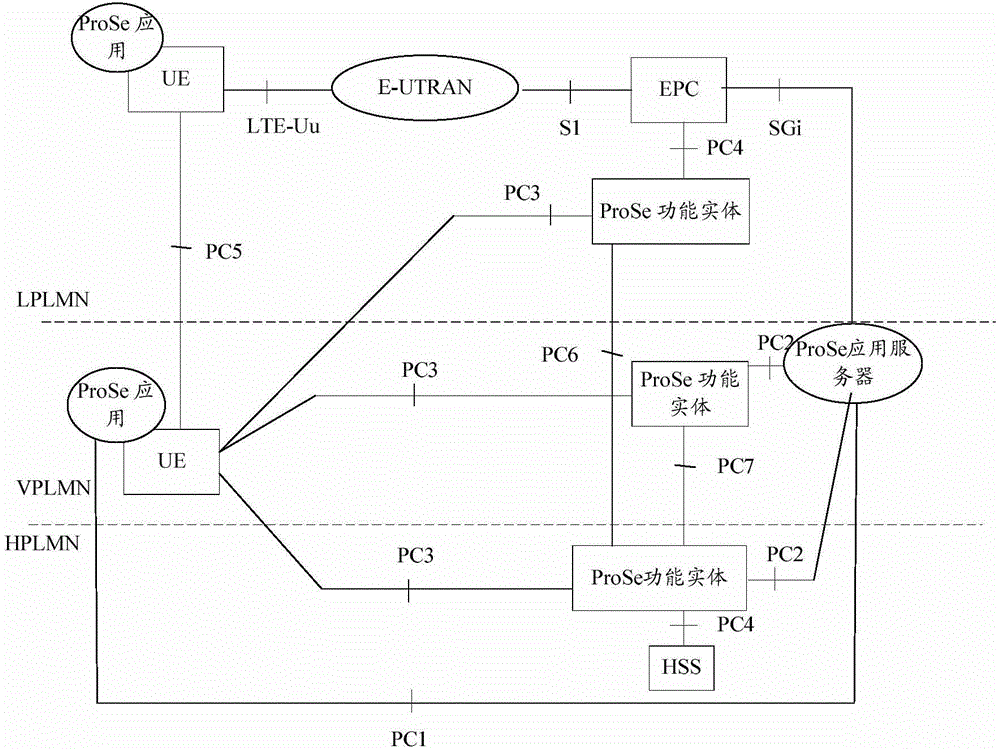
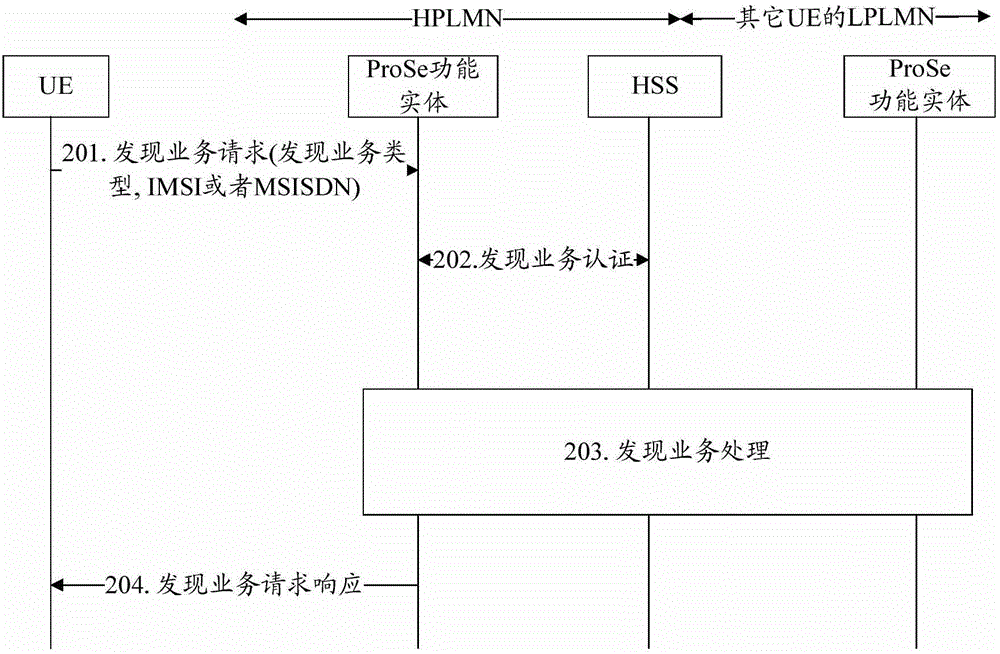
Authentication method and system, ProSe (Proximity-based Service) functional entities and UE (User Equipment)
A technology of functional entities and authentication methods, applied in short-distance communication services, security devices, electrical components, etc., can solve problems such as exposure of user privacy information, increasing the risk of users being attacked by attackers, and business request errors.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
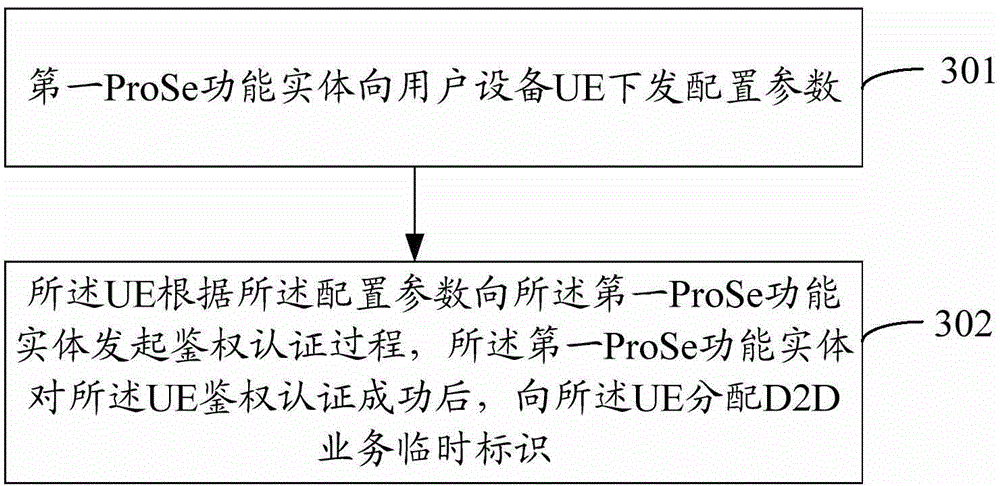
[0124] Embodiment 1 of the present invention provides an authentication authentication method, such as image 3 As shown, the method includes the following steps:
[0125] Step 301: the first ProSe functional entity sends configuration parameters to the UE;
[0126] The first ProSe functional entity here refers to the ProSe functional entity under the HPLMN of the UE. After the UE establishes a secure connection with the first ProSe functional entity, the UE sends a discovery service request message to the first ProSe functional entity;
[0127] The first ProSe functional entity sends configuration parameters to the UE, the configuration parameters include: a list of PLMN identities supported by the UE and the D2D service temporary identifier allocated for the UE by the first ProSe functional entity, or the configuration parameters only include A list of PLMN identifiers supported by the UE;
[0128] When the configuration parameters delivered to the UE include: a list of PLMN...
Embodiment 2
[0197] Embodiment 2 of the present invention provides an authentication authentication method, the method flow Figure 7 As shown, the method includes the following steps:
[0198] Step 701: the first ProSe functional entity sends configuration parameters to the UE;
