Method for identifying permission-irrelevant private data in Android application program
An Android application, privacy data technology, applied in the fields of digital data protection, electronic digital data processing, semi-structured data retrieval, etc., can solve problems such as inability to detect and analyze, and achieve the effect of low resource consumption and fast speed
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
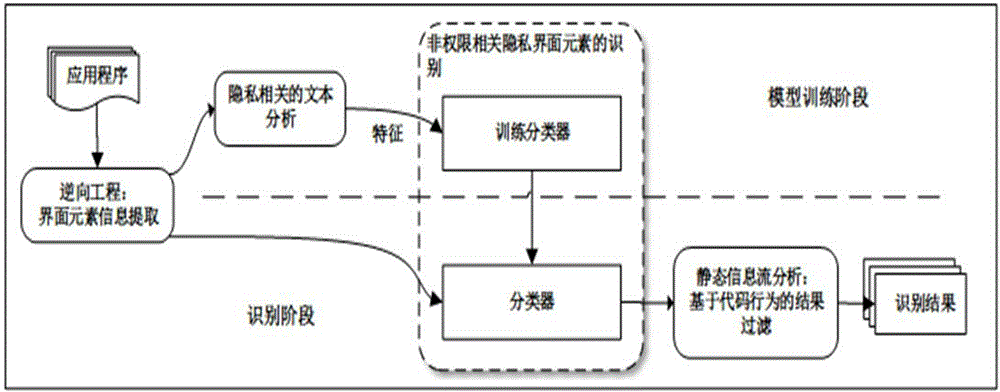
[0061] The present invention designs and implements the above-mentioned non-privacy detection system based on machine learning technology and static information flow analysis technology. This section makes a detailed introduction to the specific implementation of the framework.
[0062] (1) Data preprocessing
[0063] The present invention adopts Apktool to carry out reverse engineering to the Android application program, and Apktool is the Android application program compiling software provided by Google, which can decompile the application program, and can obtain various resource files inside the application program during decompilation. The integrity of the file is guaranteed. Therefore, the present invention selects it to realize the resource file extraction module.
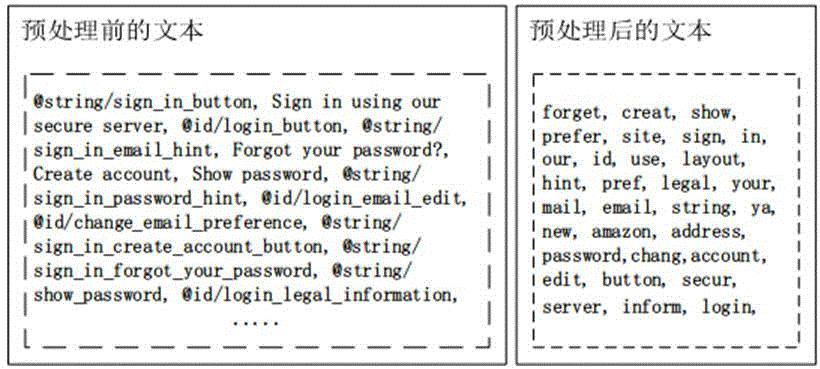
[0064] For the resource file after extraction, the present invention uses the NLTK toolkit of Python to carry out text preprocessing to it. The NLTK toolkit is one of the most commonly used toolkits in na...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com