Network protection method and device, and primary convergence network element in network
A technology for protecting devices and network elements, applied in the field of communications, can solve problems such as service flow interruption and failure to achieve linkage protection in networking, and achieve the effect of avoiding service flow interruption
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
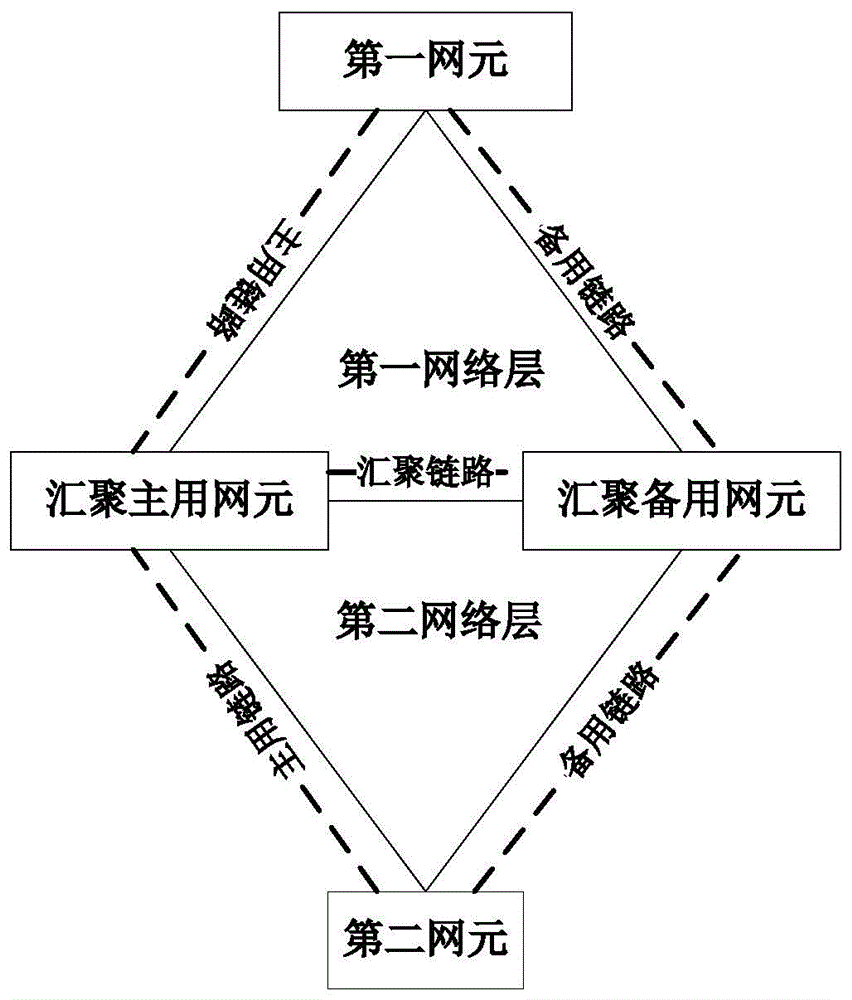
[0046] Please refer to figure 1 As shown, the networking in this embodiment includes a first network layer and a second network layer, a first network element and a second network element respectively located in the first network layer and the second network layer, and a network element located in the first network layer and the second network layer The aggregation main NE and the aggregation standby NE at the convergence point of the second network layer; the link connecting the first NE and the aggregation main NE is the main link of the first network layer; the second NE and the aggregation main NE The link connected by the network element is the active link of the second network layer; the link connecting the first network element and the converged standby network element is the standby link of the first network layer; the second network element and the converged standby network element The connected link is the backup link of the second network layer; the link connecting ...
