Distributed abnormal detection method for network data stream
An anomaly detection and data flow technology, applied in the network field, can solve problems such as large amount of calculation, large amount of data, and consumption
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0069] The present invention will be further described below in conjunction with the accompanying drawings and embodiments.
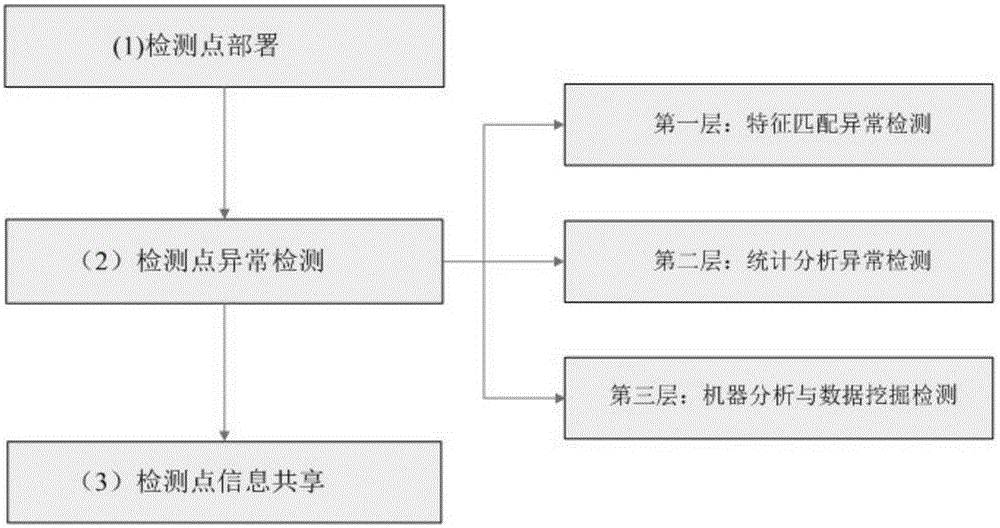
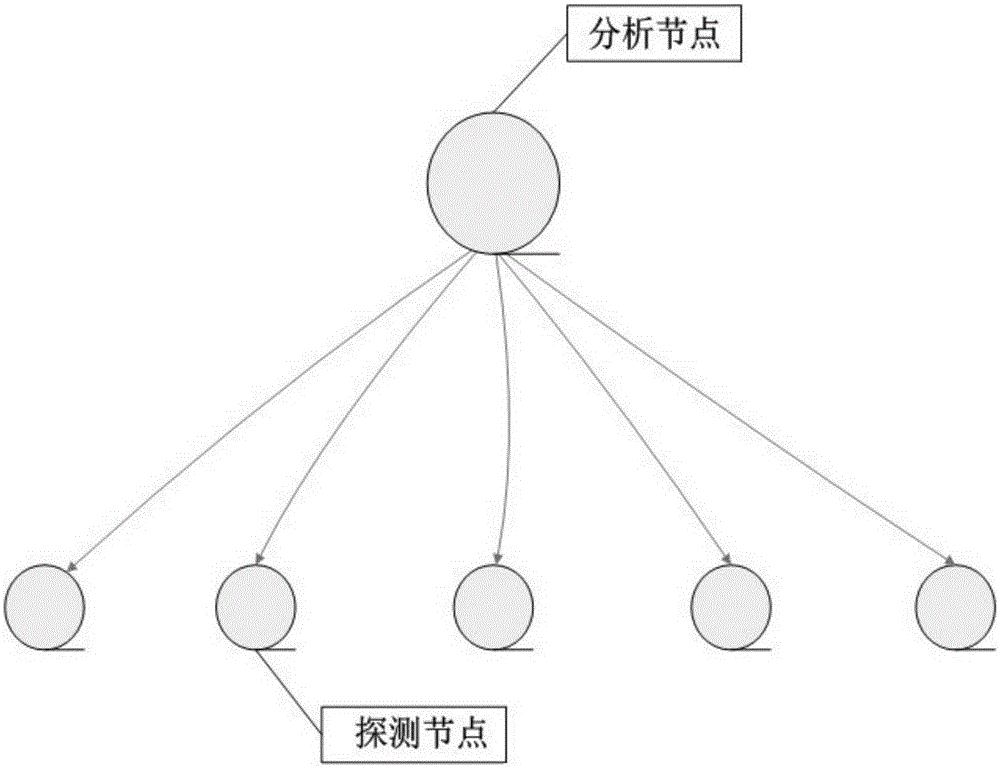
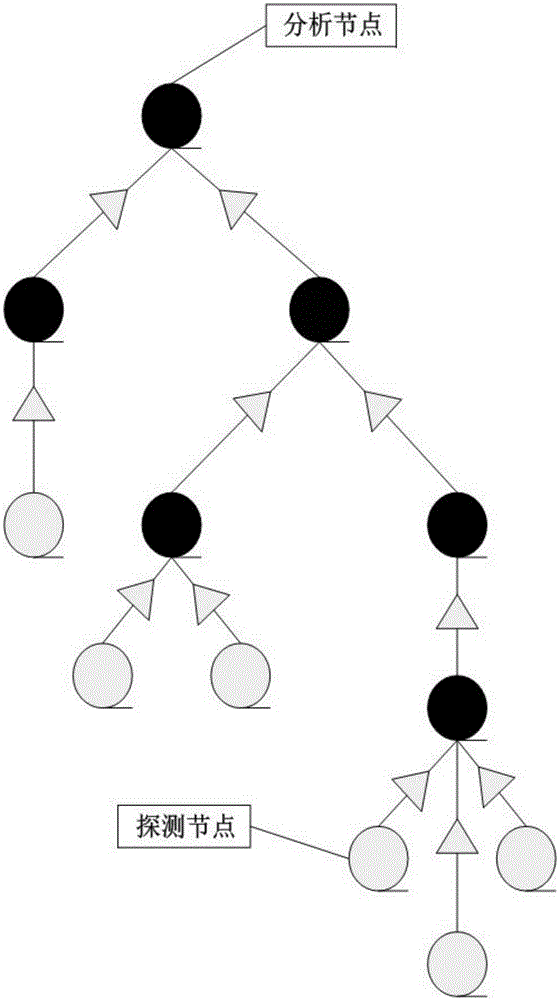
[0070] This embodiment provides a method for distributed anomaly detection network data flow, such as figure 1 , figure 2 and image 3 As shown, it specifically includes the following steps:
[0071] Step S1: Deploy N detection points: set a node of the connection interface between the terminal equipment and the network as a normal node, and the detection point is independent of the normal node; the detection point is connected to the normal node Each detection point monitors an ordinary node to detect abnormal data packets sent by terminal equipment at ordinary nodes and prevent the terminal from receiving abnormal data packets in the network;
[0072] Step S2: Detection points monitor abnormal network data streams: three detection methods are used for hierarchical anomaly detection, the first layer detection adopts the anomaly detection method ba...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com