User authentication method and device
A technology for authenticating users and users, applied in the field of communications, can solve problems such as user terminal poisoning and untrustworthy users, and achieve the effect of improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
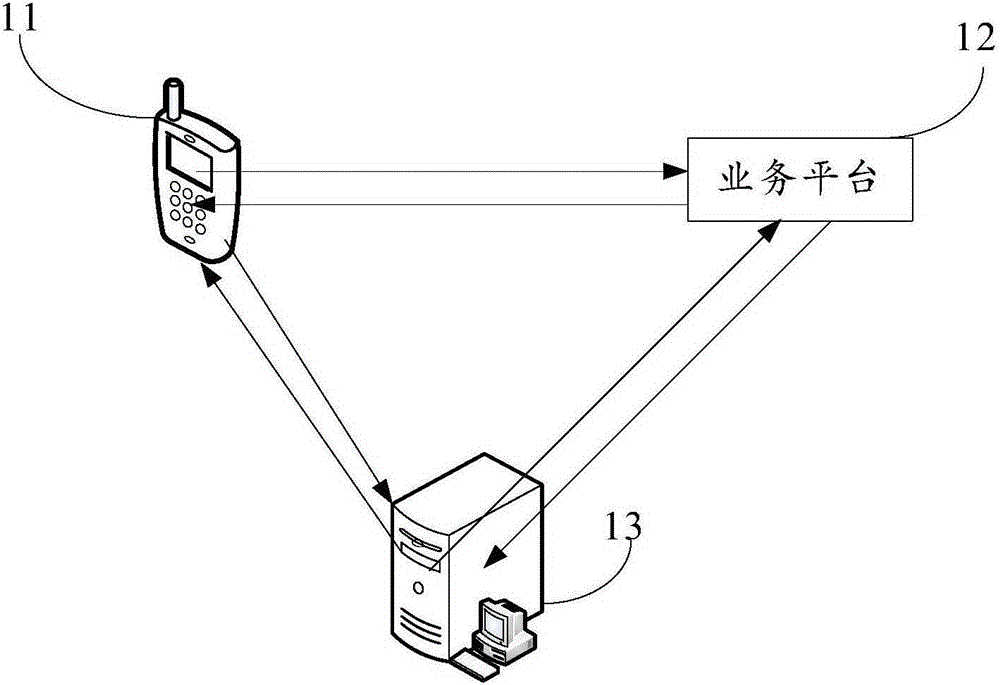
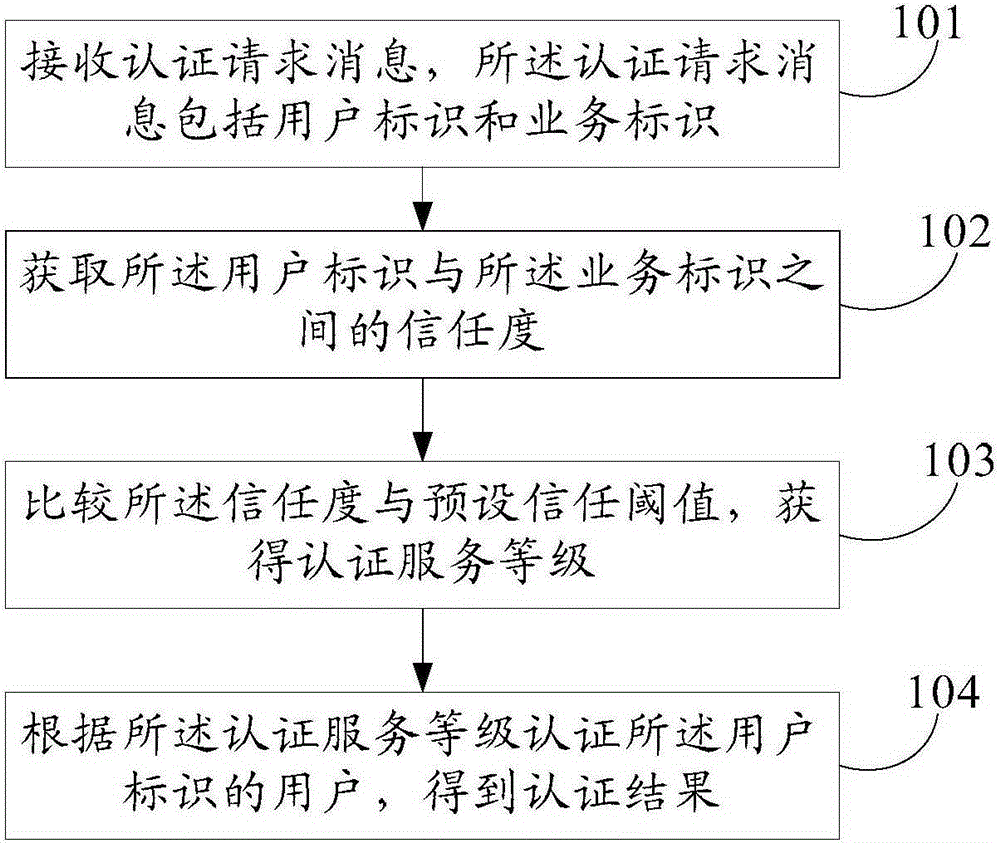
[0038] An embodiment of the present invention provides a method for authenticating a user, which is applied to an authentication user device, such as image 3 shown, including:
[0039] Step 101. Receive an authentication request message, where the authentication request message includes a user identifier and a service identifier.
