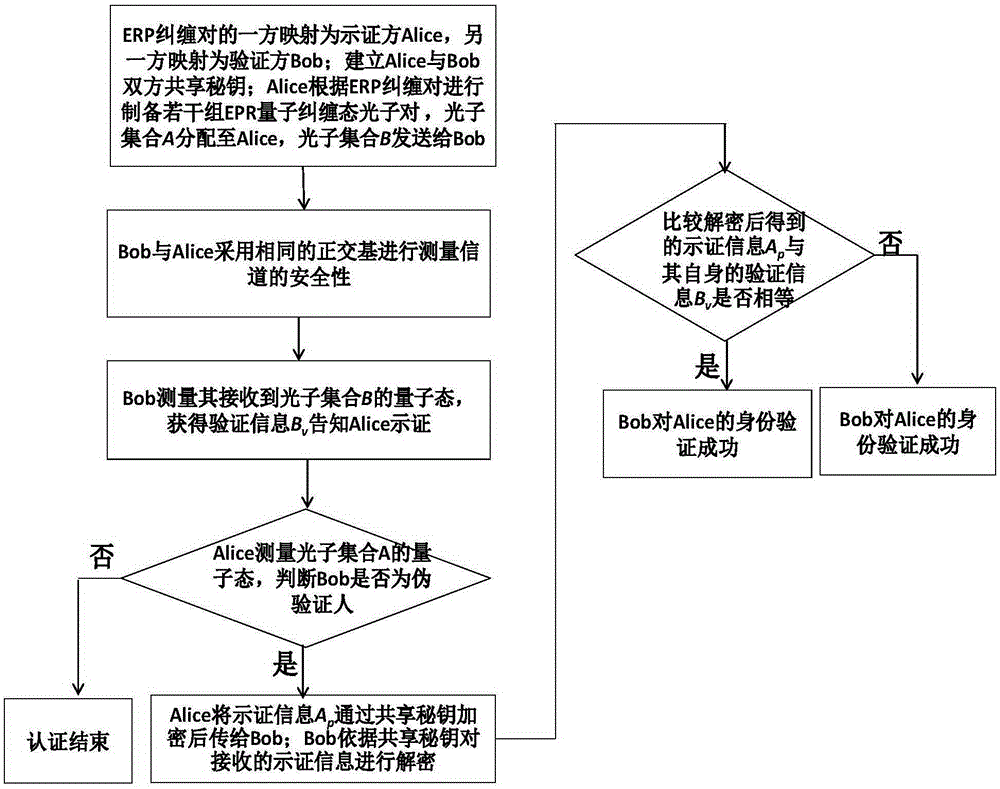
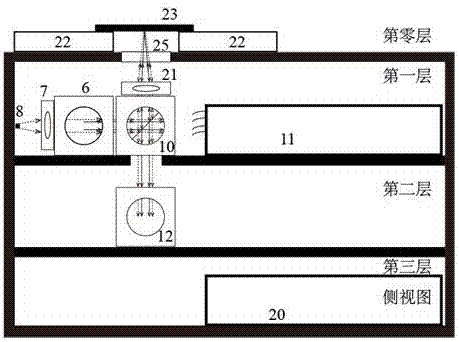
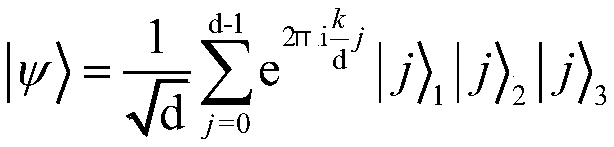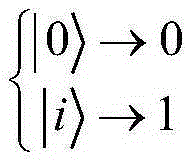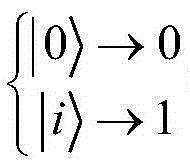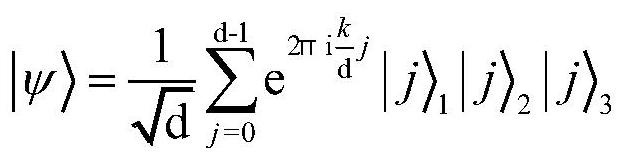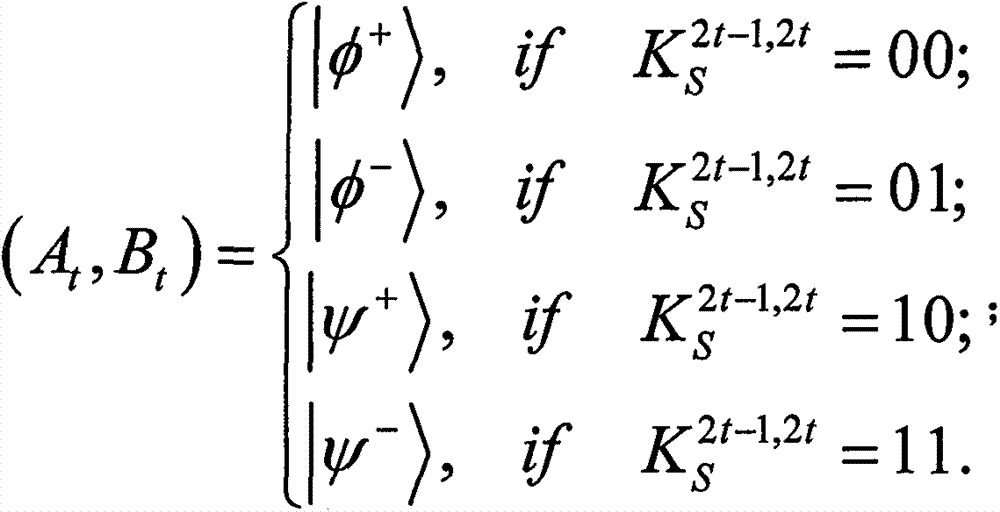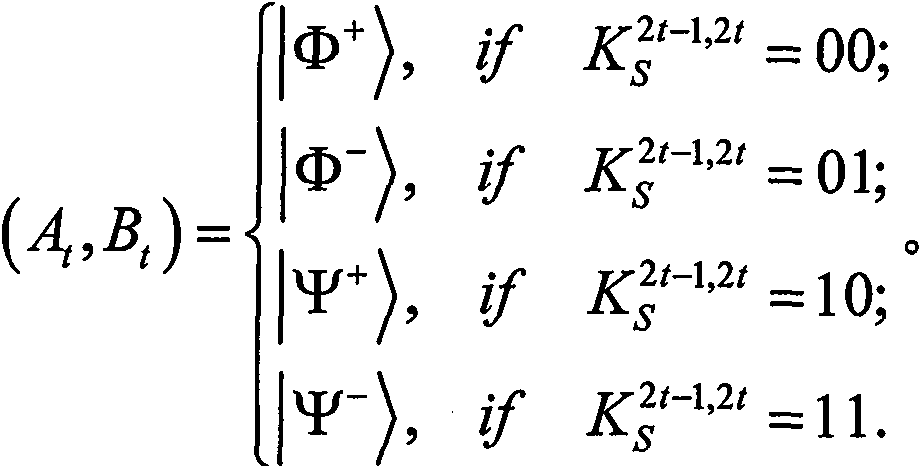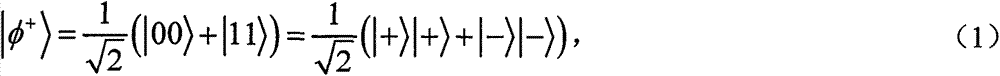Patents
Literature
30 results about "Quantum authentication" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
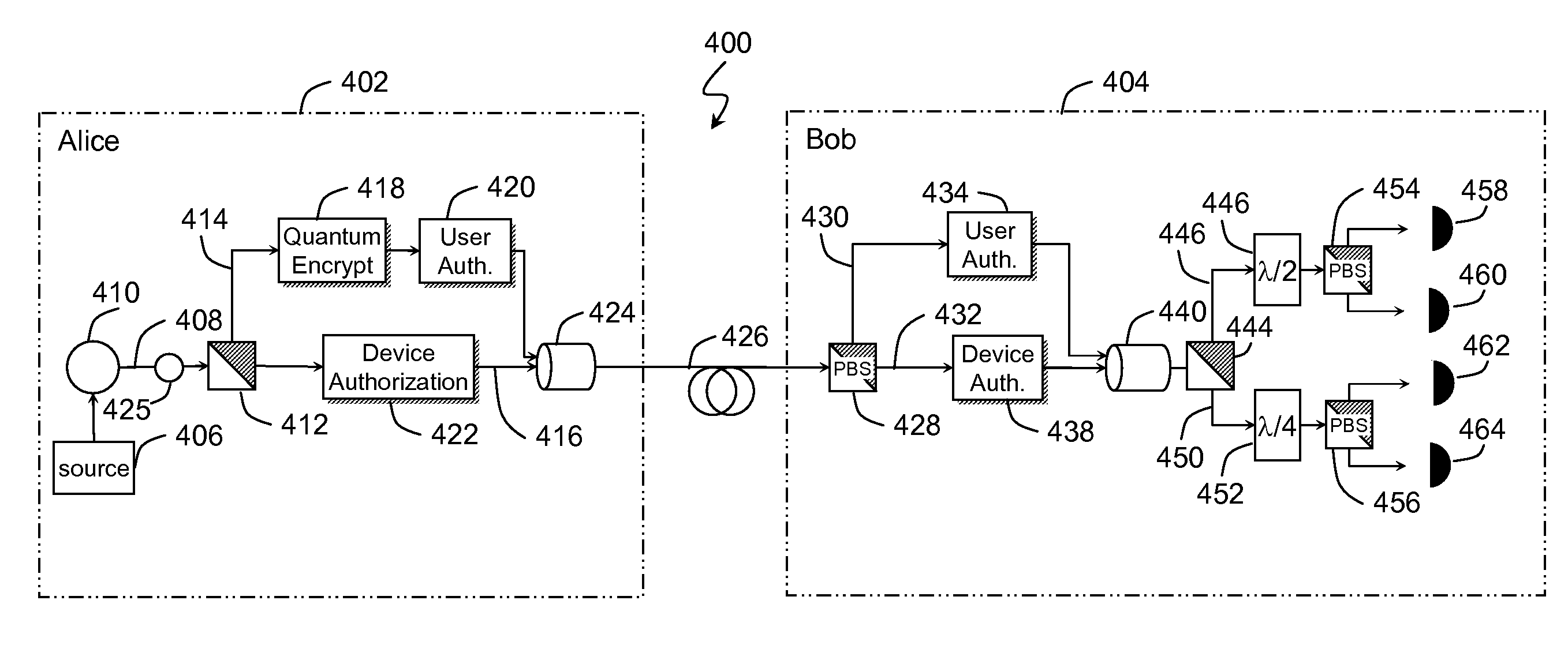
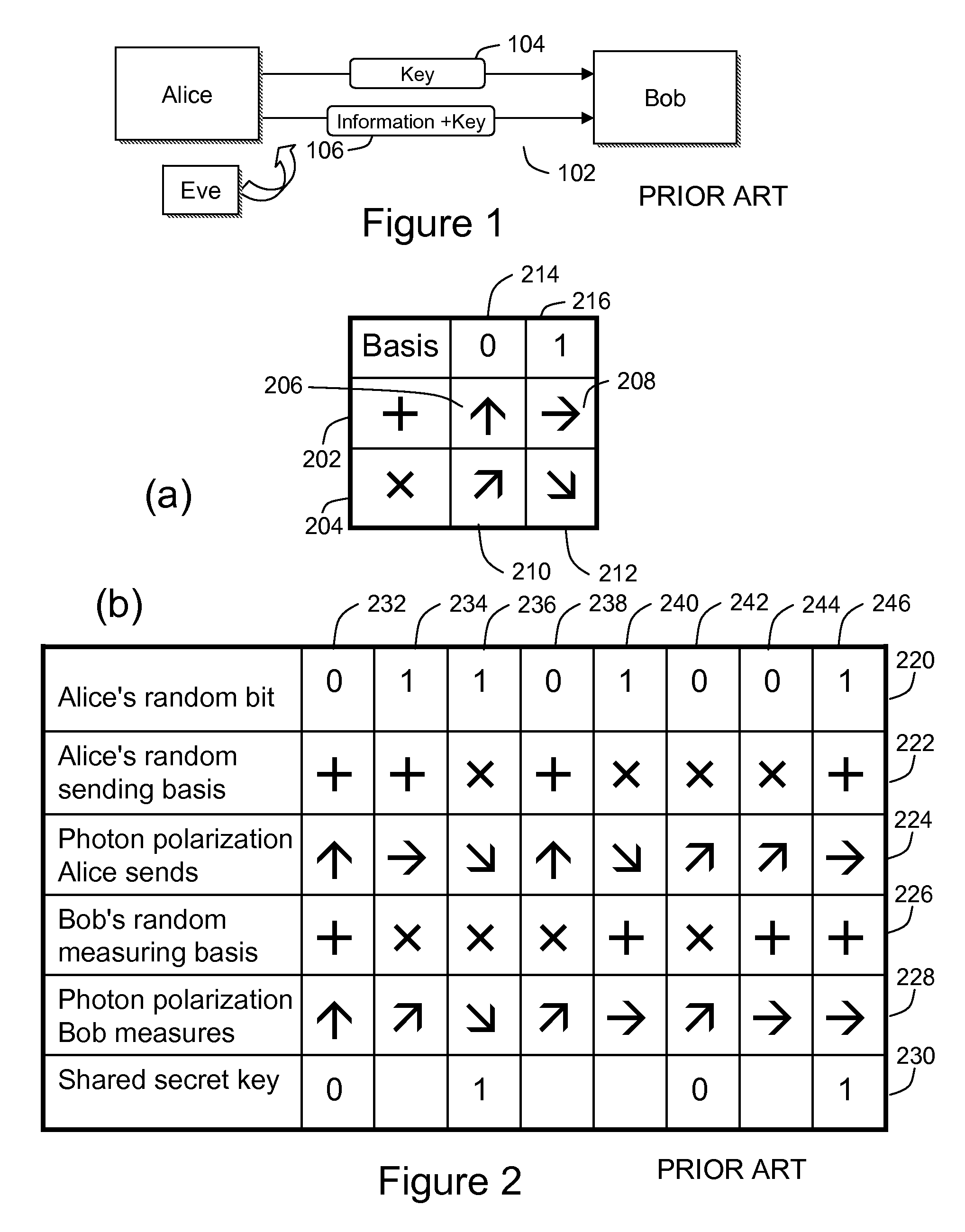
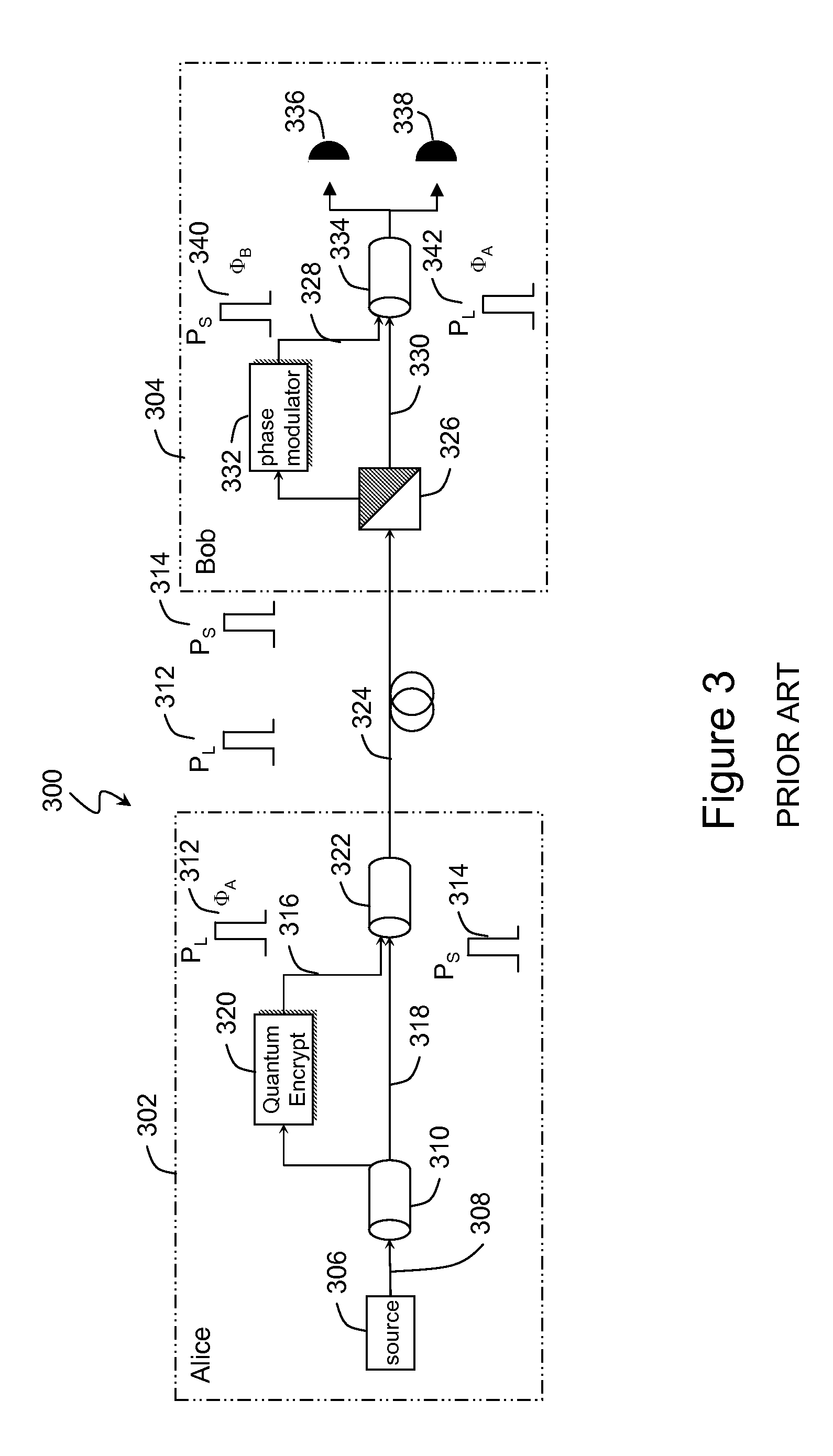
Method and system utilizing quantum authentication
ActiveUS20090106553A1Key distribution for secure communicationFreely-suspended gymnasticsPhase shiftedTime delays
A system and a method with quantum cryptography authentication. The system includes an optical link connecting a sender and a receiver. The sender transmitting a first optical pulse and a second optical pulse having a defined time delay therebetween. The first pulse is modulated with a first authentication phase shift; and the second pulse is modulated with phases selected from one basis of two non-orthogonal bases, and encoded with one of two orthogonal states within the one basis based on an information of the sender, and with a second authentication phase shift. The receiver includes a splitter receiving and splitting the first and the second pulse into pulses of interest. The split pulses of interest are modulated with the first authentication phase shift; and the second authentication phase shift, respectively. The receiver includes a second coupler whereby the split pulses of interest arrive at the second coupler simultaneously. The receiver includes a first set of detectors receiving the combined pulses, which determine the one basis of the two non-orthogonal bases; and a second set of detectors receiving the combined pulses, and determine the one of the two orthogonal states within the basis and thereby decoding the information of the sender.
