Anti-copy method for embedded device program
An embedded device and anti-copy technology, applied in the direction of program/content distribution protection, etc., can solve problems such as cumbersome implementation process and complex algorithm
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0021] The specific embodiments of the present invention will be further described below in conjunction with the accompanying drawings.
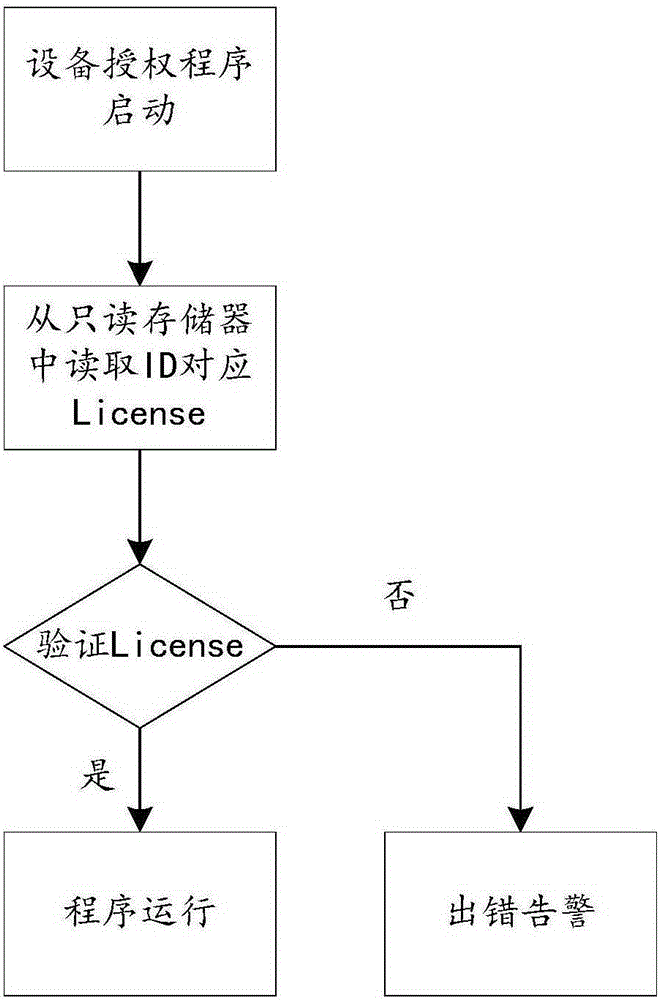
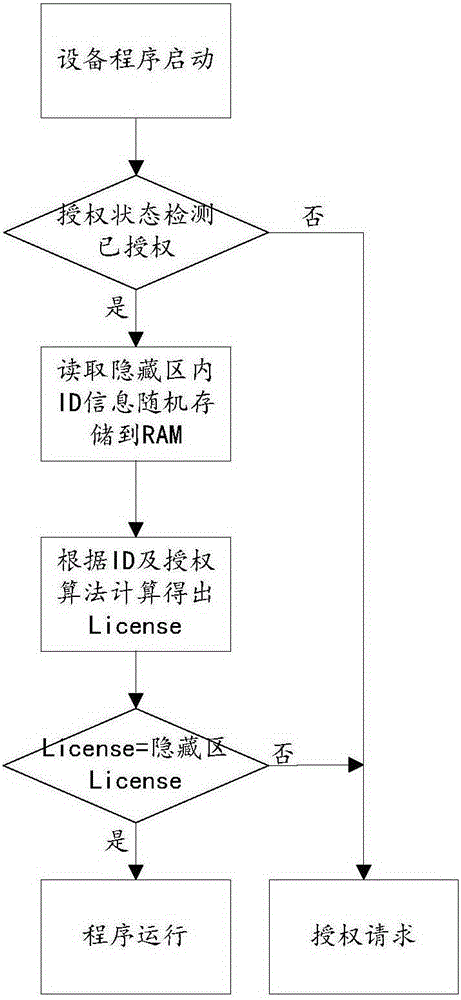
[0022] The anti-copy method of the embedded device program proposed by the present invention stores ID and License information in a hidden area, protects it, and enters the hidden area after the device program is authorized and confirmed, reads the device ID to the RAM area, and in the RAM area , combine the ID offset information and the authorization algorithm to calculate the license, and finally compare the calculated license with the license in the hidden area. Only when the two are consistent, the program enters the running state.
[0023] Take a certain embedded device program as an example below to illustrate, when the authorization flag of the embedded device program is OX00, it is in an unauthorized state, and when it is OX01, it is in an authorized state; Randomly generated by the server); the corresponding authorization code is ab...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com