[0199] Specifically, the configuration parameters issued by the first ProSe functional entity to the UE may include a list of PLMN identities supported by the UE and the temporary D2D service identifier allocated to the UE by the first ProSe functional entity, or the configuration parameters may only include the A list of PLMN identifiers supported by the UE;
[0200] Wherein, the D2D service temporary identifier may be a ProSe functional entity identifier or a parameter uniquely corresponding to the UE, and the parameter may adopt any representation form that can be used to uniquely identify a UE; specifically, in the actual distribution of the D2D service temporary identifier In , the parameters can be assign...
Embodiment 3
[0218] Embodiment 3 of the present invention provides an authentication method, the flow chart of the method is as follows Figure 8 As shown, the method includes the following steps:
[0219] Step 801: UE receives the configuration parameters issued by the first ProSe functional entity;
[0220] Specifically, the configuration parameters include a list of PLMN identities supported by the UE and the D2D service temporary identities allocated to the UE by the ProSe functional entity, or the configuration parameters only include a list of PLMN identities supported by the UE;
[0221] Wherein, the D2D service temporary identifier may be a ProSe functional entity identifier or a parameter uniquely corresponding to the UE, and the parameter may adopt any representation form that can be used to uniquely identify a UE; specifically, in the actual distribution of the D2D service temporary identifier In , the parameters can be assigned to the UE sequentially or randomly assigned to th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com