Owner:CHEN ZHIHONG +1
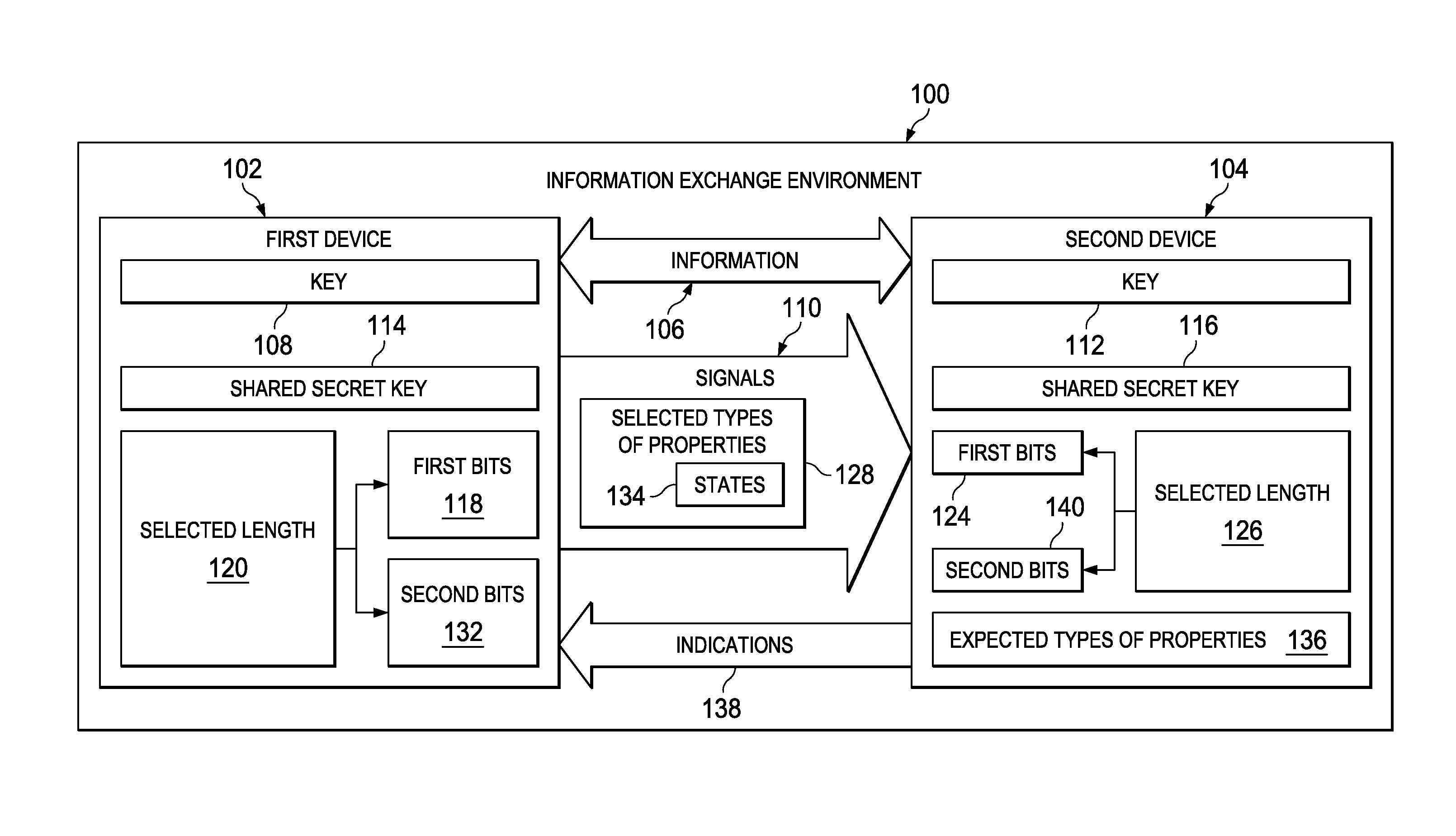
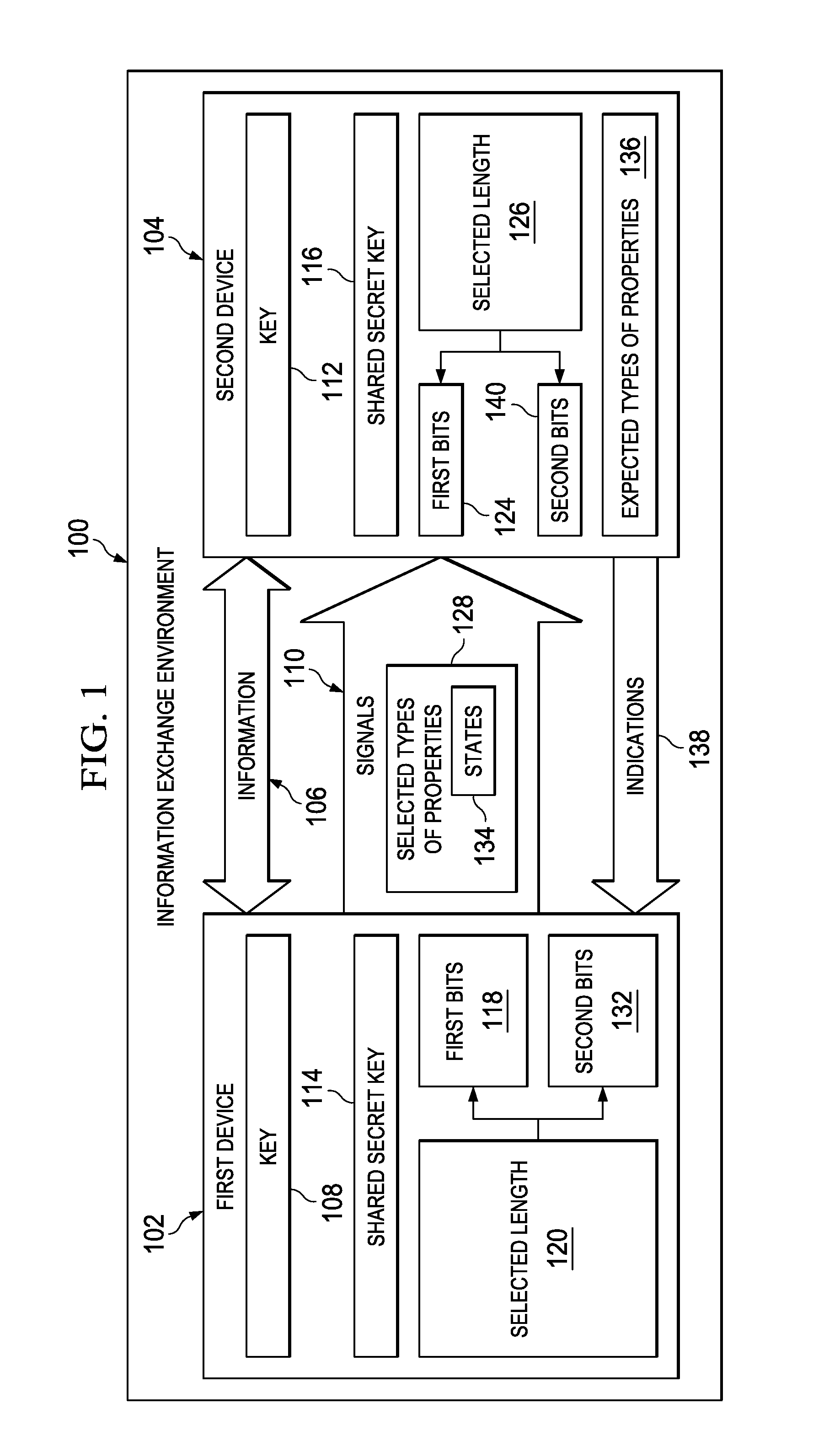
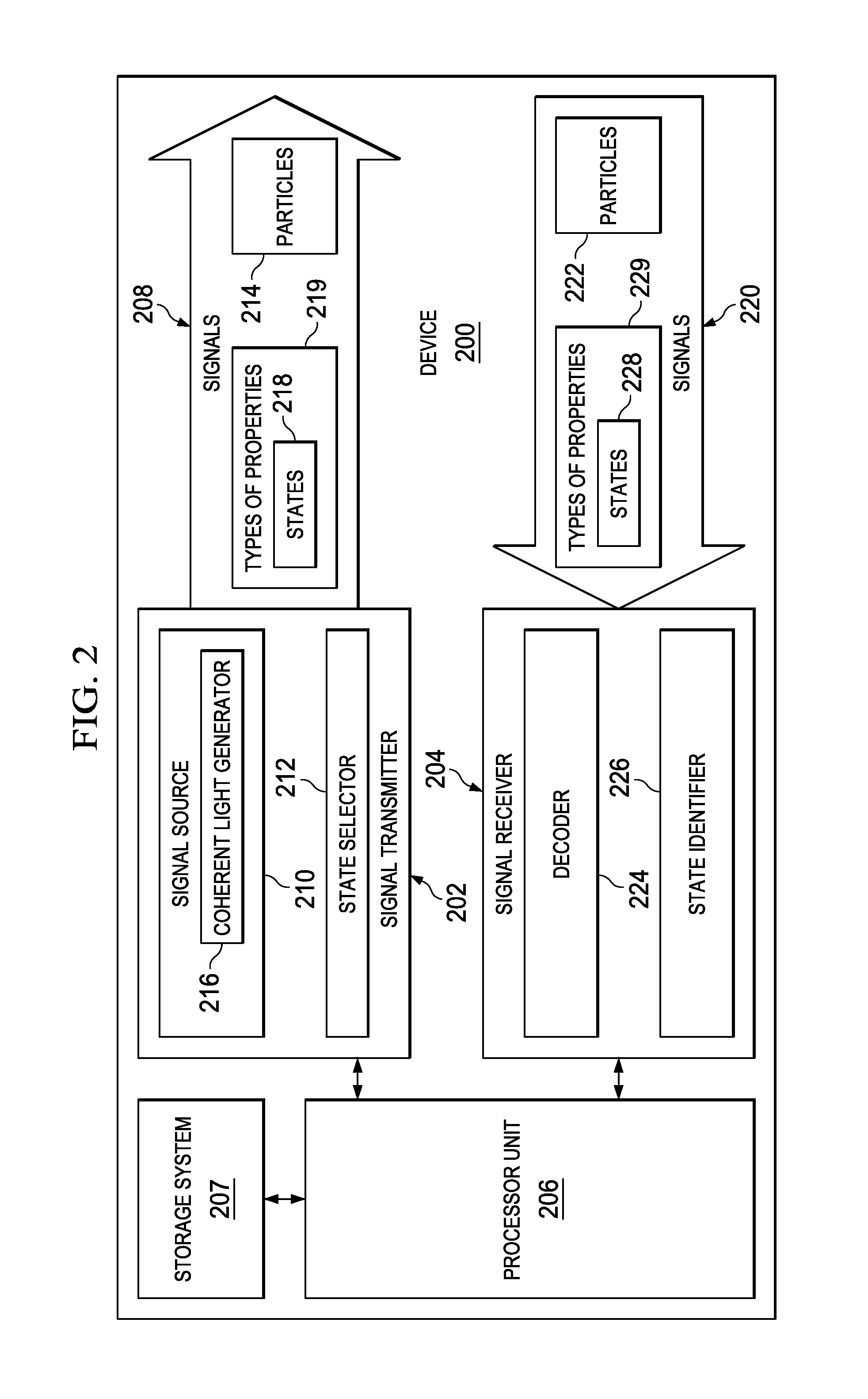
Secure quantum authentication system
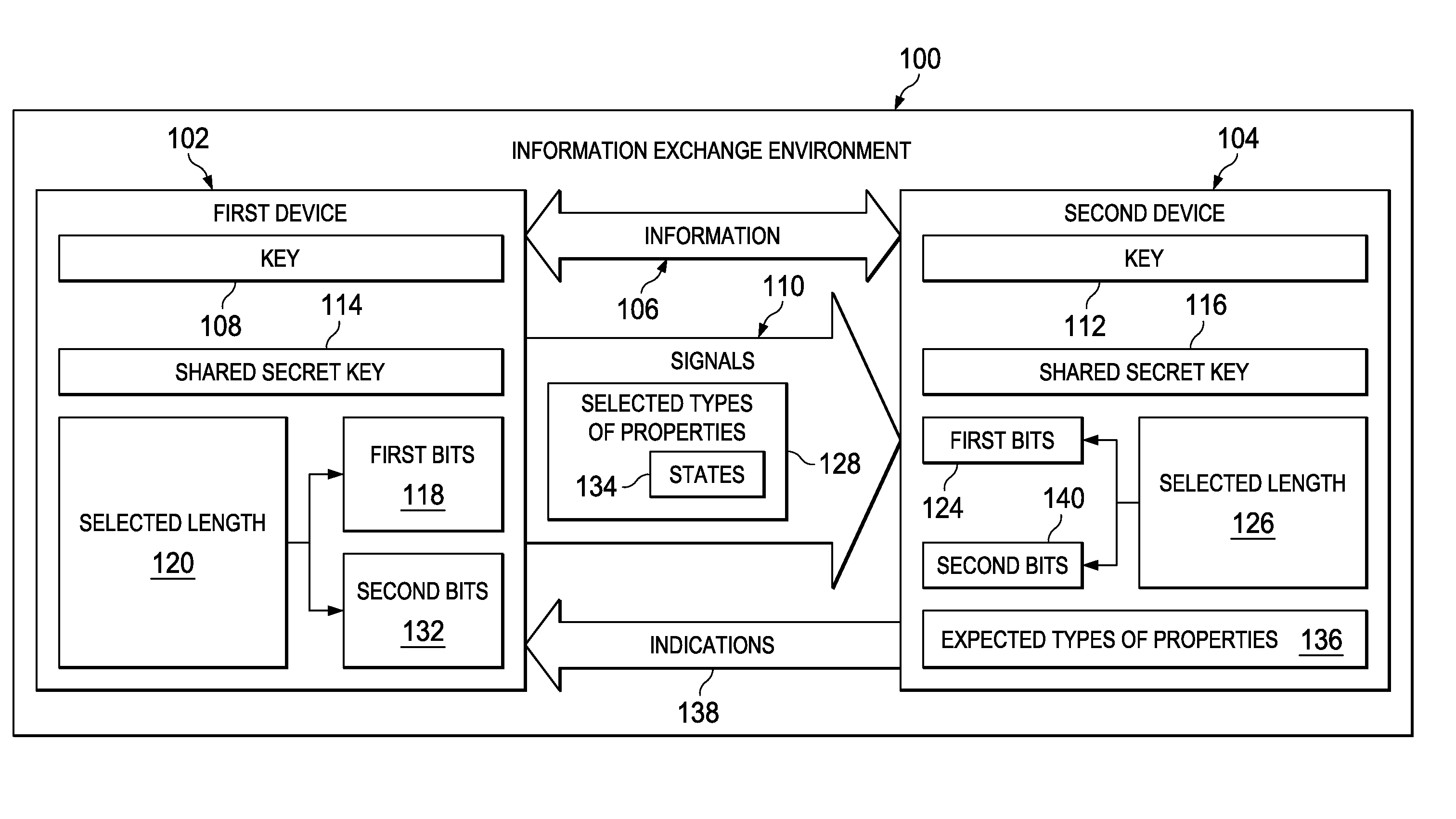
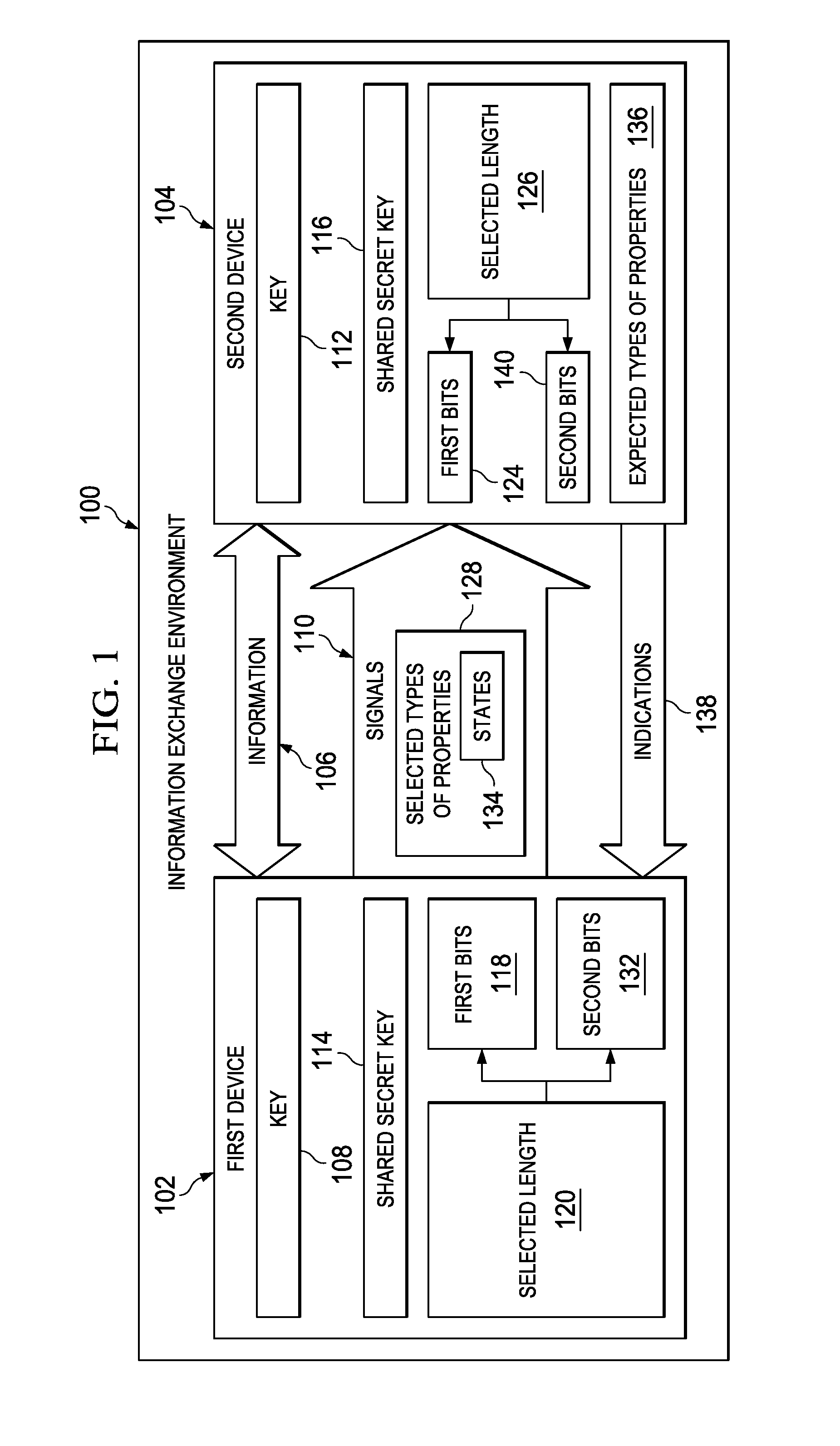
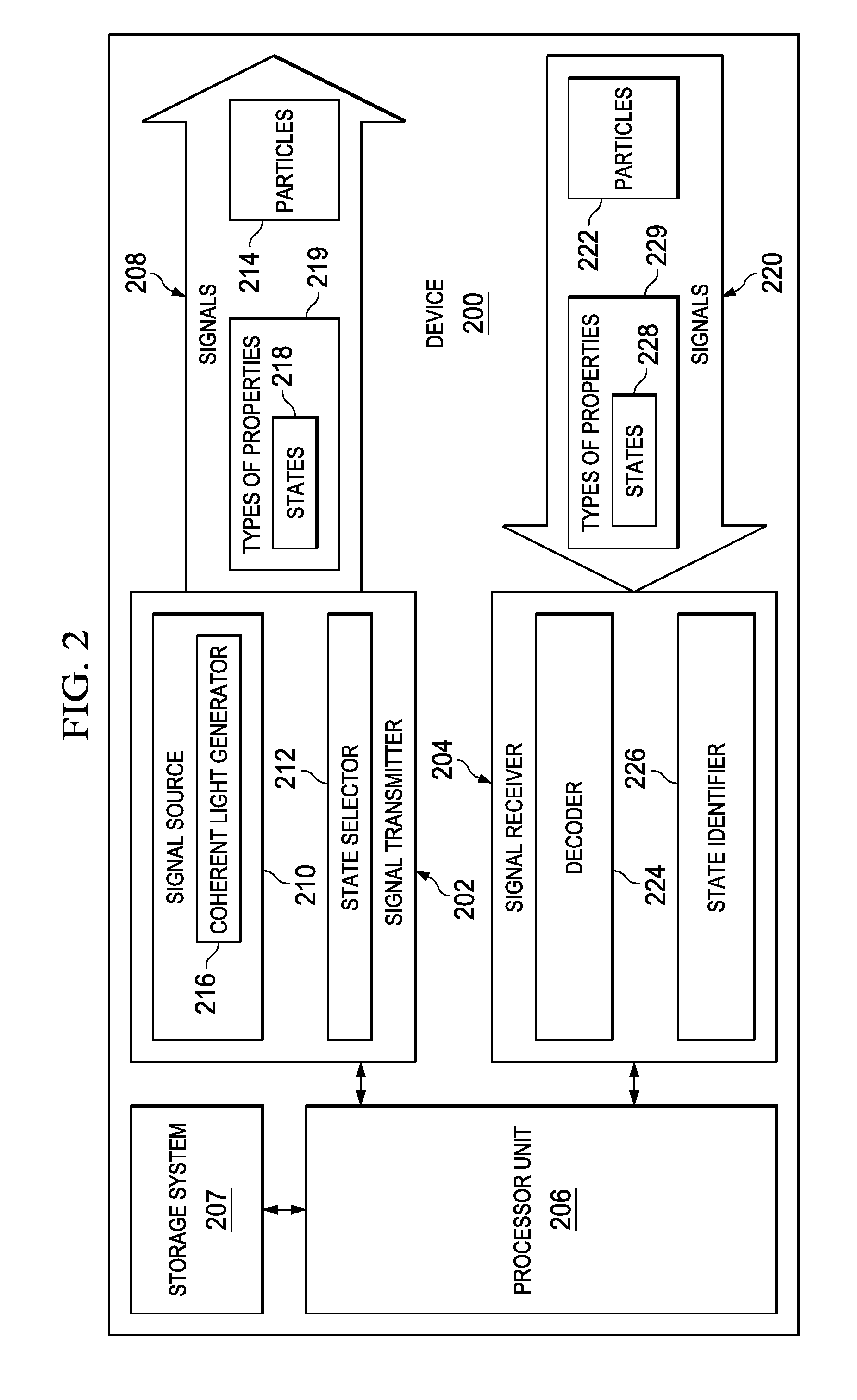
ActiveUS9184912B2Key distribution for secure communicationUser identity/authority verificationComputer hardwareQuantum authentication
A method and apparatus for sharing information. First bits are selected from a shared secret key in a first device. The first bits have a selected length. Second bits with the selected length in signals are sent from the first device to a second device. The signals have selected types of properties based on the first bits. The second bits are encoded in states for the selected types of properties. A key is generated in the first device. The key is based on the second bits received at the second device having the selected types of properties identified as matching expected types of properties.
Owner:THE BOEING CO
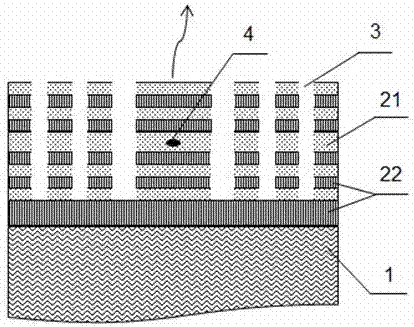
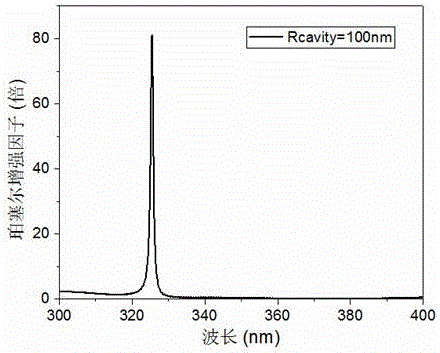
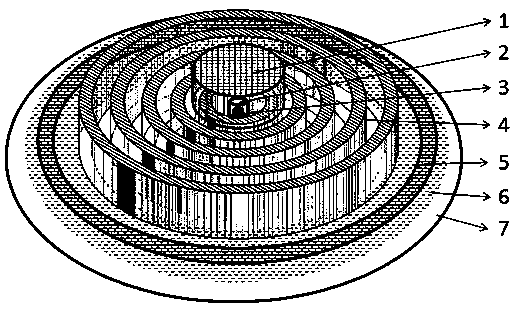
Hyperbolic metamaterial composite grating-enhanced high-frequency quantum-dot single photon source
ActiveCN107452844AIncrease spawn rateImprove production efficiencySemiconductor devicesGratingParticle physics
The invention discloses a hyperbolic metamaterial composite grating-enhanced high-frequency quantum-dot single photon source. The hyperbolic metamaterial composite grating-enhanced high-frequency quantum-dot single photon source comprises a substrate, a hyperbolic metamaterial and quantum dots, wherein a grating microstructure is arranged on a surface of the hyperbolic metamaterial or in the hyperbolic metamaterial, the hyperbolic metamaterial is of a one-dimensional periodic structure formed by alternatively arranging dielectric thin films and metal thin films or the dielectric thin films and metal-like thin films, and the quantum dots are arranged in the one-dimensional periodic