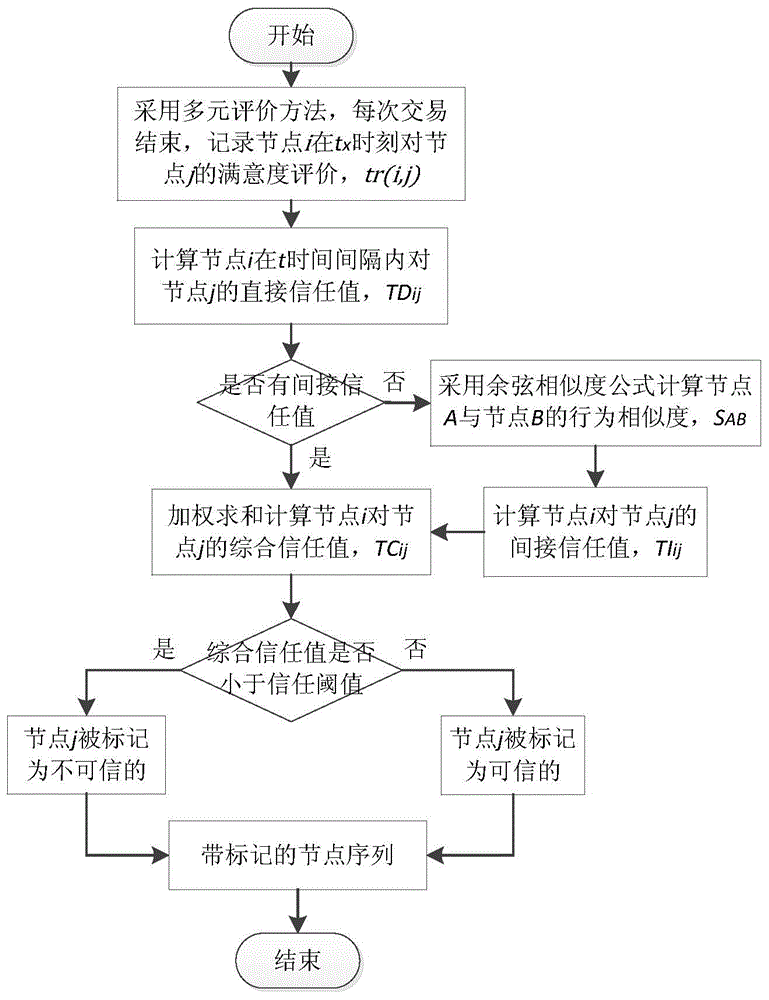
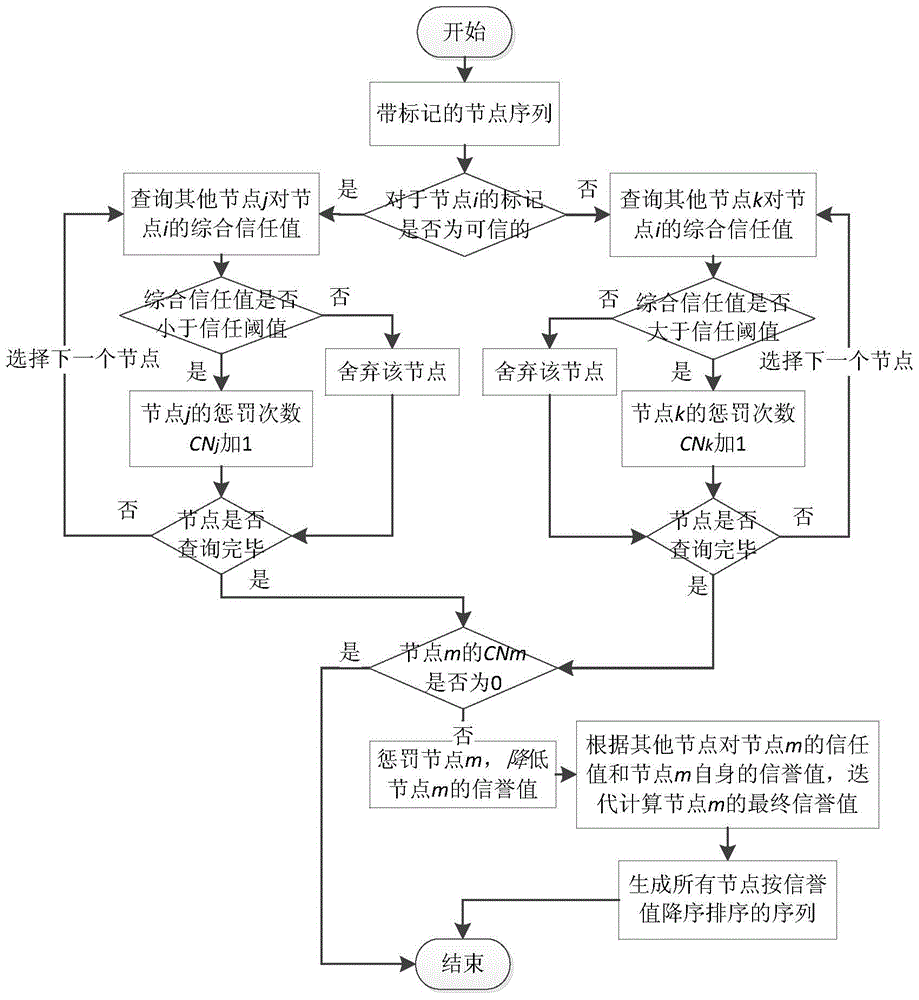
[0052] The model proposed by the present invention is divided into a trust evaluation module and a trust penalty module, such as figure 1 shown. 1) For the trust evaluation module, the satisfaction evaluation between nodes is generated through inter-node transactions, and the direct trust value of the evaluated no...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com