Implementation method for safely managing intranet terminal
A technology of terminal security and implementation method, applied in the direction of platform integrity maintenance, etc., to achieve the effect of easy promotion and strong practicability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0039] The present invention will be further described below in conjunction with the accompanying drawings and specific embodiments.
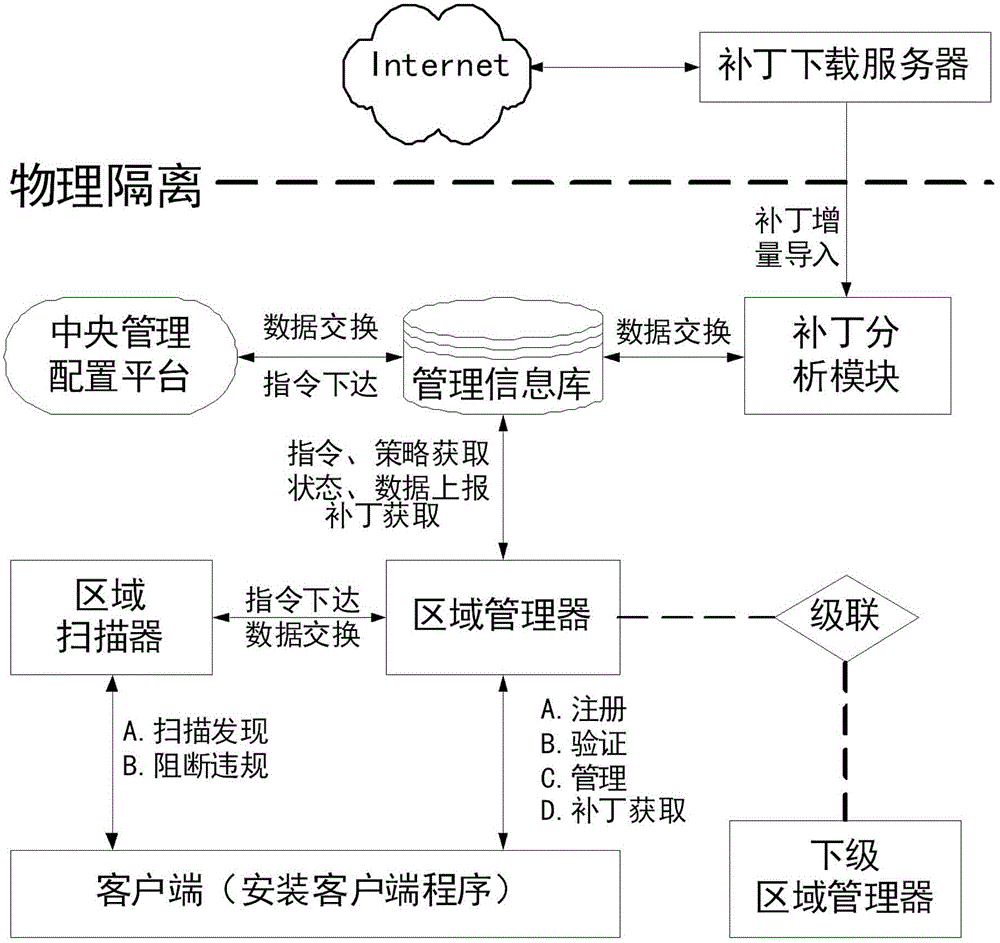
[0040] The present invention provides a method for implementing security management of intranet terminals, as shown in the attached figure 1 As shown, the specific implementation process is:
[0041] Design ten modules of terminal basic management, asset management, terminal desktop management, terminal security management, host operation and maintenance, patch distribution, security monitoring and auditing, report management, event alarm management, and third-party interface management to realize the controllable management of internal network terminals .
[0042] Furthermore, the structure and implementation process of the above ten modules are now described in detail:
[0043] 1. Terminal basic management module.
[0044]Terminal registration management. The system adopts the management method combining C / S and B / S modes, including clien...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com