A Wireless Router with Malware Network Behavior Discovery Capabilities
A wireless router and malware technology, applied in wireless communication, data exchange network, network traffic/resource management, etc., can solve the problems of high resource consumption of user terminals, stay in the academic research stage, difficult to deploy and implement on a large scale, etc. The effect of resolving deployment difficulties
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0043] The present invention is described in detail below in conjunction with accompanying drawing:
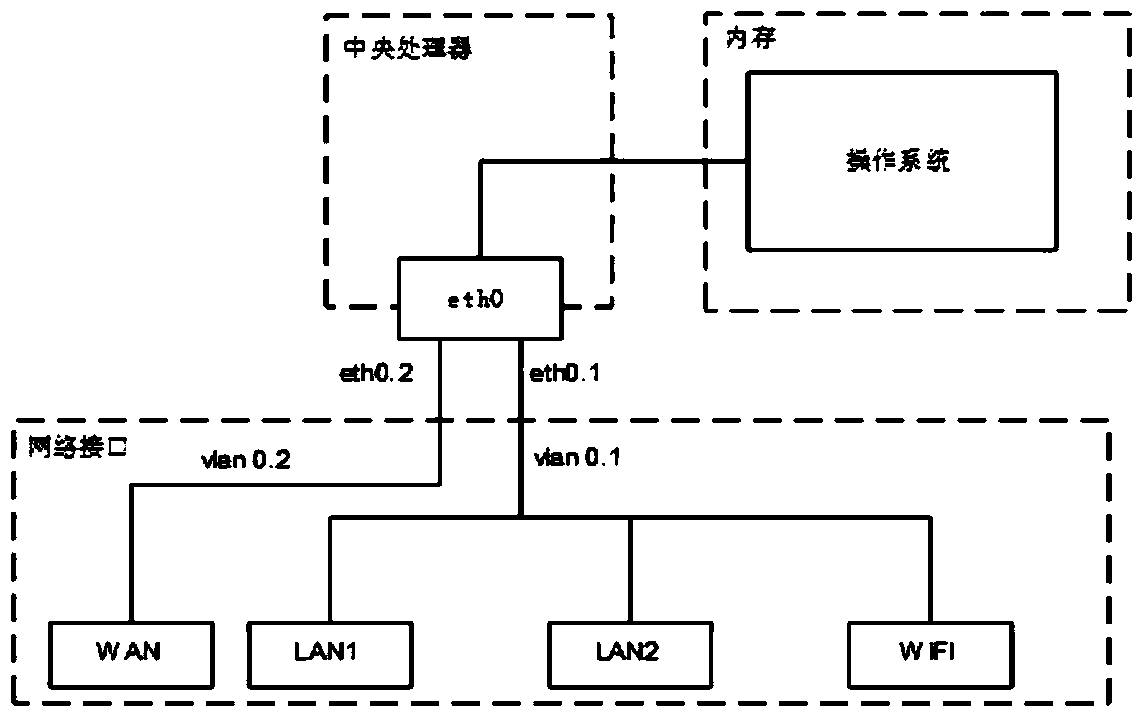
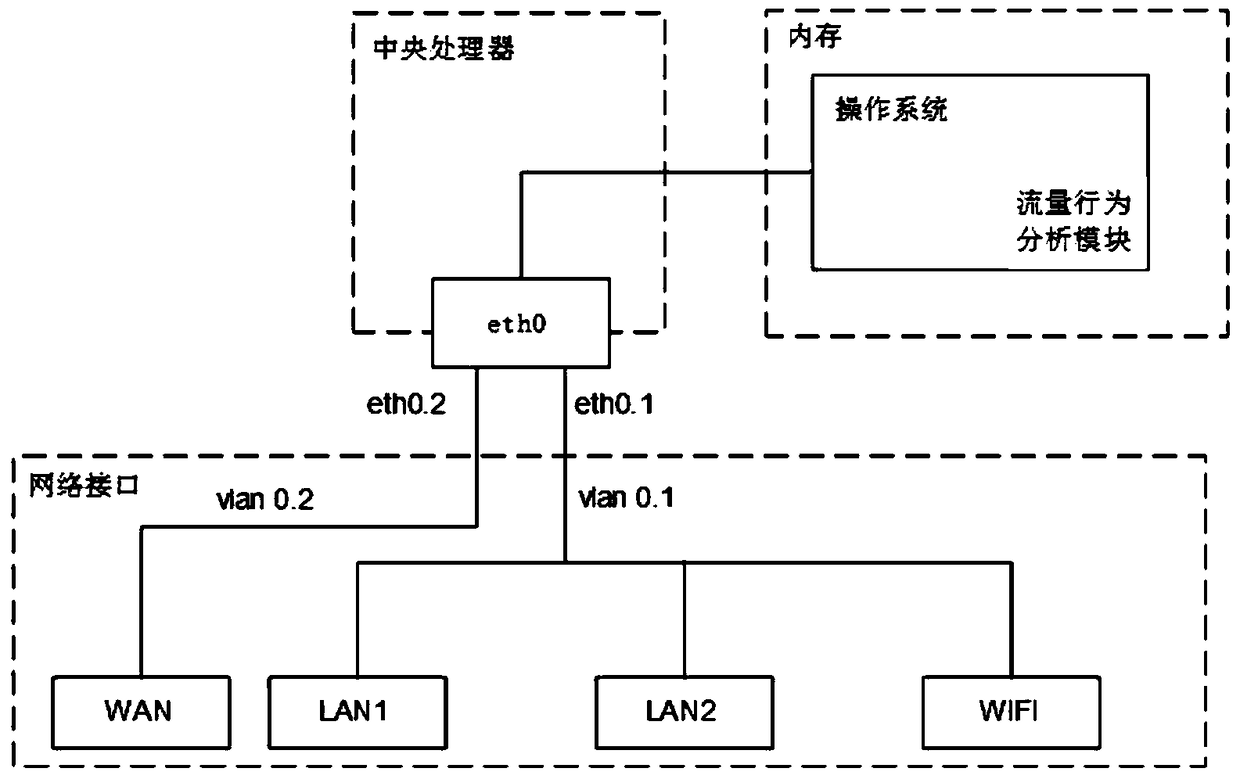
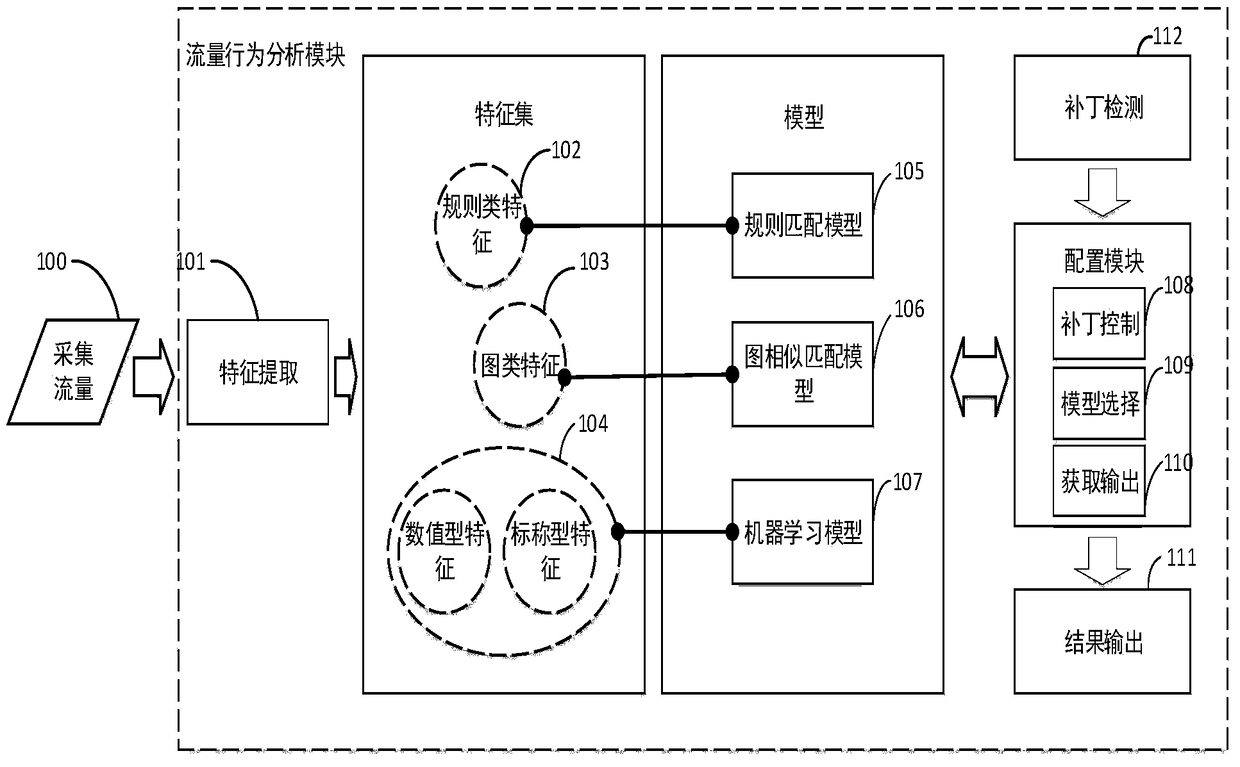
[0044] The present invention uses the structure of the original wireless router (such as figure 1 shown) as the basis, a traffic behavior analysis module is added to the operating system (such as figure 2 shown). First, when the user's mobile terminal accesses the external network through a router, use the tcpdump tool installed in the router system to collect the interactive traffic between the user's mobile terminal device and the external network; then, the behavior analysis module reads the collected network traffic and analyze it; finally, if malicious traffic is detected, it means that a malicious application is installed on the user's mobile terminal device, and the detection result is fed back to the user through a prompt message.
[0045] A wireless router capable of discovering malicious software network behavior, it should include:
[0046] The traffic acquisiti...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com