structure or a near field of the hyperbolic metamaterial. Spontaneous radiation enhancement of wideband of the quantum dots is achieved by the hyperbolic metamaterial, the light emergent efficiency is improved by simultaneously combining directional coupling output characteristic of the grating, the photon generation ratio and the collection and utilization ratio of the quantum-dot single photon source are greatly improved, and the high-frequency, high-brightness and directional-emission quantum-dot single photon source of GHz or above can be achieved; and meanwhile, two excitation modes of optical pumping and electric pumping are compatible, and the quantum-dot single photon source is suitable for various wave bands to an infrared band from an ultraviolet band and can be widely applied to related fields of quantum information, quantum computation, quantum imaging, quantum authentication and quantum precision measurement.
Owner:INST OF ELECTRONICS ENG CHINA ACAD OF ENG PHYSICS
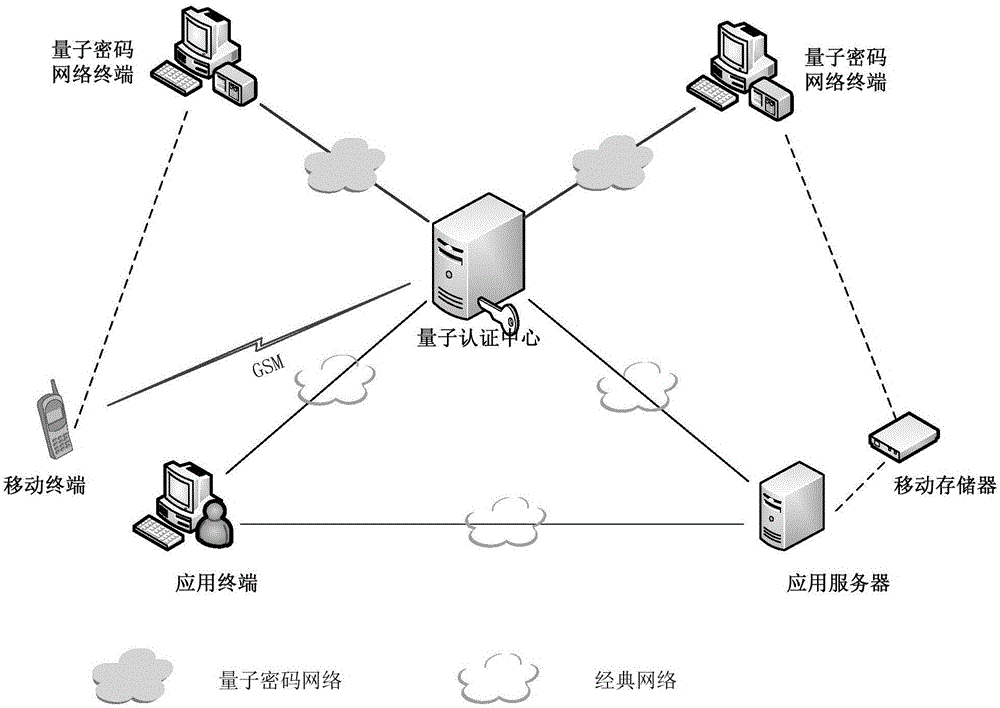
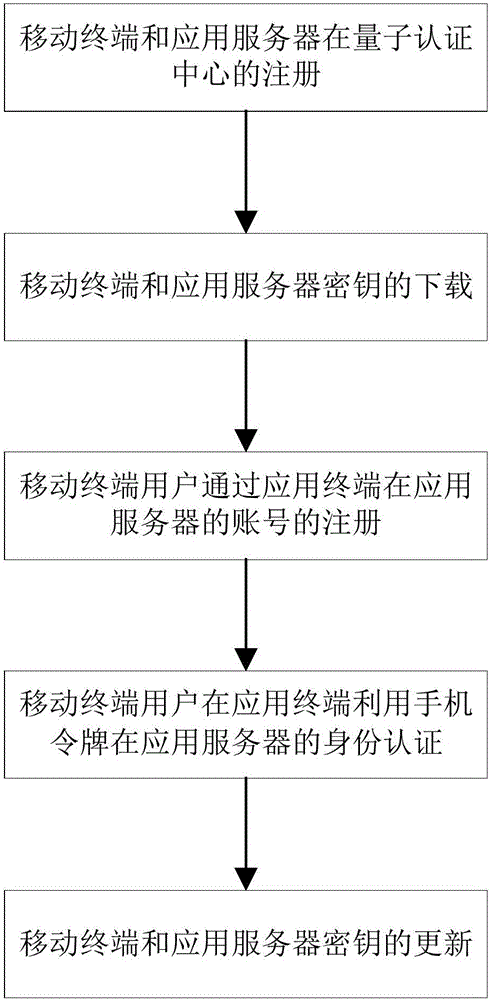
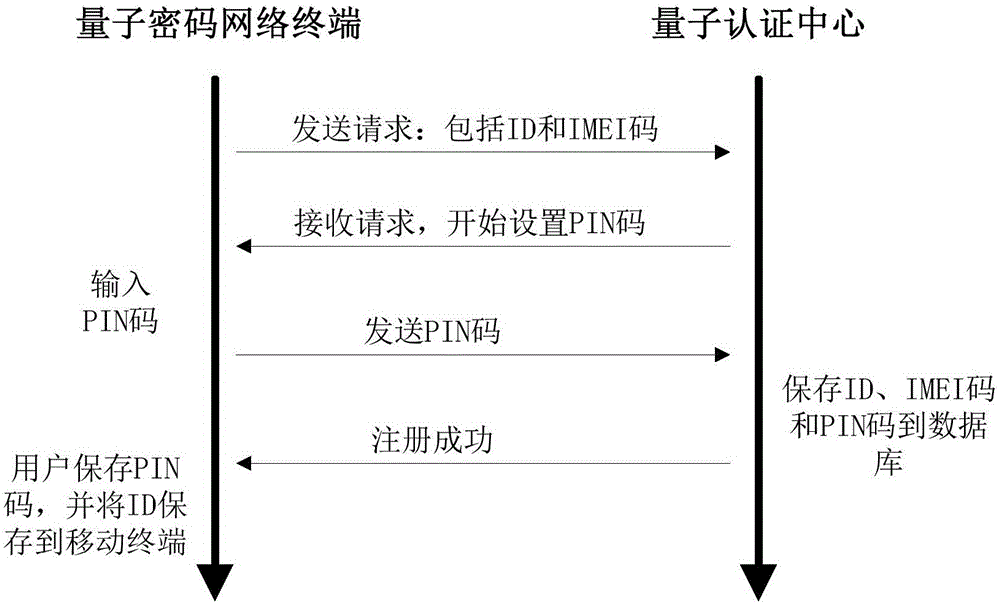
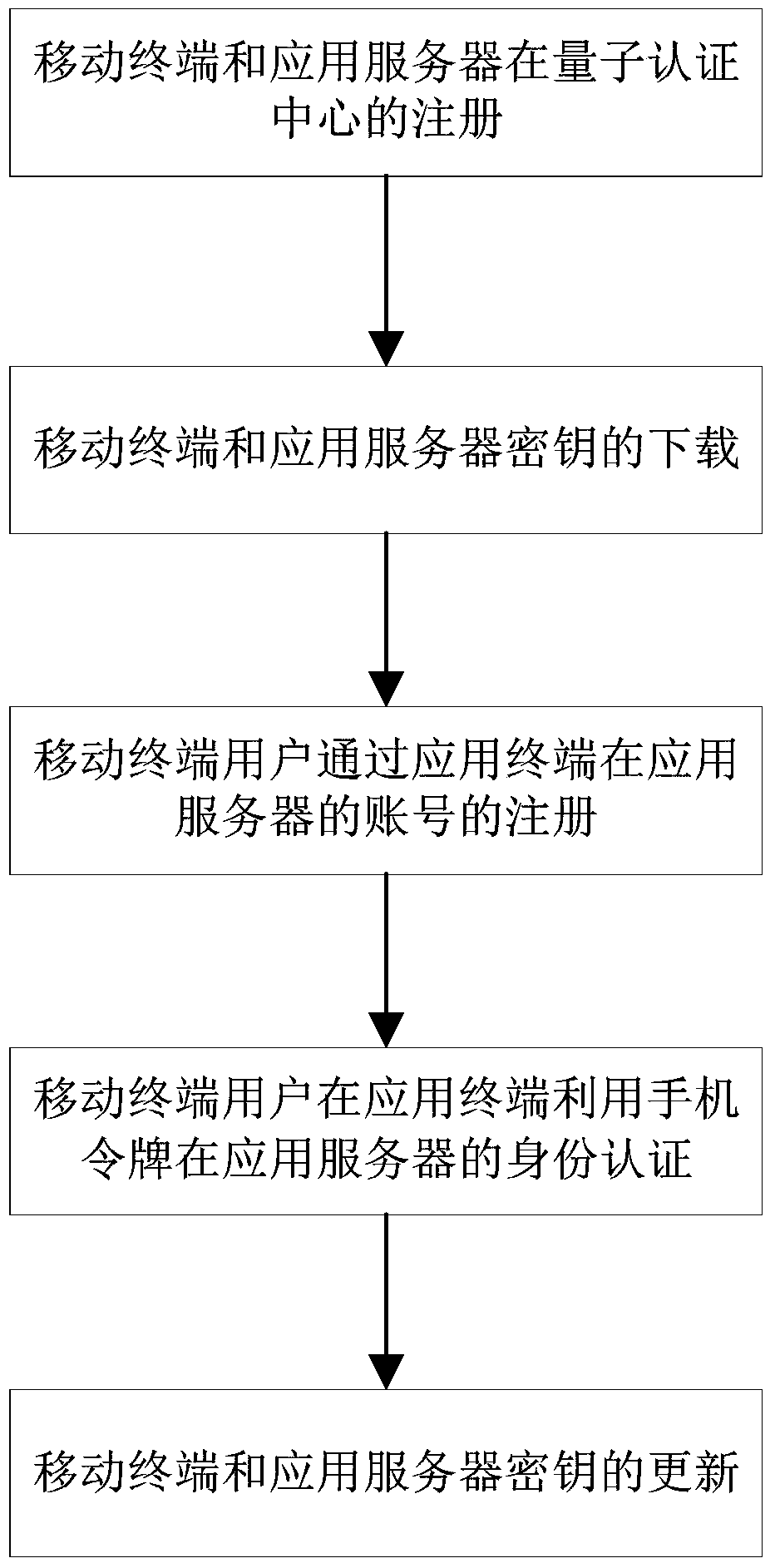
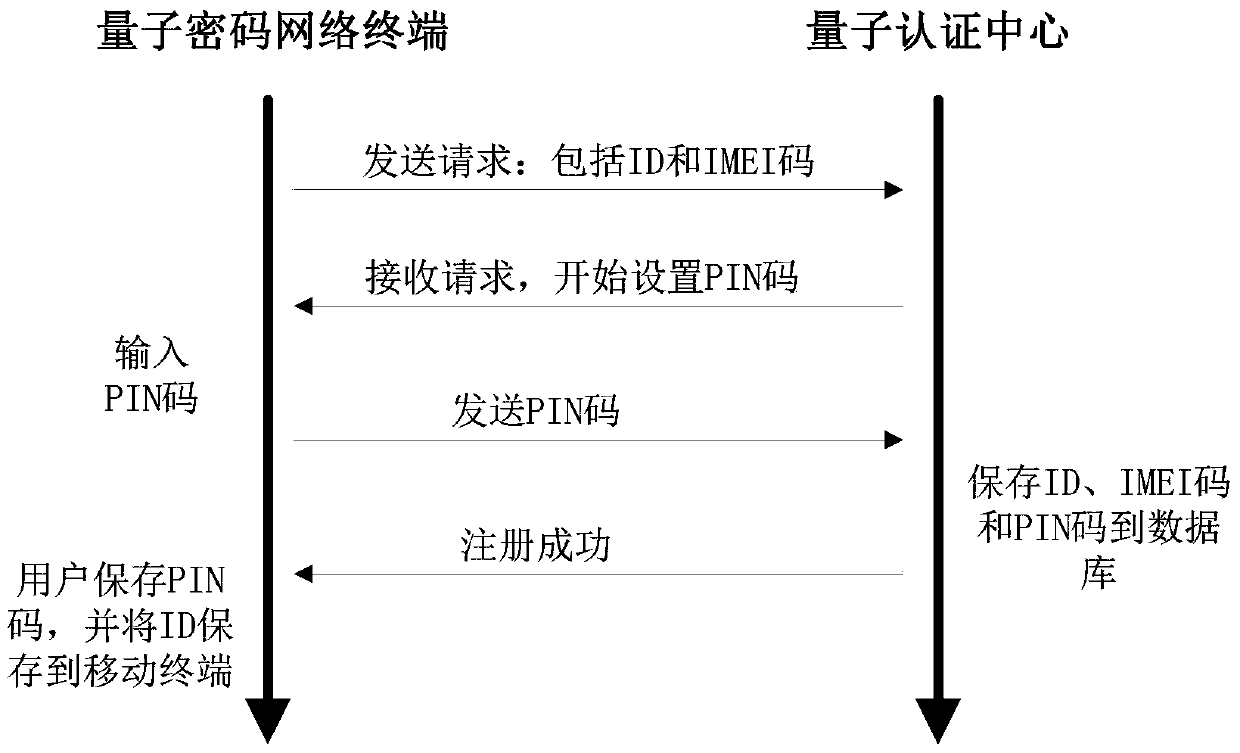
Mobile phone token identity authentication system and method based on quantum cipher network
ActiveCN106712931AUnconditionally safeEnsure safetyKey distribution for secure communicationUser identity/authority verificationDomain nameApplication server
The invention provides a mobile phone token identity authentication system based on a quantum cipher network. A mobile terminal and an application server register a quantum authentication center through a quantum cipher network terminal, an ID, an IMEI code or a domain name is provided in registration, and PIN codes are set. The mobile terminal and the application server download a quantum key at the quantum cipher network terminal, and the database of the quantum authentication center stores downloaded quantum key data. A mobile terminal user provides an ID of the mobile terminal user when the application server