Data detection method and device
A data detection and data technology, applied in the field of network security, can solve problems such as terminal malicious data intrusion, system or user data threats, etc., and achieve the effect of ensuring security and reliability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach
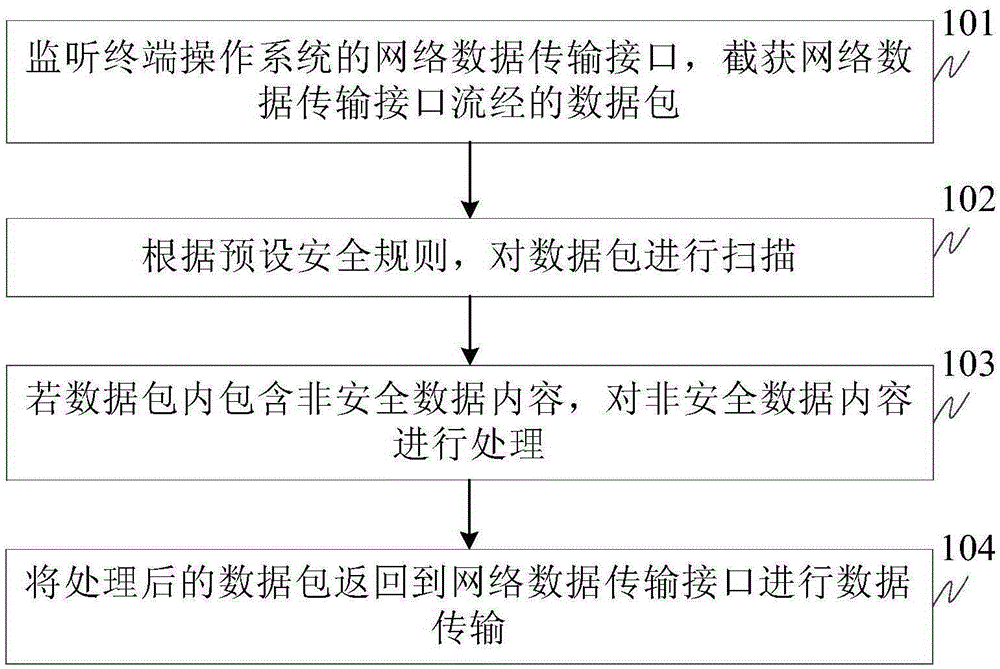
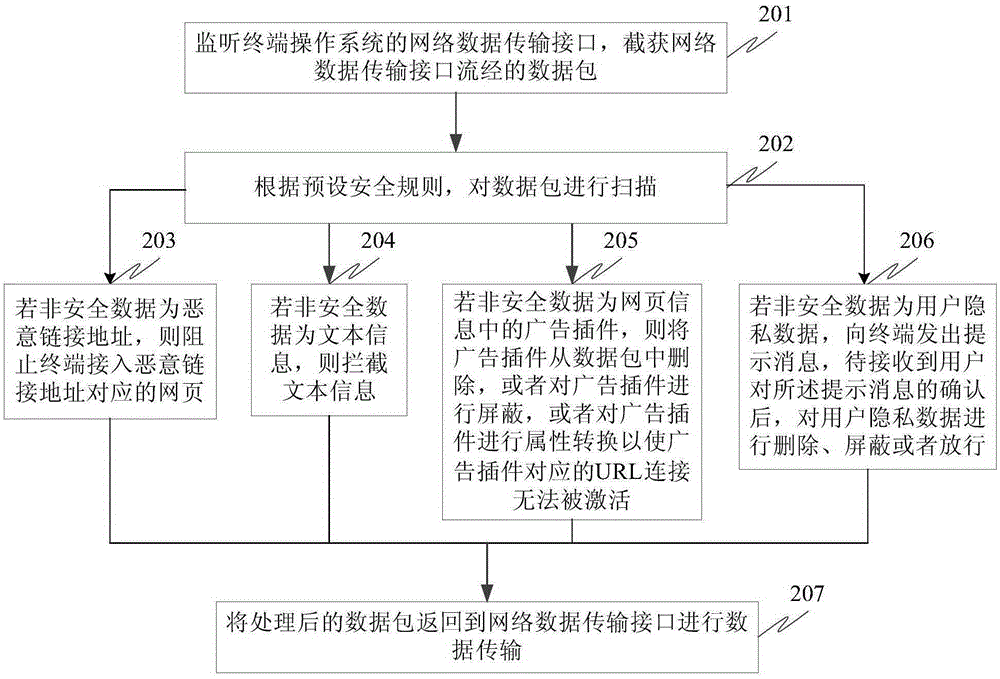
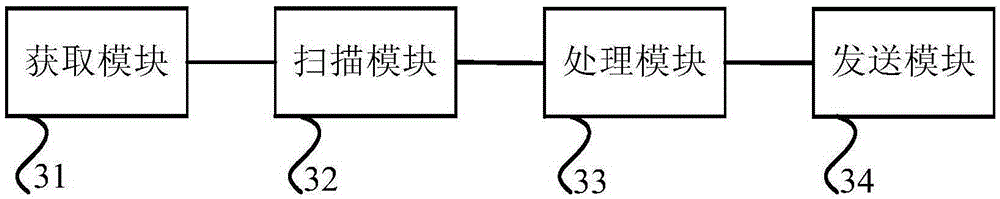
[0072] A) The hook program is used to capture the interface function of the terminal operating system to send or receive network data, and when the interface function is captured, the data packet to be sent or to be received pointed to by the interface function is intercepted.
[0073] The Hook mechanism allows applications to intercept operating system messages or specific events. It is a message processing mechanism in the operating system. Applications can set subroutines on it to monitor certain messages of specific interface functions provided by the operating system. , such as the interface function for sending and receiving network data, the implementation of the hook mechanism can be achieved by: obtaining a hook plug-in corresponding to a specific event behavior from a background sandbox HOOK framework, and using the hook plug-in to monitor the specific event behavior of the target application. Achieved. The background sandbox HOOK framework can be centrally managed o...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com