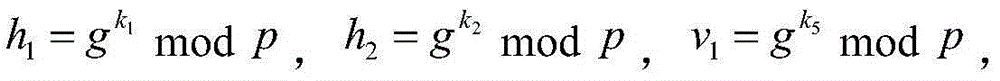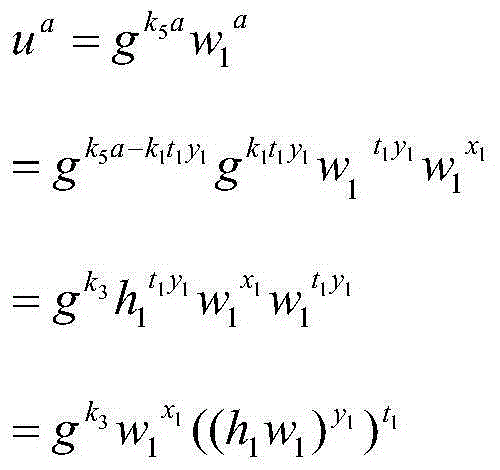Safe mode index outsourcing method and system under single malicious cloud server
A cloud server, modular index technology, applied in the field of cloud computing, can solve problems such as low verifiability and inability to find lazy servers to deceive users.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0031] The specific implementation manner of the present invention will be described in detail below in conjunction with the accompanying drawings.
[0032] Suppose p, q are two large prime numbers, q|p-1, and u q = 1modp, giving an arbitrary exponent and base calculate u a modp, which requires the values of a and u to be kept secret from U during the outsourced computation. This is a requirement of the security model index outsourcing method, which belongs to the existing general requirements, and will not be described in detail here.
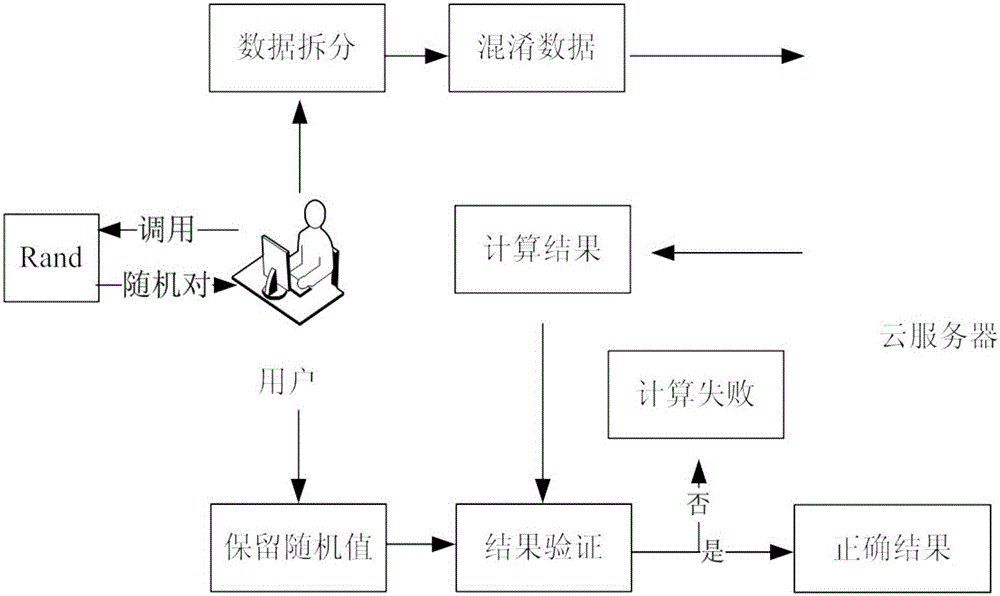
[0033] Such as figure 1 A schematic diagram of the system architecture of the outsourcing modulo index method of the present invention is shown. There are three participating parties in the present invention: the subroutine Rand, the user T, and the malicious cloud server U.
[0034] Subroutine Rand: Each call can honestly return a form (k,g k ), the computational efficiency can be improved by calling Rand.
[0035] Malicious cloud...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com