registers. When the application server needs the identity authentication of the mobile terminal user, the mobile terminal calculates a dynamic password by using the download quantum key, the application server transfers the dynamic password to the quantum authentication center, and the quantum authentication center notifies the mobile terminal user of a verification result through the application server. The invention also provides an authentication method. The system and the method have the advantages of unconditional safety, high synchronization between key use of the mobile terminal and the quantum authentication center, and the improvement of the convenience of user use.
Owner:QUANTUMCTEK SHANGHAI CO LTD
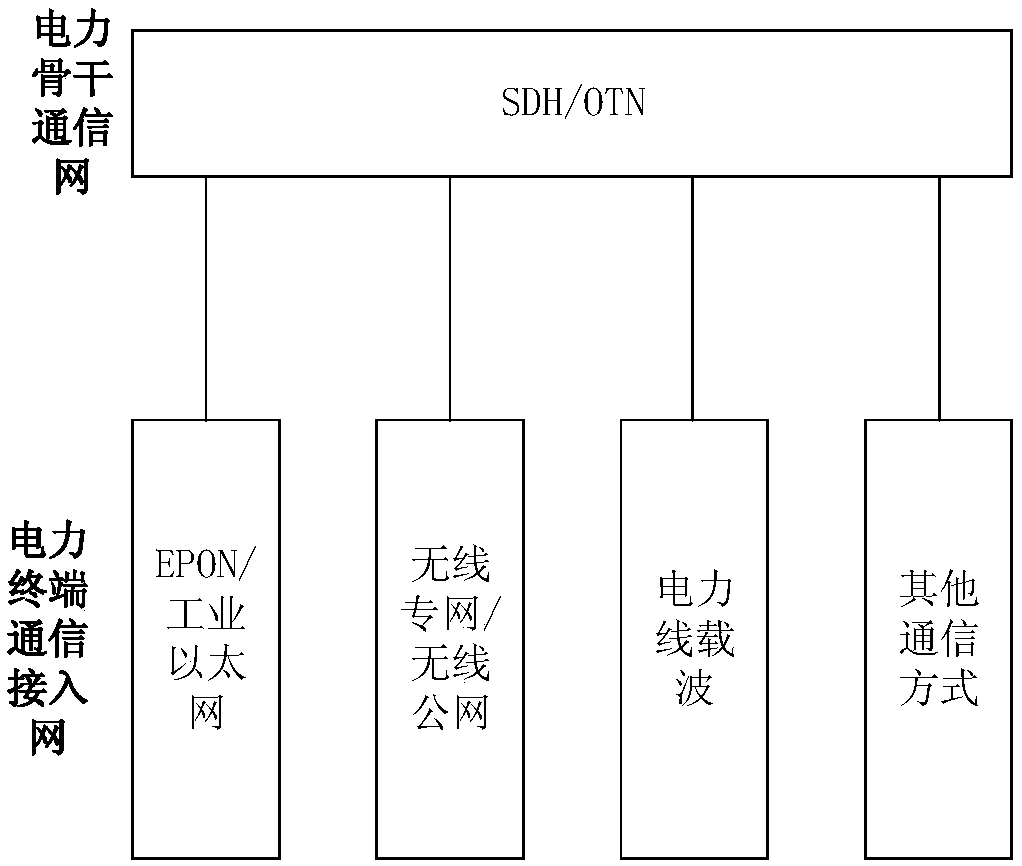
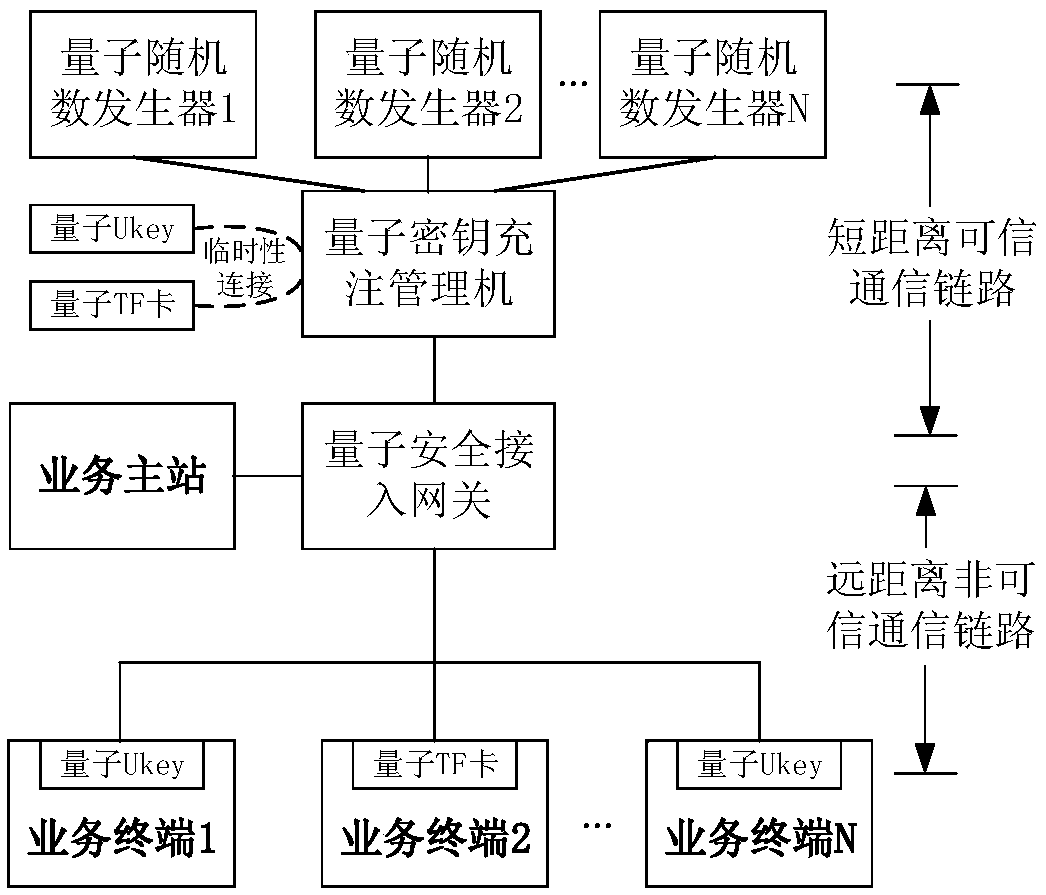
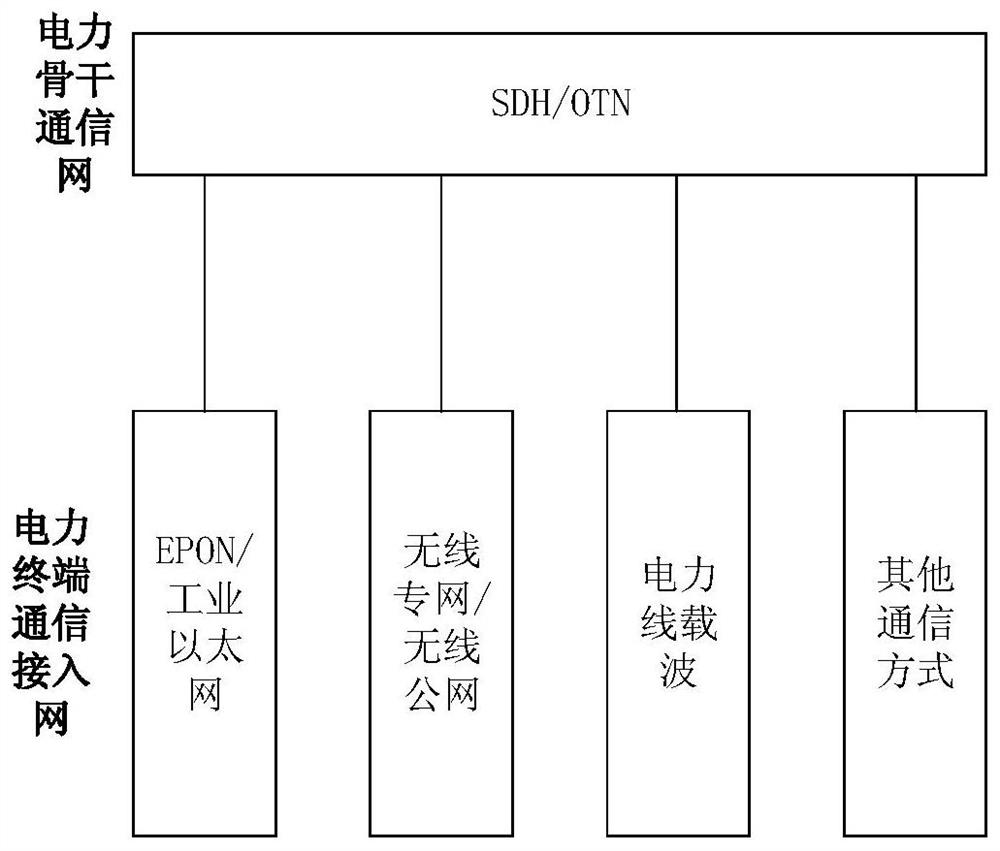
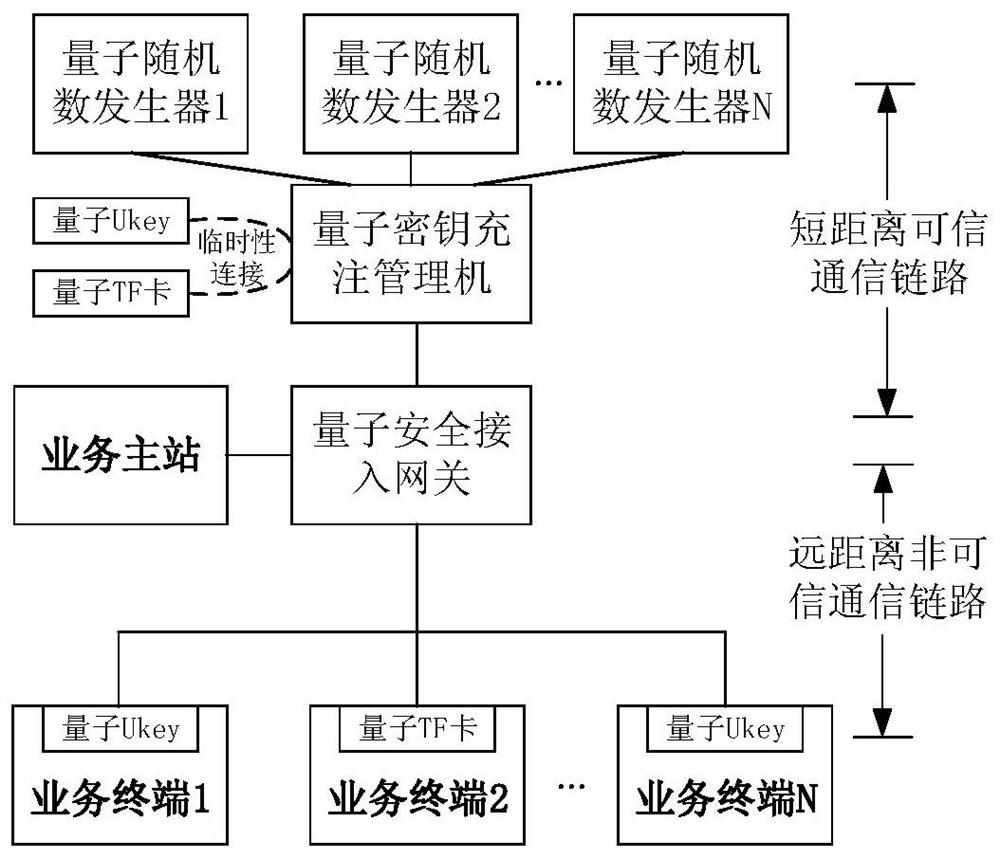
Automatic quantum key charging method and system adapting to electric power services
ActiveCN109412794AImprove the level of practicalityReduce construction costsKey distribution for secure communicationPrimary stationQuantum authentication
The invention discloses an automatic quantum key charging method and system adapting to electric power services. Quantum keys are divided into a quantum authentication key, a quantum encryption key and a quantum updating key according to a deployment structure for electric power service main station convergence and electric power service terminal access; the quantum authentication key is used foridentity authentication during communication interaction; the quantum encryption key is used for encryption and decryption of data during the communication interaction; and the quantum updating key isused to encrypt and decrypt a new quantum key in the communication interaction when used to update the quantum authentication key and the quantum encryption key and / or the quantum updating key. The quantum updating key updates the quantum authentication, encryption and / or updating keys, thereby realizing automatic charging and updating of the quantum keys.