[0040] Step 102, acquiring the trust degree between the user identifier and the service identifier.
[0041] Step 103, comparing the trust degree with a preset trust threshold to obtain an authentication service level.
[0042] Step 104: Authenticate the user identified by the user according to the authentication service level, and obtain an authentication result.
[0043]After receiving the authentication request message including the user ID and the service ID, firstly, obtain the trust degree between the user ID and the service ID; then, compare the trust degree with the preset trust threshold to obtain the authentication service level ; Fina...
Embodiment 2
[0045] An embodiment of the present invention provides a method for authenticating a user, such as Figure 4 shown, including:
[0046] Step 201, the user terminal sends an access request message to the service platform.
[0047] The access request message includes user identification, access time and so on. The user identifier is a unique identifier of the user identity, which may be the user's mobile phone number.
[0048] Step 202, the service platform sends an authentication request message to the authentication user device.
[0049] The authentication request message includes user identification and service identification. The service identifier is a service identifier corresponding to the service accessed by the user.
[0050] Step 203, the authenticated user device judges whether to store the service identifier in advance.
[0051] If the service identifier is not pre-stored, step 204 is performed.
[0052] If the service identifier is stored in advance, step 206 ...
Embodiment 3
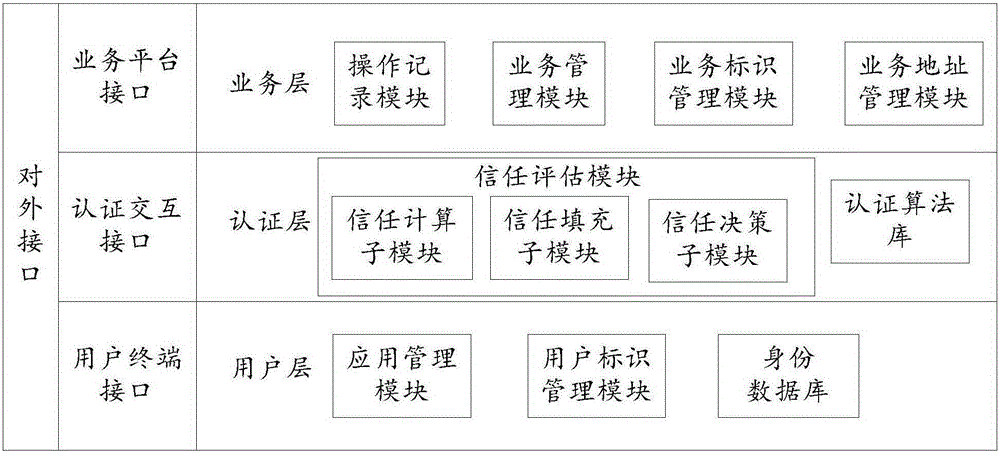
[0112] An embodiment of the present invention provides an authentication user device 30, such as Figure 6 shown, including:
[0113] A receiving unit 301, configured to receive an authentication request message, where the authentication request message includes a user identifier and a service identifier;
[0114] A processing unit 302, configured to obtain the degree of trust between the user identifier and the service identifier;
[0115] The processing unit 302 is further configured to compare the trust degree with a preset trust threshold to obtain an authentication service level;
[0116] The processing unit 302 is further configured to authenticate the user identified by the user according to the authentication service level, and obtain an authentication result.
[0117] Compared with the existing technology, which only performs identity verification based on the user name and login password provided by the user, the present invention dynamically authenticates the user...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com