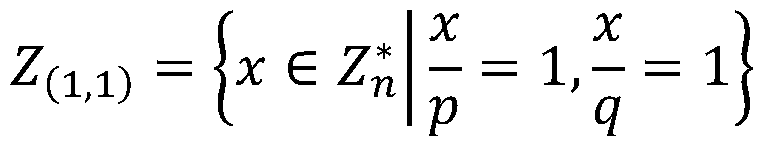Data Encryption Method Based on Double Difficulty
A data encryption and encryption algorithm technology, applied in key distribution, can solve the problems of slow encryption and decryption speed, and achieve the effect of ensuring correctness and integrity, good security and practical application value
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
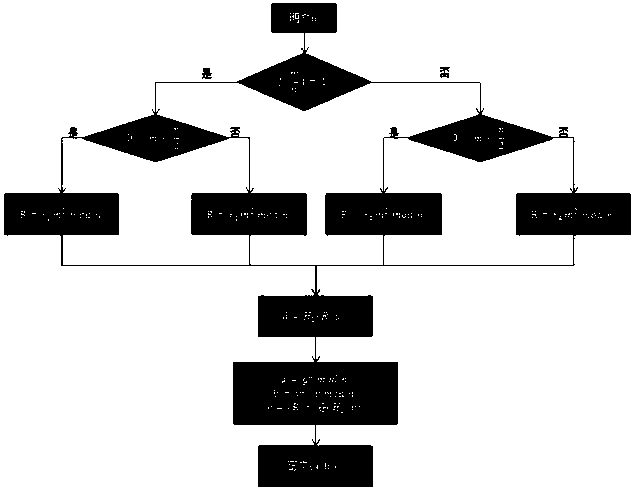
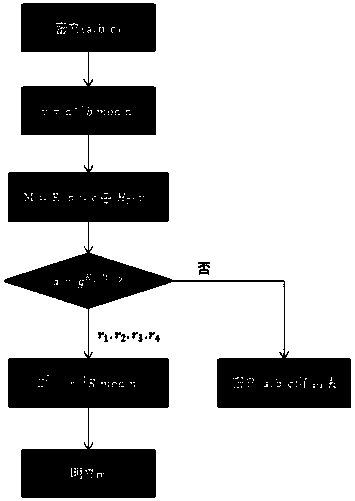
[0042] Below with reference to accompanying drawing, further illustrate the present invention.
[0043] The data encryption method based on double difficulty of the present invention, comprises the steps:
[0044] Step 1, initialization; first select a security parameter L, and input the L-bit parameter into the generating function F(·) generating function F(1 L ) to generate Enc and Dec two algorithms, which are the encryption algorithm and the decryption algorithm respectively, and the parameters used are generated in the following way:
[0045]Step11 Let n be a Williams integer, n=p×q, where p=3 mod 8, q=7 mod 8, and p=2p'+1, q=2q'+1, the length is Among them, p, q, p' and q' are all large prime numbers, and |n|=k represents the bit length of n;
[0046] Step12 Let G= be the multiplicative group The largest cyclic subgroup, g is the generator of the cyclic subgroup, the rank λ(n)=lcm(p-1,q-1)=2p'q' of G is the Carmichael's function, is defined as follows;
[0047] S...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com