Terminal authentication method, device and system
A terminal and authentication technology, applied in the Internet field, can solve problems such as insufficient intelligence in authentication operations, and achieve the effect of improving intelligence
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
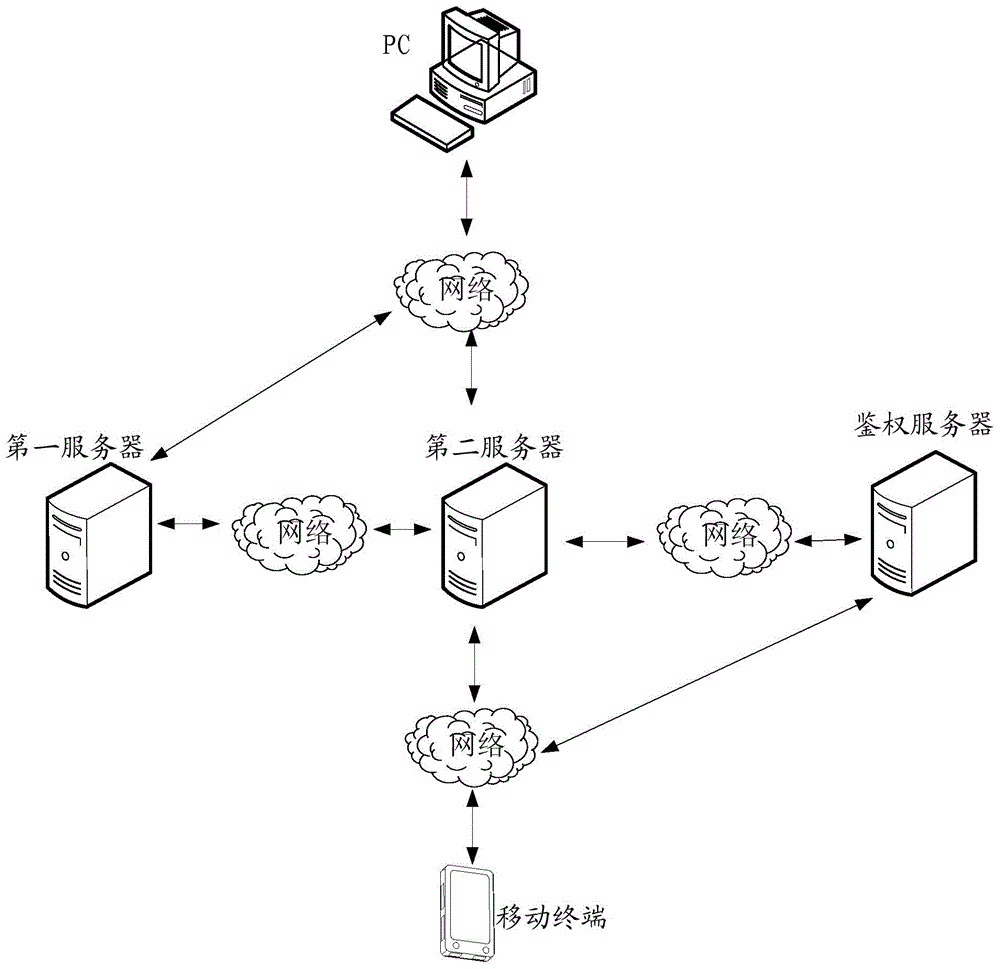
[0050] Such as image 3 As shown, a first embodiment of a terminal authentication method of the present invention is proposed, and the terminal authentication method includes:
[0051] Step S10, when receiving an authentication event triggered based on a preset application, the first terminal acquires authentication information from the first server based on the user identification information corresponding to the preset application;
[0052] In this embodiment, the preset application can be an application run by the first terminal simulating a mobile device, or some application specially developed for the second terminal, or an application run by the first terminal in the state of mobile communication. Authorization events can be operations such as login and payment. The user's identification information may be the login information used by the user to log in to the application, such as the user's login account; or, the ID information preset by the user. Multiple sets of us...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap