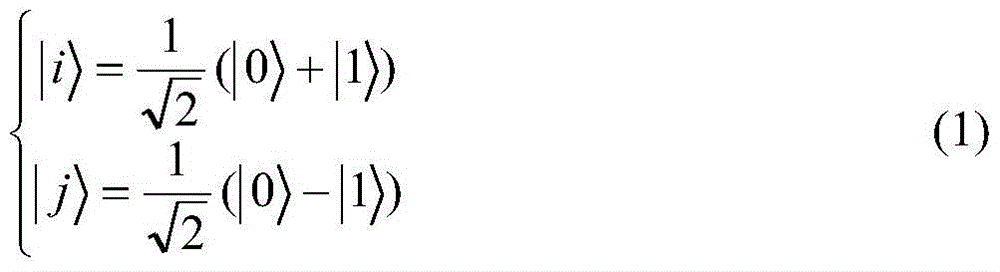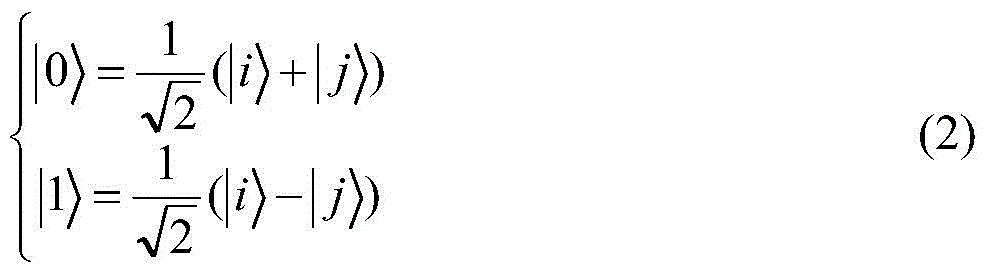Quantum authentication method for access control among three elements of cloud computing
A technology of access control and authentication method, which is applied in the field of collar security communication, can solve the problem of no secret, etc., and achieve the effect of high communication efficiency and reliable security guarantee
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0034] Below in conjunction with accompanying drawing and embodiment, the present invention will be further described:
[0035] In this embodiment, set {|0>, |1>} to be a set of orthonormal basis, denoted as C x ;{|i>,|j>} is a set of orthonormal basis, denoted as C y ;C x with C y There is the following relationship between the two:
[0036]
[0037] Equivalent to:
[0038]
[0039] C x with C y Satisfy the following formula:
[0040]
[0041] The two photon EPR entangled pairs in the quantum entangled photon pair are in the following entangled states:
[0042]
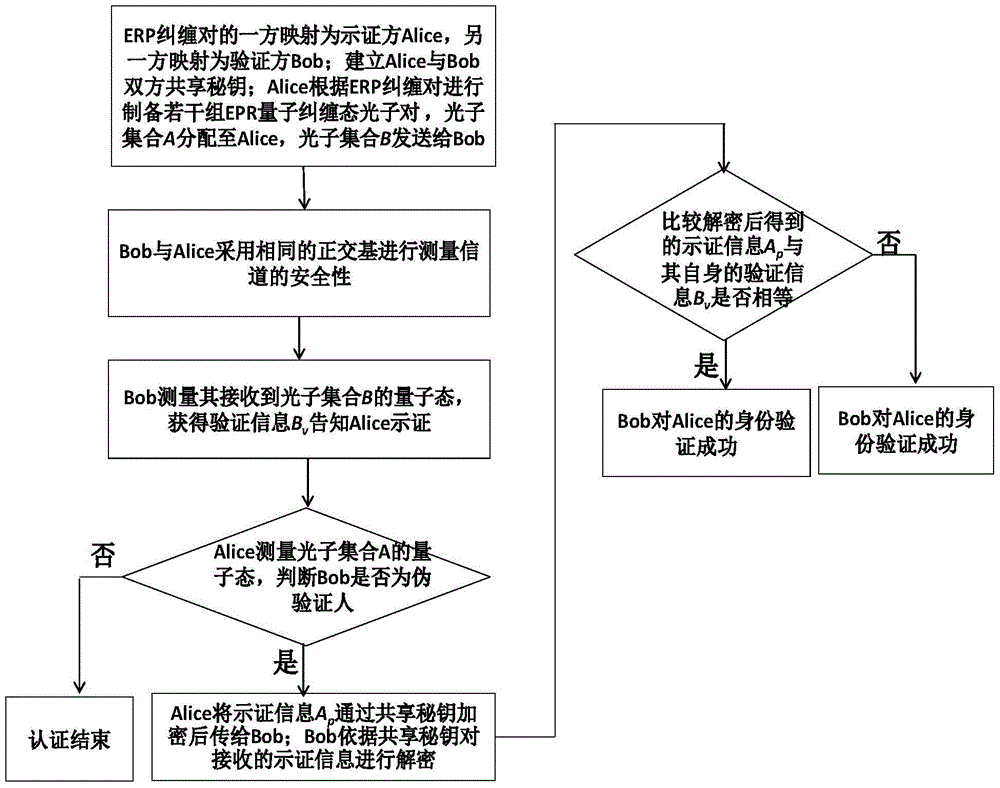
[0043] likefigure 1 As shown, the mutual quantum authentication process between CSP and DUser in the cloud model is as follows:
[0044] (1) Both CSP and DUser establish a shared secret key:
[0045] A shared secret key K needs to be established between the sender CSP (Alice) and the receiver DUser (Bob). AB , the establishment of the key can be achieved through the quantum distribution protoco...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com