Owner:南京南瑞网络安全技术有限公司 +2
Quantum authentication system integrated on single circuit board
ActiveCN106789031AReduce volumeReduce weightKey distribution for secure communicationUser identity/authority verificationIdentity recognitionDisplay device
Owner:INST OF ELECTRONICS ENG CHINA ACAD OF ENG PHYSICS
Physical non-cloning key for quantum secure authentication and quantum key distribution
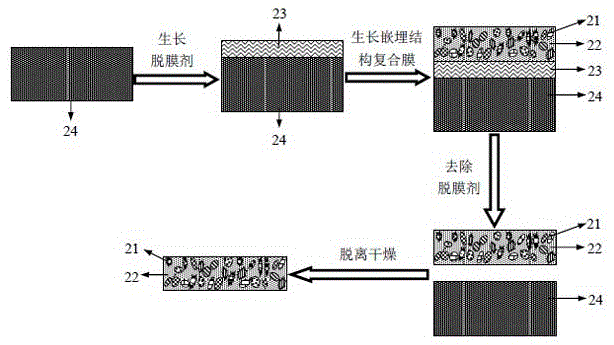
InactiveCN105610584ALarge amount of authentication informationLong equivalent keyKey distribution for secure communicationUser identity/authority verificationMicro nanoRefractive index
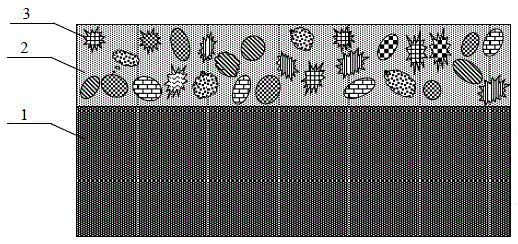
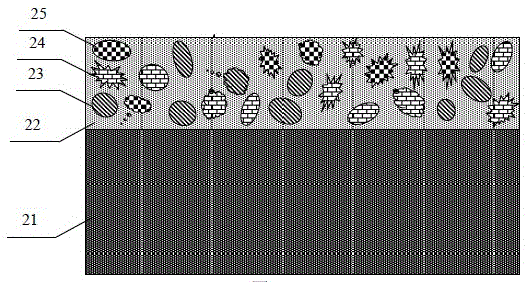
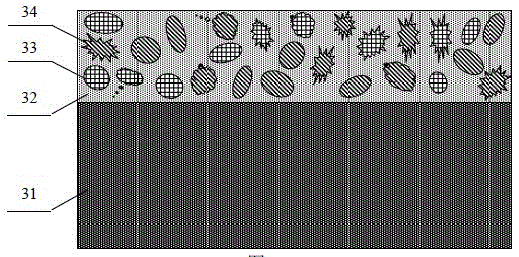
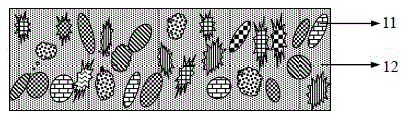
The invention discloses a physical non-cloning key for quantum secure authentication and quantum key distribution. The physical non-cloning key is composed of a substrate, a transparent dielectric film grown on the substrate, disordered micro nanoparticles embedded in the transparent dielectric film; and micro nanoparticles which are made of various kinds of materials, and are in various kinds of sizes and various kinds of shapes are mixed to form the disordered micro nanoparticles embedded in the transparent dielectric film. Compared with a physical non-cloning key formed by micro nanoparticles made of a single material, the physical non-cloning key of the invention has a more complicated microstructure and a spatially unevenly-distributed refractive index, can interact more complexly with incident light and generate a large authentication information speckle, and has higher security; compared with a physical non-cloning key which is of a porous structure and is directly formed by micro nanoparticles, the physical non-cloning key of the invention has higher stability and reliability, is insusceptible to interference and destruction of external environment and suitable for various kinds of substrates, and can be widely applied to quantum authentication and quantum key distribution.
Owner:INST OF ELECTRONICS ENG CHINA ACAD OF ENG PHYSICS
Quantum authentication encryption protocol suitable for quantum Email and based on double-photon entanglement state
The invention discloses a quantum authentication encryption protocol suitable for a quantum Email and based on a double-photon entanglement state. Two communicators Alice and Bob share two private keys for deciding double-photon entanglement state preparation in advance. The sender Alice sends a double-photon entanglement sequence encoded with classical bits of Alice to the receiver Bob in a one-step quantum transport manner. After receiving the encoded quantum state sequence, Bob decodes the classical bits of Alice by utilizing double-photon combined measurement and authenticates integrity of a secret of Alice with the help of a one-way hash function. The protocol disclosed by the invention only uses one-step quantum transport and not only does not need a public discussion, but also does not need a credible third party. Therefore, the protocol disclosed by the invention can be suitable for the situations, such as the quantum Email and the like, which only require the receiver to be positioned below the line. The protocol disclosed by the invention enables accuracy of massage authentication to be the level of 1 bit with the help of the one-way hash function. Moreover, the information theory efficiency of the protocol disclosed by the invention reaches 100 percent.
Owner:杭州百城科技有限公司
Novel anti-snooping luminous warning optical PUF
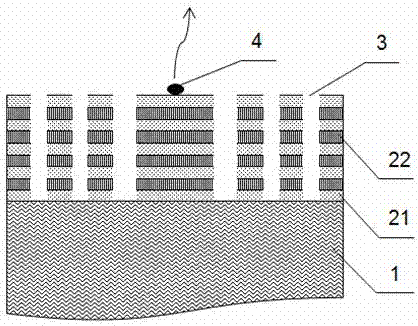
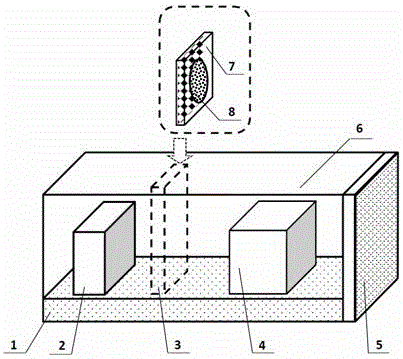
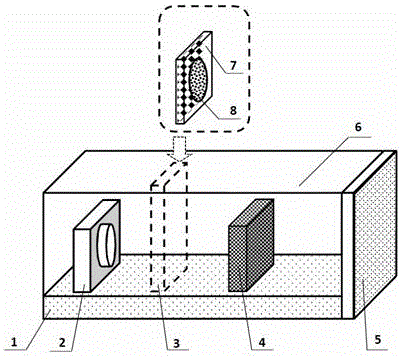
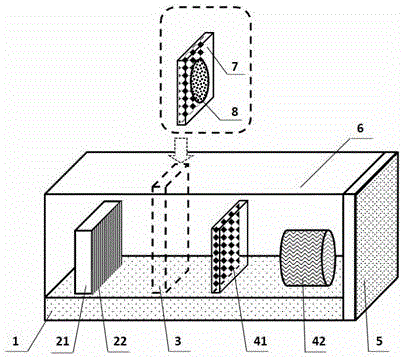
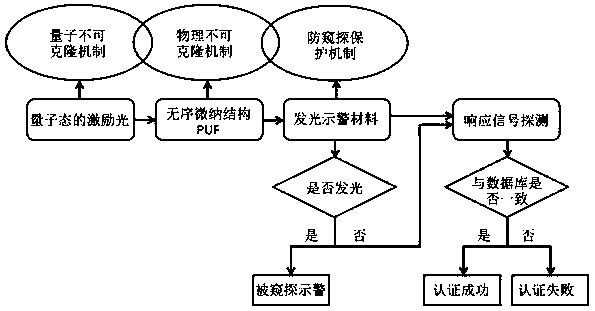
The invention discloses a novel anti-snooping luminous warning optical PUF. The novel anti-snooping luminous warning optical PUF structurally comprises a substrate, an optical PUF dielectric layer growing on the substrate, a long afterglow luminescent material capable of being embedded in the substrate or the optical PUF dielectric layer, and a non-transparent box for packaging the substrate, the optical PUF dielectric layer and the long afterglow luminescent material therein. According to the novel anti-snooping luminous warning optical PUF, the long afterglow luminescent material added into a conventional optical PUF structure still can continuously emit light for a long time after the material is irradiated through a light source for a short time and the light source is turned off, and the light emitting behavior is utilized as a basis for judging whether the PUF is snooped or not, so that the PUF is endowed with an anti-snooping luminous warning function and the defect that a general optical PUF cannot judge whether excitation-response pairs of the optical PUF are snooped by an enemy or not is overcome; the PUF has the anti-snooping luminous warning function, so that the security of the optical PUF is ensured; and therefore, the novel anti-snooping luminous warning optical PUF has true practicality and can be widely applied to quantum authentication and quantum key distribution.
Owner:INST OF ELECTRONICS ENG CHINA ACAD OF ENG PHYSICS
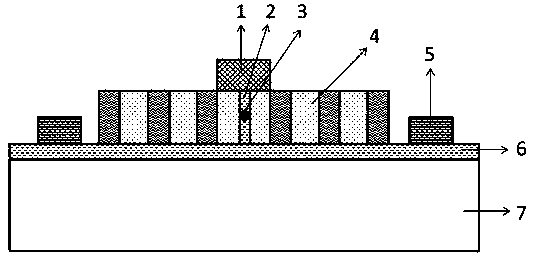
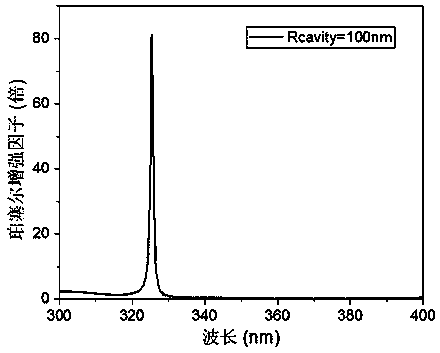
Ring cavity nano-wire electric injection single-photon source device
InactiveCN106784213AImprove radiation efficiencyEasy to couple and integrateSemiconductor devicesNanowireElectromagnetic field
Owner:INST OF ELECTRONICS ENG CHINA ACAD OF ENG PHYSICS
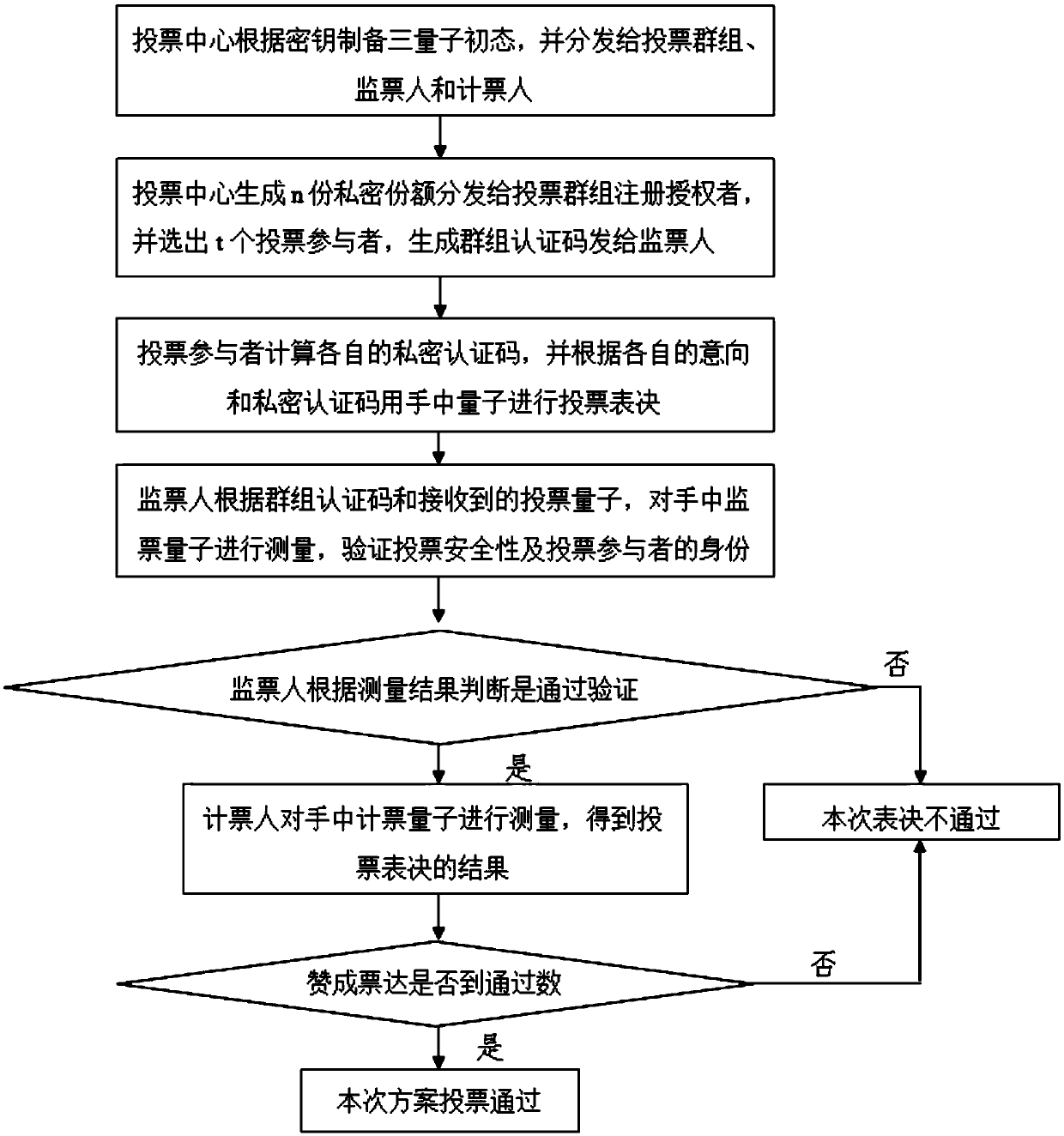
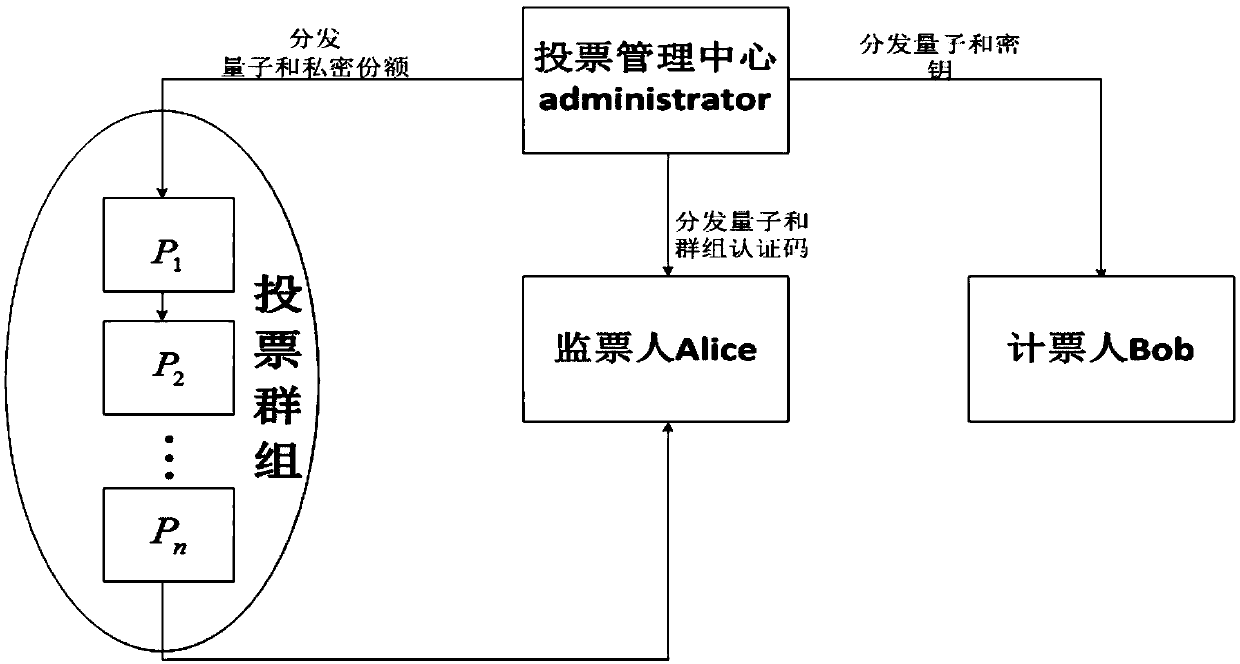
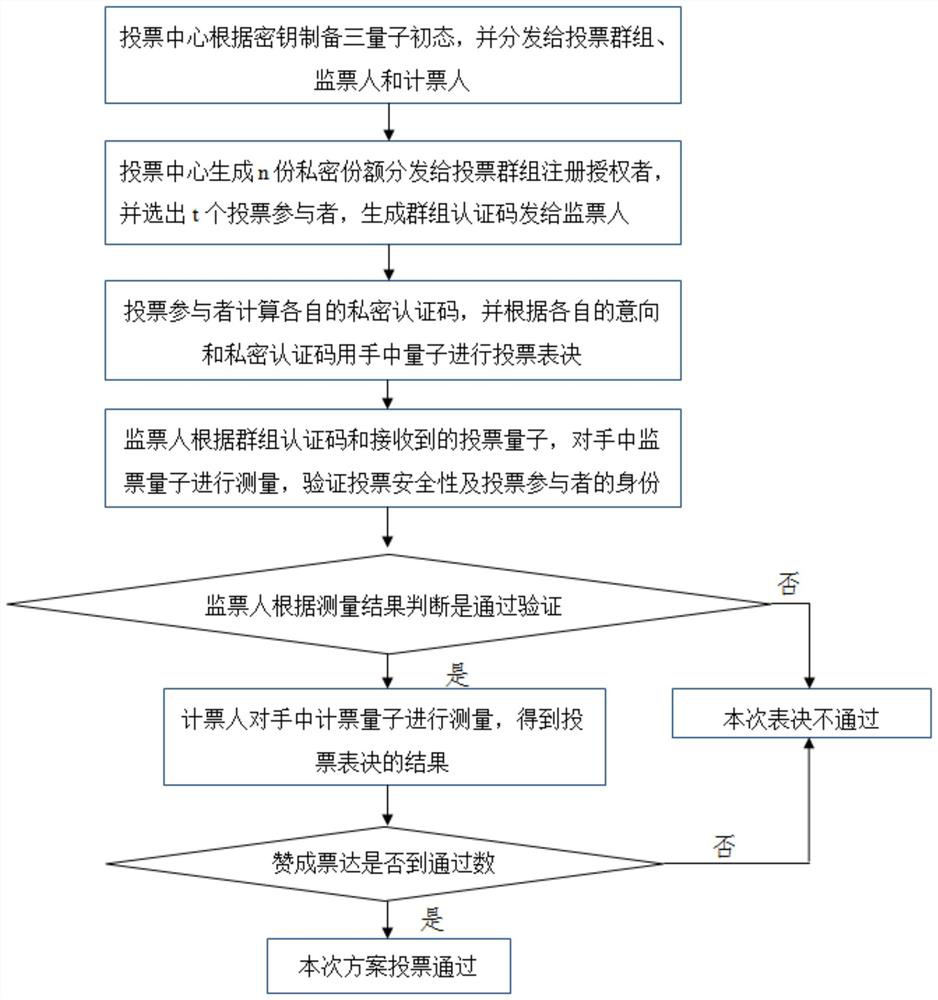
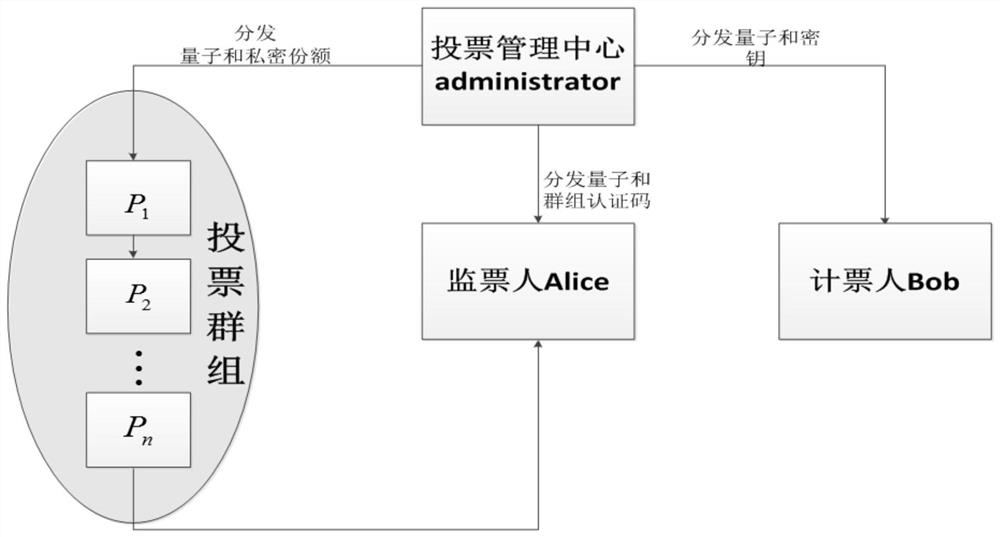
Voting protocol method based on d-dimensional three-quantum entanglement state