Embodiment 2
[0066] The networking provided by this embodiment is the same as figure 1 As shown; this embodiment also provides a network protection device, please refer to Figure 4 As shown, including the fault detection module and the first link switching module:
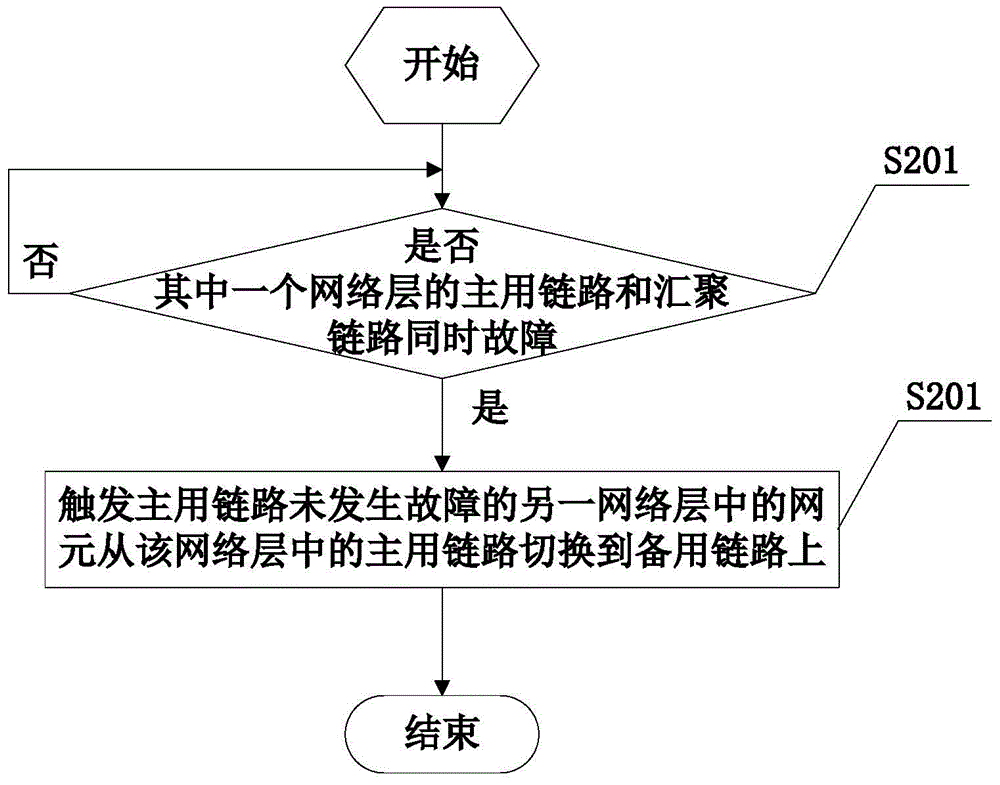
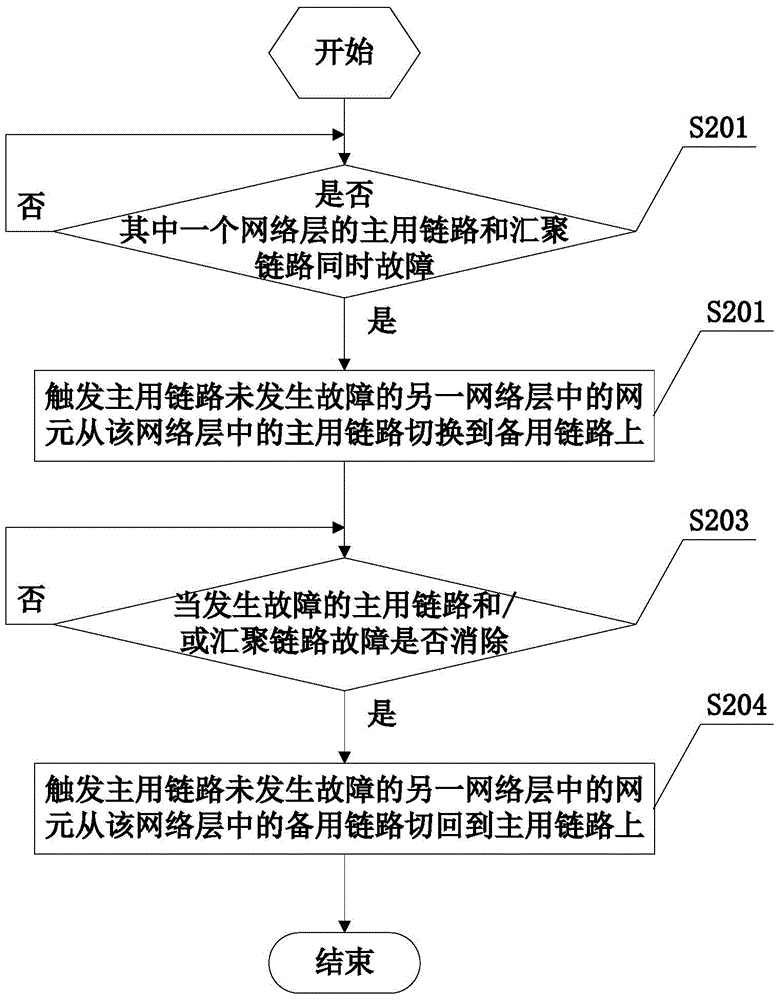
[0067] The failure detection module is used to detect whether the active link of one of the network layers in the two network layers and the aggregation link fail simultaneously, and if so, notify the first link switching module; in this embodiment, the failure detection module includes The message detection submodule is used to detect whether the state detection message sent by the network element in one of the network layers in the two network layers can only be received normally; The link and the aggregated link fail simultaneously.
[0068] The first link switching module is used to trigger a network element in another network layer where the active link has not failed to switch from the active link in the network layer ...
Embodiment 3
[0075] This example provides figure 1 The convergent main network element in the shown network includes a memory and a processor; the memory is used to store instructions; the processor is used to call the instructions to execute the steps shown in the first embodiment. In the following, the first network layer is the three-layer virtual private network layer (L3VPN, LayerThreeVirtualPrivateNetwork), the first network element is the core layer network element; the second network layer is the two-layer virtual private network layer, namely (L2VPN, LayerTwoVirtualPrivateNetwork) networking , and the second NE is an access layer NE as an example. For details, see Figure 5 shown. In this embodiment, link switching is realized by L3VPNFRR (fast rerouting, FastReRoute) in L3VPN, and the corresponding state detection message is a BFD (BidirectionalForwardingDetection, bidirectional forwarding detection) message; The corresponding state detection message is a CCM (Continuity check ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com