Verification method, device and system of transmitted data
A technology for transmitting data and verifying methods, which is applied in the computer field and can solve problems such as the inability to reduce the risk of file transmission errors
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0021] Before describing further details of the various embodiments of the present application, reference will be made to figure 1 to describe one suitable computing architecture that can be used to implement the principles of the present application. In the following description, unless indicated otherwise, various embodiments of the present application are described with reference to acts and symbolic representations of operations that are performed by one or more computers. It will thus be appreciated that such acts and operations, which are sometimes referred to as computer-implemented, include the manipulation of electrical signals representing data in a structured form by the processing unit of a computer. This manipulation transforms the data or maintains it at a location in the computer's memory system, which reconfigures or changes the operation of the computer in a manner well understood by those skilled in the art. A data structure that maintains data is a physical...
Embodiment approach
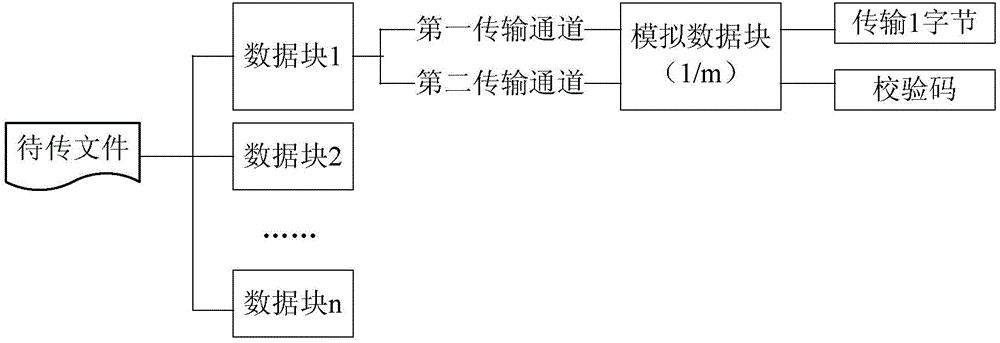
[0042] First, the receiving client reads the currently received data segment and the storage space value corresponding to the currently received data segment.
[0043] Then, after creating a verification storage space according to the storage space value corresponding to the currently received data segment, save the currently received data segment to the verification storage space, and generate a received file corresponding to the currently received data segment.
[0044] Finally, a predetermined verification algorithm is used to perform verification processing on the received file, and a verification value corresponding to the currently received data segment is generated.
[0045] It can be seen from the above solution that in an optional embodiment provided by the present application, since the sending client will store the current data segment after saving the currently transmitted data segment among the n data segments in the preset storage space The storage space of the s...
Embodiment 2
[0048] According to an embodiment of the present invention, a method embodiment for implementing the above-mentioned system embodiment is also provided. It should be noted that the steps shown in the flow charts of the drawings can be implemented in a computer system such as a set of computer-executable instructions and, although a logical order is shown in the flowcharts, in some cases the steps shown or described may be performed in an order different from that shown or described herein.
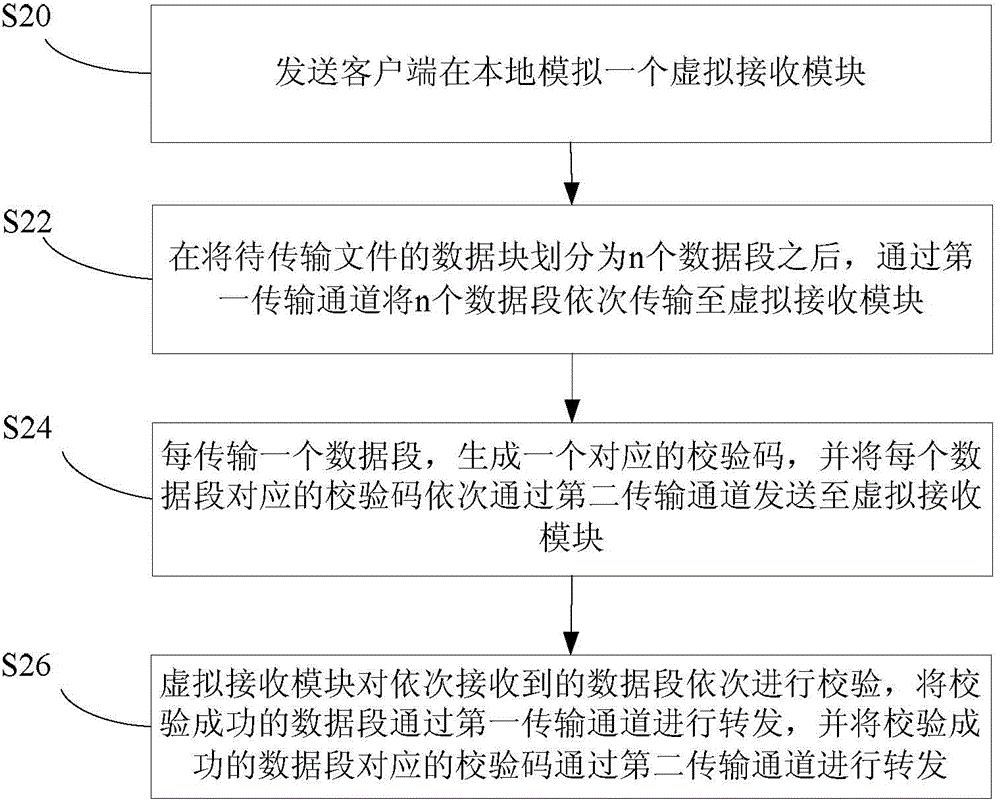
[0049] figure 2 is a schematic flowchart of a method for verifying transmission data according to Embodiment 2 of the present invention.
[0050] Such as figure 2 As shown, the verification method of the transmitted data may include the following implementation steps:
[0051] Step S20, the sending client locally simulates a virtual receiving module. This step realizes the automatic creation of a virtual receiving module on the sending client to verify whether the local network connec...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com