ActiveCN108737116AImprove information efficiencyEnsure safetyKey distribution for secure communicationUser identity/authority verificationQuantum entanglementQuantum computer
The invention provides a voting protocol method based on a d-dimensional three-quantum entanglement state, and belongs to the technical field of quantum computation and quantum authentication. The voting protocol method comprises the steps that a d-dimensional three-quantum entanglement system is prepared by a voting management center, three quanta are distributed to voting groups, a scrutineer and a vote counting person correspondingly, n private shares and group authentication codes a<0> are prepared simultaneously, the private shares are distributed to n voting group registered authorized persons, t persons with the voting qualification are selected from the voting groups to participate in voting, and the group authentication codes are issued to the scrutineer; the voting groups calculate the private authentication codes of the voting groups, and vote according to the voting intentions and the private authentication codes of the voting groups; after voting is completed, the scrutineer conducts unitary operation on the quanta in the hands through the group authentication codes in the hands, and authenticate safety through measuring; and after authentication is qualified, the votecounting person obtains a voting result. Compared with other protocols, the number of the quanta required to be prepared by the voting protocol method is much less, and thus the efficiency is improved, and the protocol flexibility and universality are enhanced by using any d-dimensional quantum state.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
Quantum authentication method for access control among three essential elements for cloud computing
ActiveCN105337727AImprove securityImprove reliabilityKey distribution for secure communicationUser identity/authority verificationMedia access controlQuantum authentication
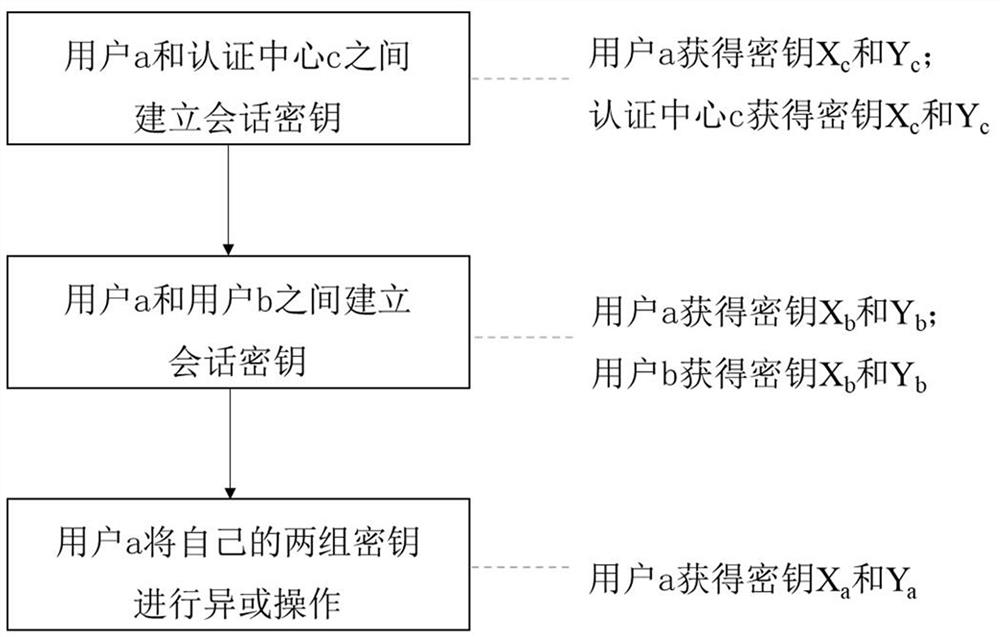
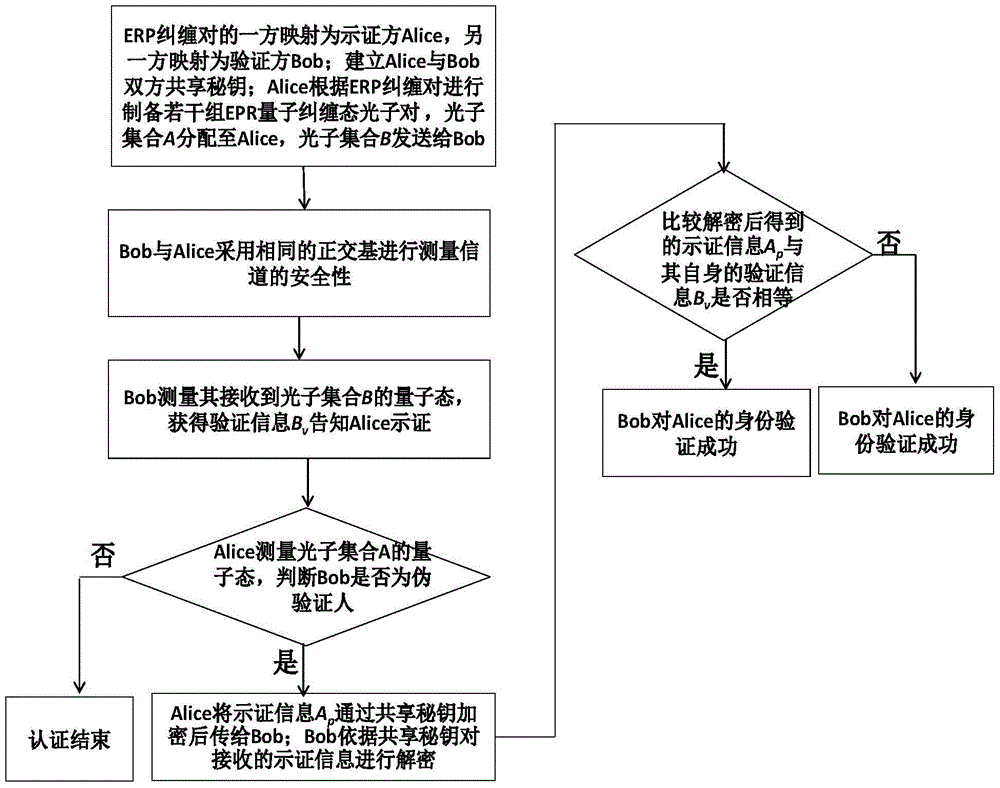
The invention discloses a quantum authentication method for access control among three essential elements for cloud computing. The three essential elements for cloud computing are a data owner Downer, a data user DUser and a cloud service provider CSP. The method comprises: setting the CSP and the DUser as an ERP (entangled pair) and enabling the CSP and the DUser to possess the same identity number legally, and performing mutual quantum authentication for the CSP and the DUser; setting the Downer and the CSP as an ERP and enabling the Downer and the CSP to possess the same identity number legally, and performing mutual quantum authentication for the Downer and the CSP; realizing successful quantum authentication among the Downer, the DUser and the CSP if the mutual quantum authentication between the CSP and the DUser and the mutual quantum authentication between the Downer and the CSP are successful; and quantum authentication among the Downer, the DUser and the CSP fails if the mutual quantum authentication between the CSP and the DUser and the mutual quantum authentication between the Downer and the CSP are not successful.
Owner:QINGDAO TECHNOLOGICAL UNIVERSITY
Miniature quantum authentication system
ActiveCN107196766AReduce volumeReduce the impactKey distribution for secure communicationUser identity/authority verificationPhoto irradiationEngineering
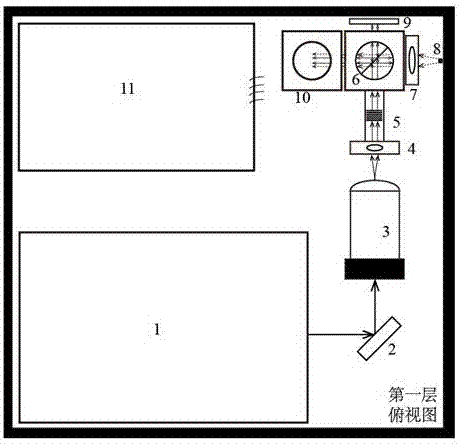
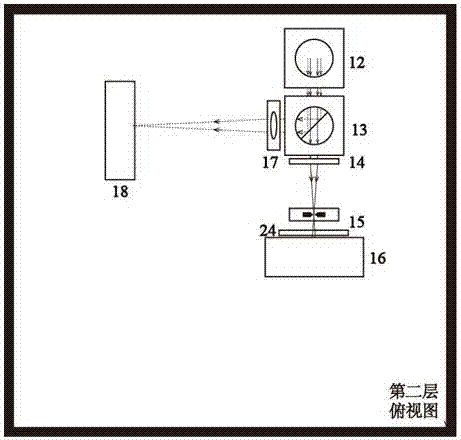
The invention provides a miniature quantum authentication system. The system prepares a single photon source by using a laser pulse attenuation method, encodes incident light waves by using a high-speed space light modulator, and irradiates the encoded light onto an optical PUF key composed of random media to generate speckle response, and processes the speckle by using the space light modulator to accomplish registration and authentication processes of the PUF key. According to the miniature quantum authentication system provided by the invention, the light path is folded on a three-dimensional direction, the volume of the whole authentication system is reduced by using a caged light path system, and commercialized equipment is adopted, so that the manufacturing cost is very low.
Owner:INST OF ELECTRONICS ENG CHINA ACAD OF ENG PHYSICS
Self-supporting physical unclonable key and preparation method thereof
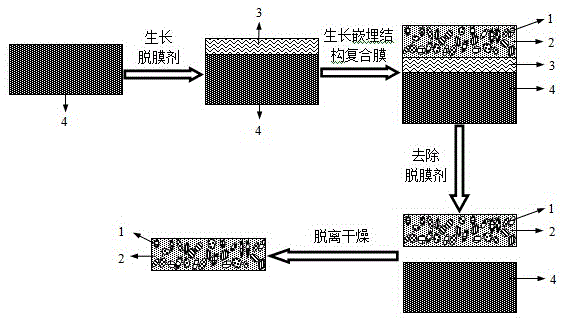
InactiveCN105471586AImprove stabilityImprove reliabilityKey distribution for secure communicationLiquid surface applicatorsEngineeringMicro nanoparticles
The invention discloses a self-supporting physical unclonable key and a preparation method thereof. The preparation method comprises the following steps: growing a release agent on a substrate, and growing a composite film formed by embedding disordered micro / nano-particles into a transparent medium on a release agent layer; and dissolving the release agent with a solvent, taking the composite film removed by the solvent out, and drying the composite film to obtain the self-supporting physical unclonable key formed by embedding the disordered micro / nano-particles into the transparent medium. The self-supporting physical unclonable key has high stability and high reliability, and is suitable for serving as a self-supporting structure. The preparation method is low in cost, simple, convenient and feasible, and has practicability. The obtained self-supporting physical unclonable key is small in size and not limited by any substrate, and can be transferred onto various substrates to use and embedded into a conventional security authentication card or directly applied to highly-integrated quantum authentication and quantum key distribution microsystems.
