Public audit method with privacy protection in data shared by multi-manager groups
A data sharing and privacy protection technology, applied in the field of cloud storage and information security, can solve the problems of malicious users covering up and innocent users being framed, and achieve the effects of eliminating potential safety hazards, ensuring unframing, and realizing traceability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
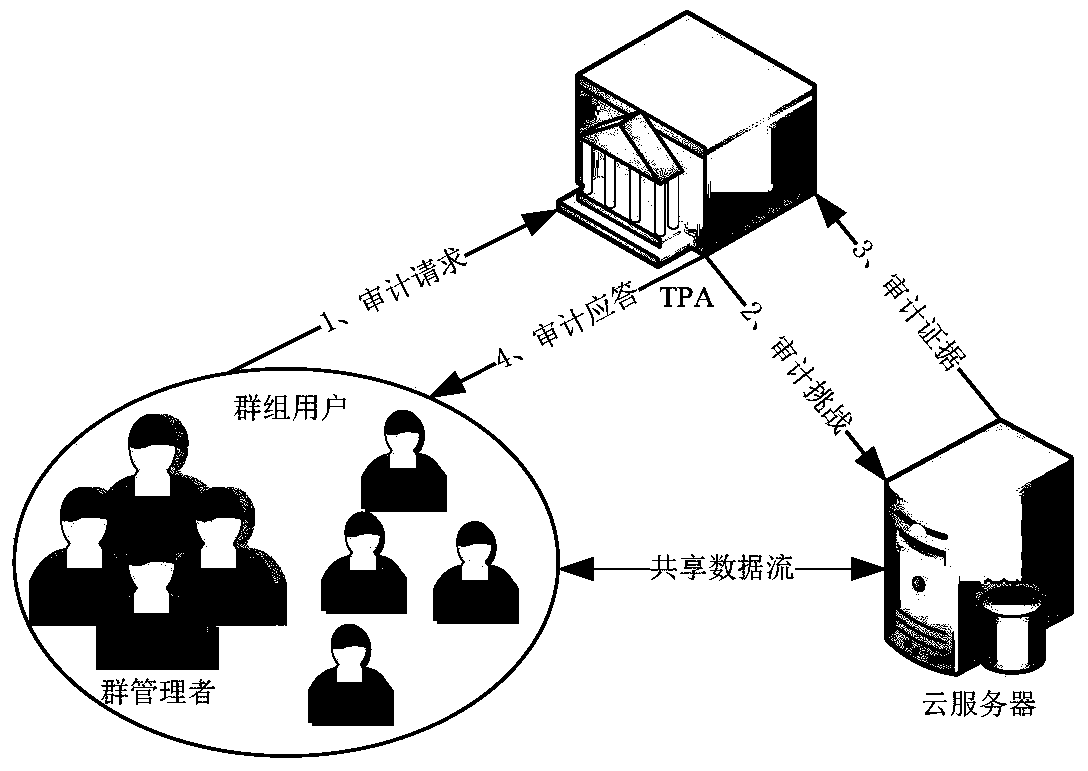
[0036] The system model of the inventive method is as figure 1 As shown, there are three types of entities: cloud server, third party auditor TPA (the Third Party Auditor) and group users, and group users include multiple group managers GMs (GroupManagers) and some ordinary users U. When the user needs to check the integrity of the shared data, the user sends an audit request to the TPA, and then the TPA sends an audit challenge message to the cloud server. After the cloud server receives the challenge, it will generate audit evidence and return it to TPA. TPA then verifies the correctness of the audit evidence and returns the audit results to the user.
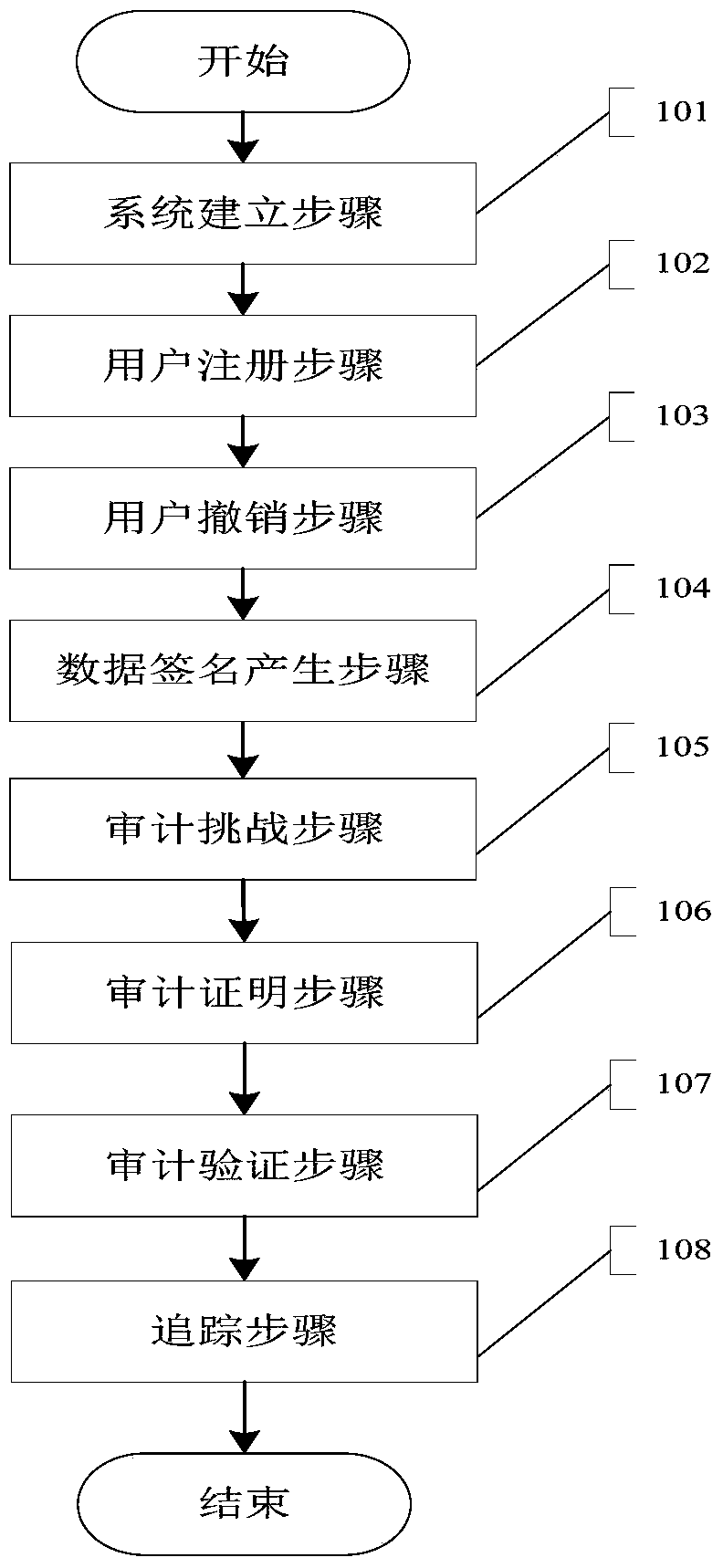
[0037] The public audit method with privacy protection in the multi-manager group shared data of the present invention can support the multi-manager group user model, while ensuring the integrity of outsourced data, it can realize the identity privacy protection of group users, when it is necessary to track When the identit...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com