Method for configuring secure element, and configurable secure element
A technology of security components and software packages, which is applied in security devices, security communication devices, electrical components, etc., and can solve problems such as complex personalized processing
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0030] According to this document, key generation for e.g. smart card applications can be implemented on the card. Personalization of smart cards is made easier and less expensive since the personalization is performed on the card rather than off the card through a specific security device. Note that the methods disclosed herein can be applied to secure elements embedded in smart cards as well as secure elements embedded in mobile devices, such as NFC enabled mobile phones. More specifically, the methods disclosed herein are capable of executing virtual smart card applications such as The application is very beneficial for use in mobile devices.
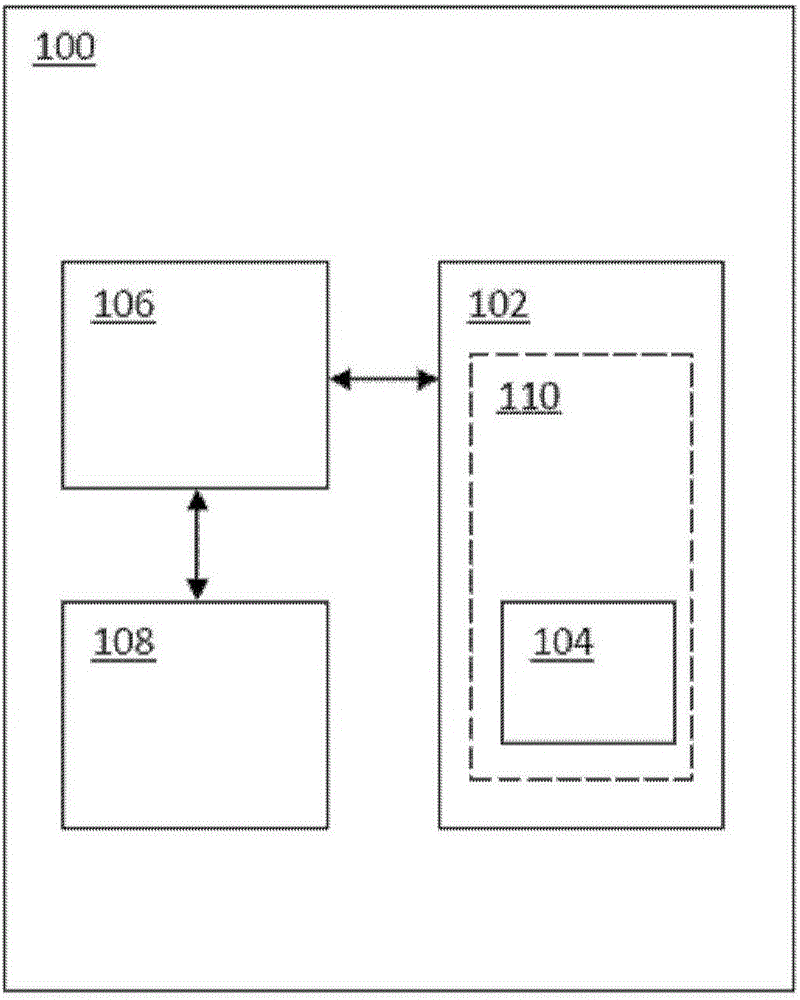
[0031] figure 1 An example of a mobile device 100 including a secure element 102 is shown. In addition to the secure element 102, the mobile device 100 may also include an NFC controller 106 and an NFC antenna 108 to establish near field communication between the mobile device 100 and an NFC reader device (not shown). For exampl...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com