Owner:INST OF ELECTRONICS ENG CHINA ACAD OF ENG PHYSICS
Secure Quantum Authentication System
ActiveUS20130275757A1Key distribution for secure communicationUser identity/authority verificationComputer hardwareQuantum authentication
A method and apparatus for sharing information. First bits are selected from a shared secret key in a first device. The first bits have a selected length. Second bits with the selected length in signals are sent from the first device to a second device. The signals have selected types of properties based on the first bits. The second bits are encoded in states for the selected types of properties. A key is generated in the first device. The key is based on the second bits received at the second device having the selected types of properties identified as matching expected types of properties.
Owner:THE BOEING CO
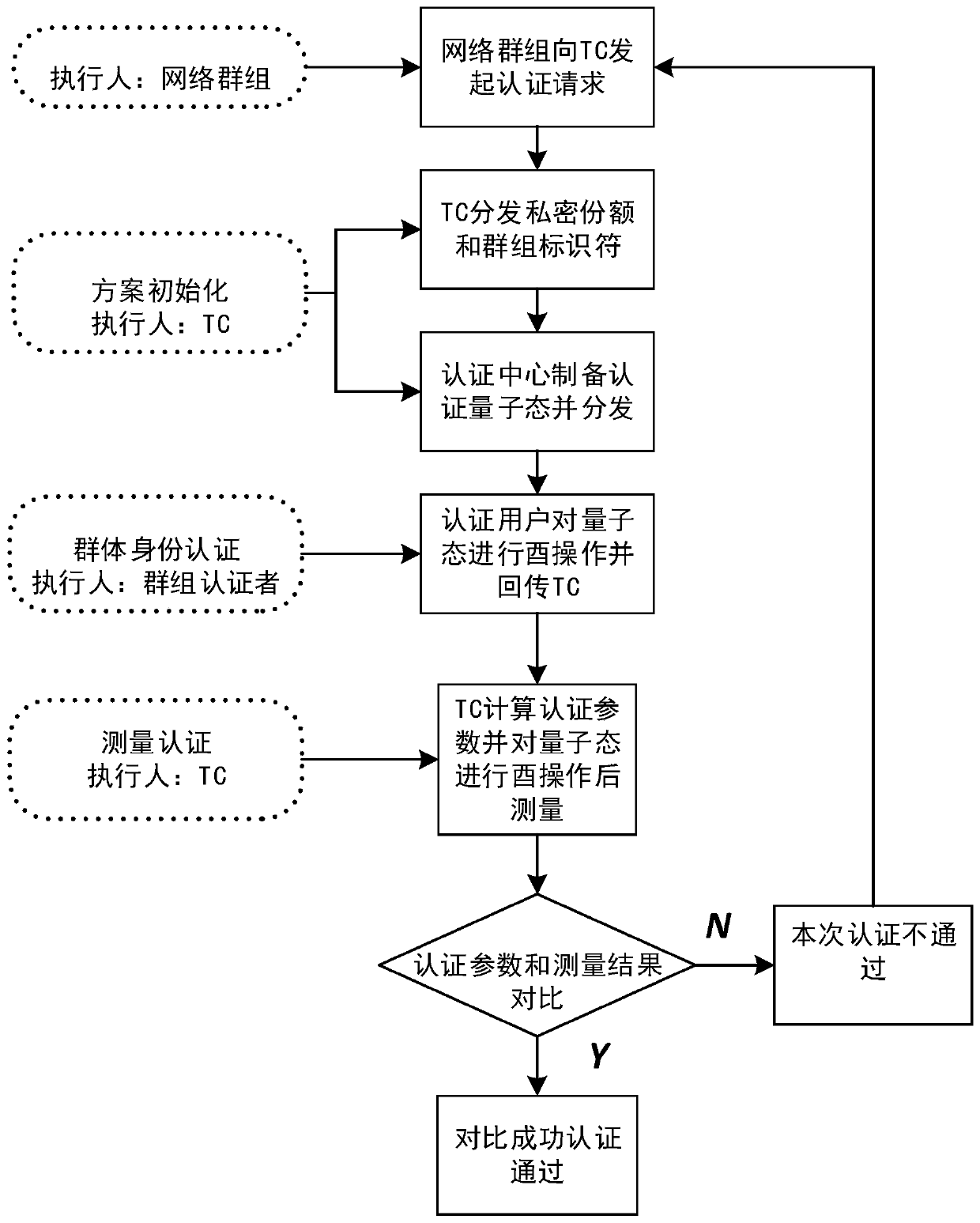
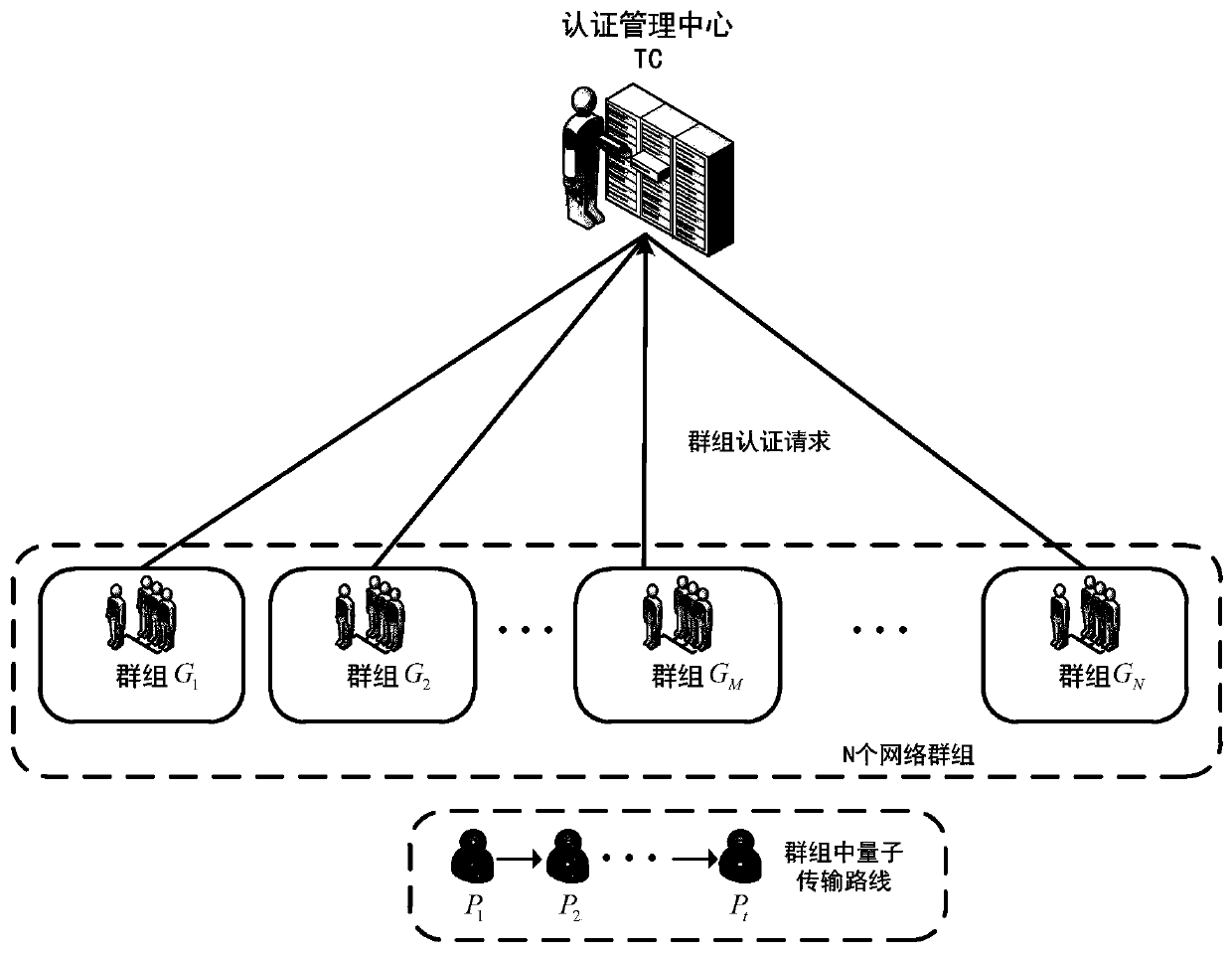
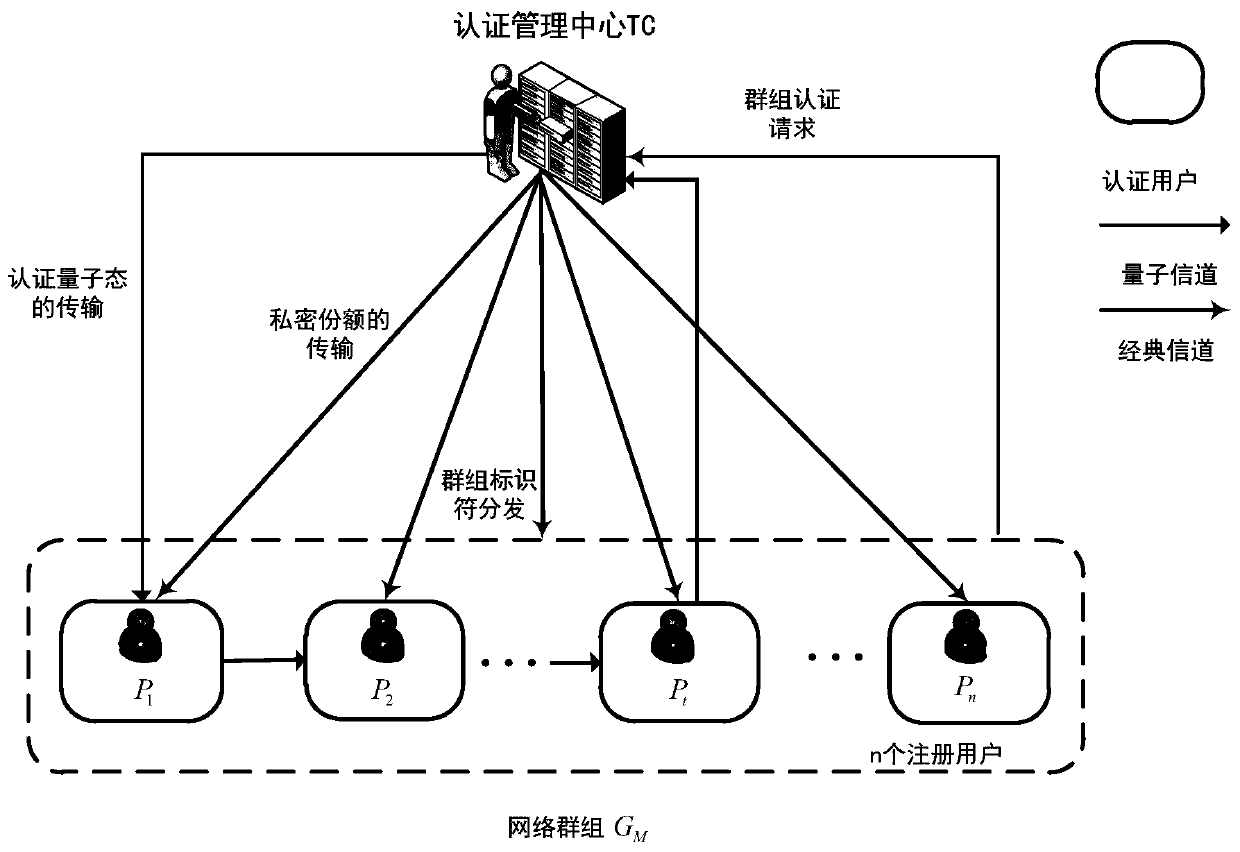
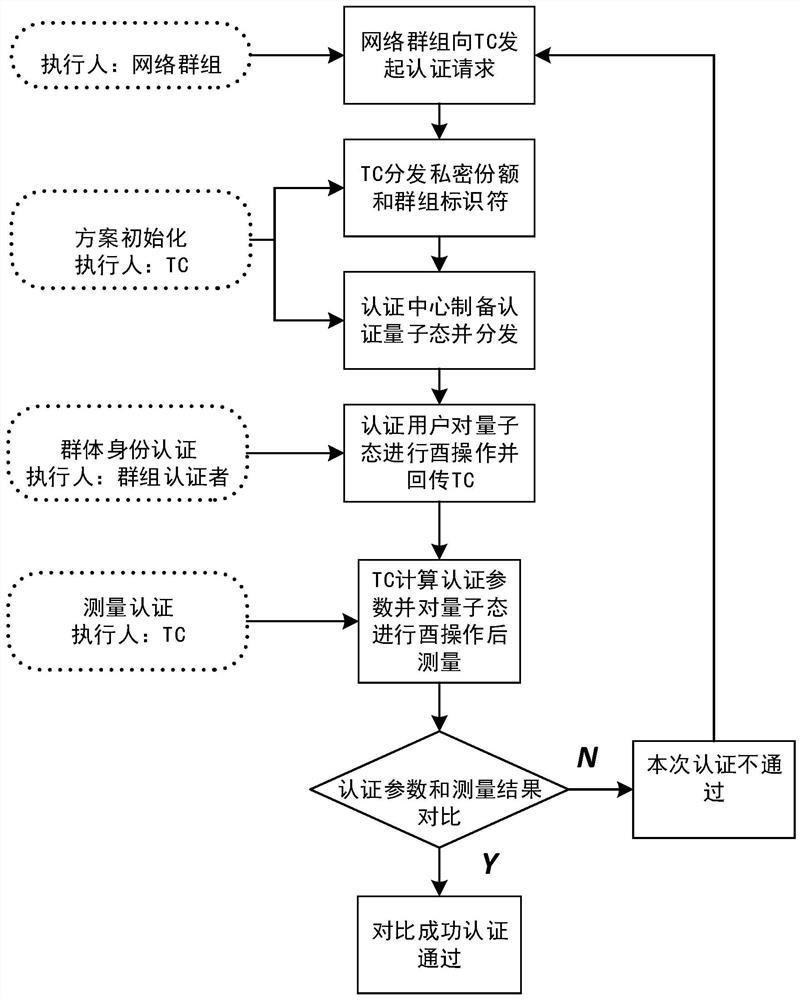
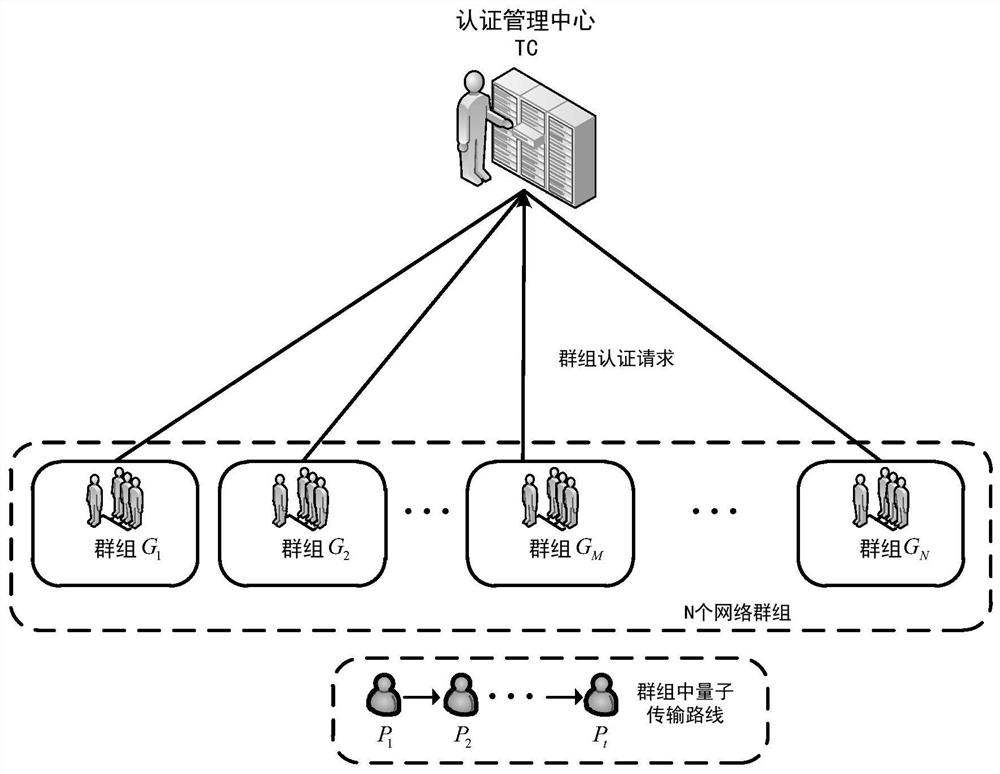
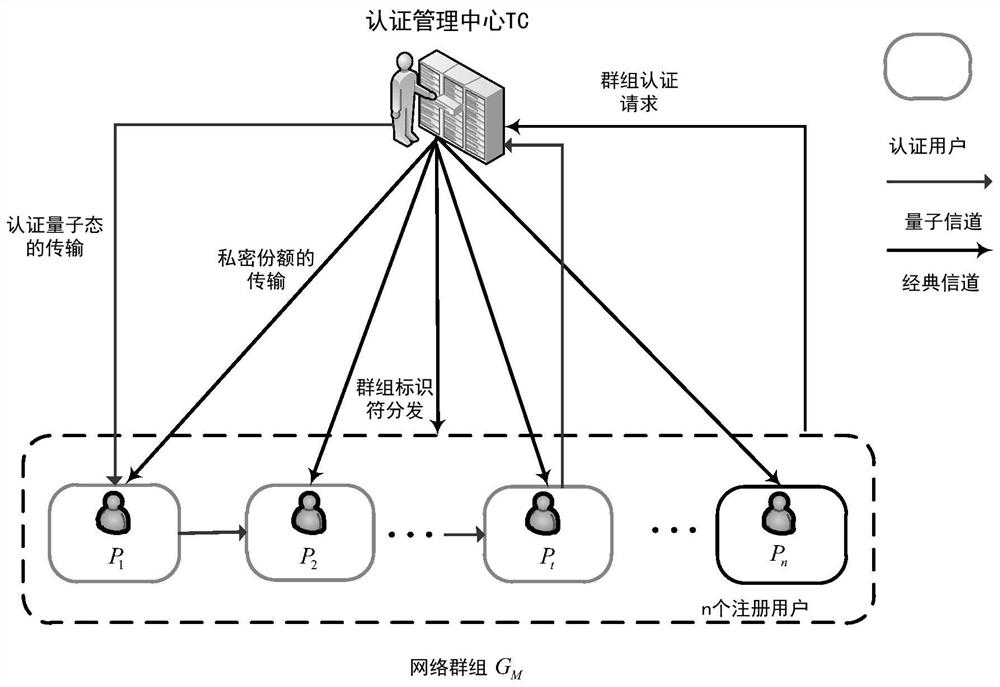
Quantum group authentication method based on Grover algorithm
ActiveCN110336775AImprove applicabilityReduce the number of transfersKey distribution for secure communicationUser identity/authority verificationQuantum channelGrover's algorithm
The invention belongs to the technical field of quantum computing and quantum authentication, and relates to a quantum group authentication method based on a Grover algorithm. The method comprises thesteps that an authentication management center prepares an initial authentication quantum state; the private shares are sent to a network group needing to be authenticated through a safe quantum channel, then the private shares are prepared to serve as registered user identity information and sent to a registered user through a classic channel, and a group identifier is generated for the networkgroup and sent to the network group through the classic channel; in the authentication stage, each user participating in authentication performs unitary transformation on the authentication quantum state according to own identity information and the group identifier, and finally, the group transmits the authentication quantum state after unitary transformation back to the authentication managementcenter for comparison to obtain an authentication result. According to the invention, the Grover operator is used, the usage of the Grover operator is expanded, the group user identity and the network group identifier can be authenticated at the same time, and the security of the authentication method is improved through dual authentication.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
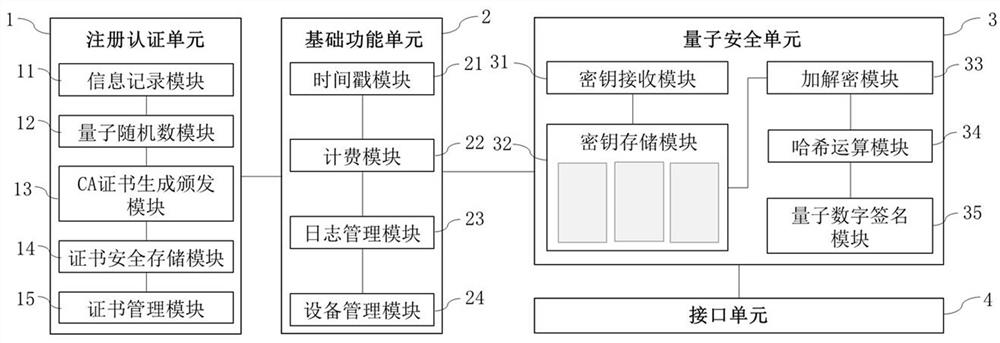
Digital certificate generation method, identity authentication method, quantum CA authentication center and quantum CA authentication system
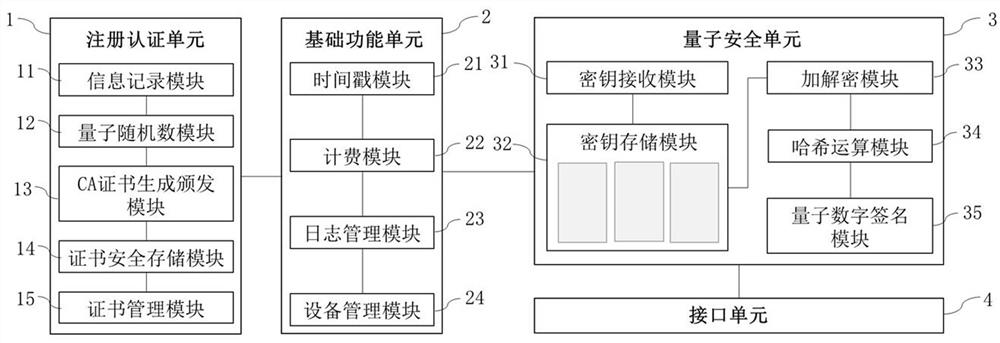
ActiveCN114254284AImprove securityConvenient certificate managementQuantum computersDigital data protectionInternet privacyDigital signature
The invention provides a digital certificate generation method, an identity authentication method, a quantum CA authentication center and a quantum CA authentication system, and each CA authentication center is used for providing a message authenticity authentication function, namely a quantum digital signature service based on trusted identity authentication. The CA authentication center comprises a registration authentication unit, a basic function unit, a quantum security unit and an interface unit which are connected in sequence. When a signature is initiated between two users, a CA authentication center and two communication parties jointly form a message authenticity verification system, firstly, a signer requests one identity authentication from the CA authentication center, and then quantum security verification is completed on the authenticity of a sent message through the processes of secret key preparation, signature generation and signature verification. And completing the quantum digital signature. According to the invention, the CA needs to issue a trusted identity certificate to each user, but the certificate does not need to be bound with a secret key for verifying the signature, so that the certificate management of the CA with quantum security is more convenient.
Owner:NANJING UNIV +1
A new type of anti-peeping light-emitting warning optical puf
Owner:INST OF ELECTRONICS ENG CHINA ACAD OF ENG PHYSICS
A ring-cavity nanowire electrical injection single photon source device
InactiveCN106784213BImprove radiation efficiencyEasy to couple and integrateSemiconductor devicesNanowireElectromagnetic field
Owner:INST OF ELECTRONICS ENG CHINA ACAD OF ENG PHYSICS
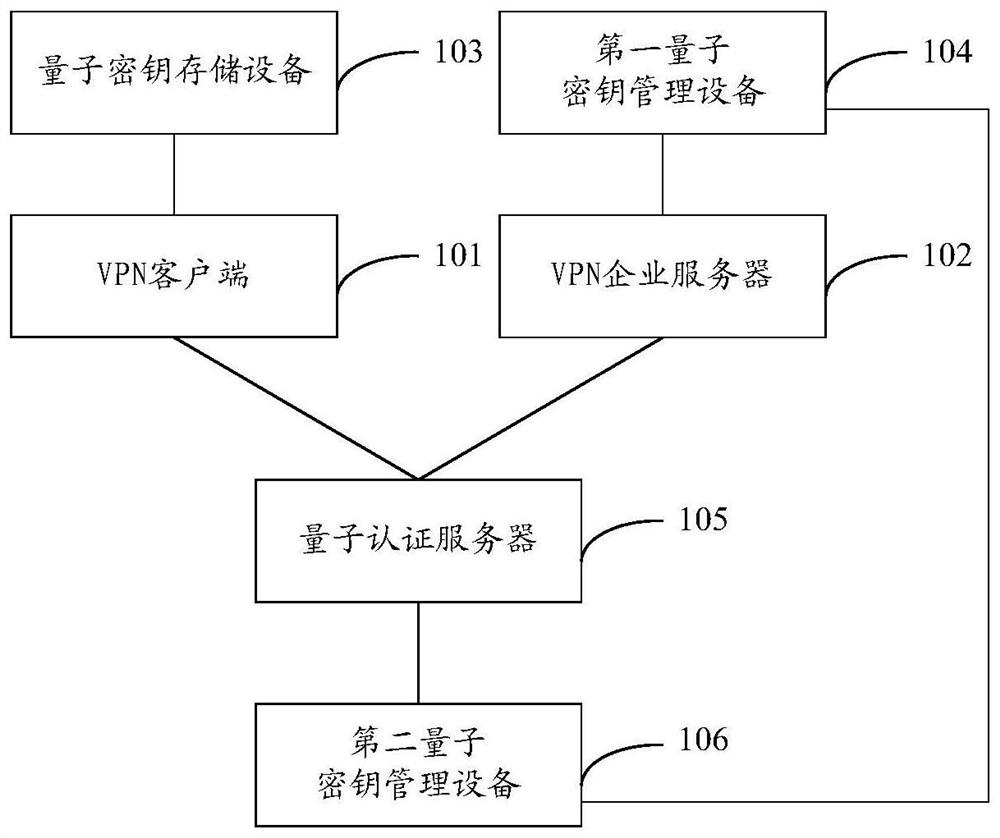
Method, device and system for identity authentication
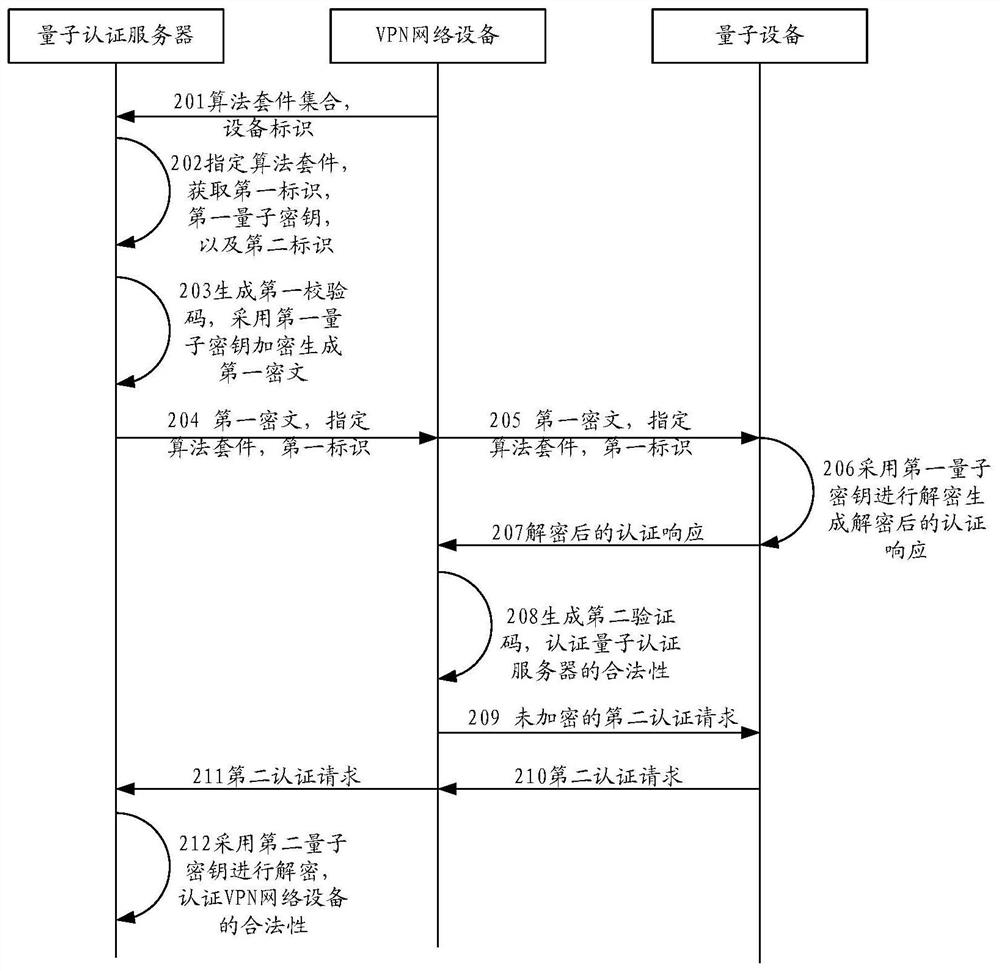
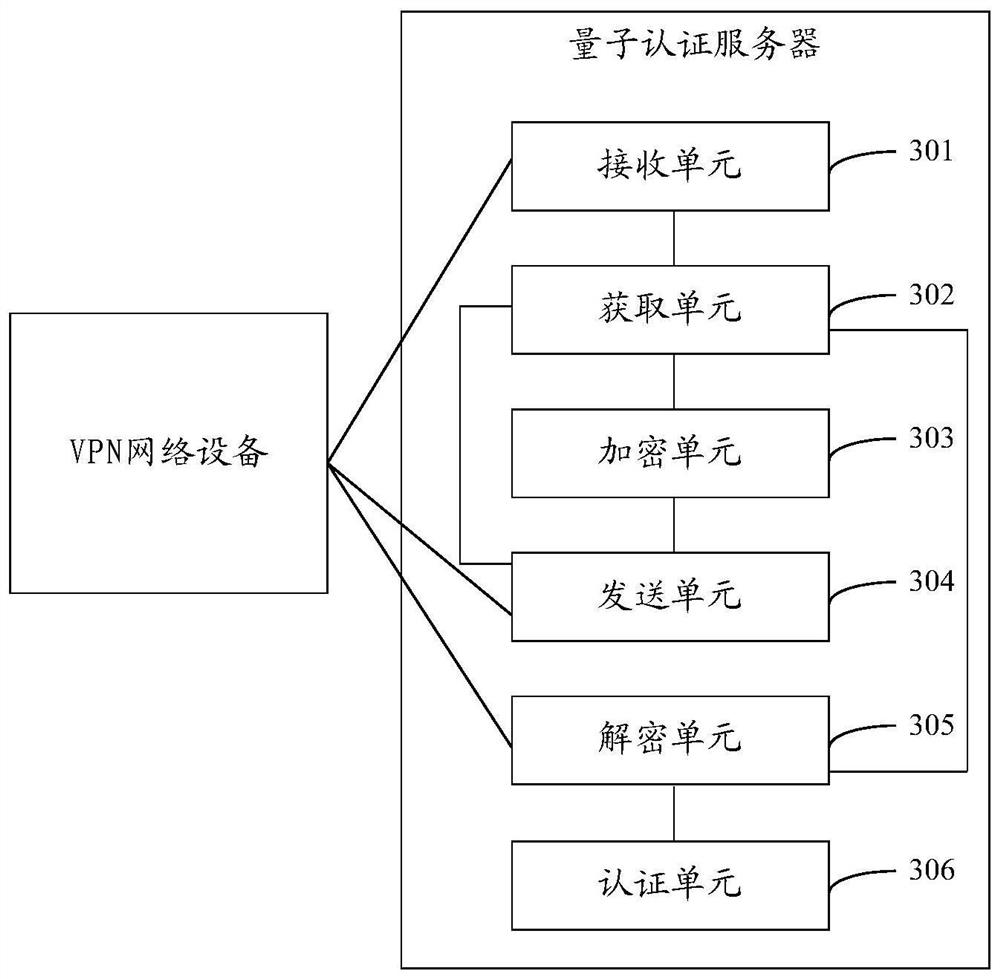
The invention provides a method, device and system for identity authentication. A quantum authentication server receives a first authentication request sent by a VPN network device, uses a first quantum key to encrypt to obtain a first ciphertext, and returns an authentication response to the VPN network device. The VPN network device uses the first quantum key to decrypt the first ciphertext in the authentication response, obtains the first check code, and generates the second check code. When the first check code and the second check code are the same, the quantum The identity authentication of the authentication server is passed. The VPN network device uses the second quantum key to encrypt to obtain the second ciphertext, and sends the second authentication request to the quantum authentication server. The quantum authentication server decrypts the second ciphertext in the second authentication request, obtains the third check code, and generates the fourth check code. When the third check code is the same as the fourth check code, the identity of the VPN network device Certification passed. In the above identity authentication process, a quantum key is used for encryption, which improves the security of identity authentication.
Owner:QUANTUMCTEK GUANGDONG CO LTD
Digital certificate generation, identity authentication method and quantum ca authentication center and system
ActiveCN114254284BImprove securityConvenient certificate managementQuantum computersDigital data protectionDigital signatureEngineering
The present invention proposes a digital certificate generation, identity authentication method, quantum CA authentication center and system, each CA authentication center is used to provide message authenticity authentication function, that is, quantum digital signature service based on credible identity authentication, the CA authentication center It includes a registration authentication unit, a basic function unit, a quantum security unit and an interface unit connected in sequence. When a signature is initiated between two users, the CA certification center and the communication parties jointly constitute a message authenticity verification system. First, the signer requests the CA certification center for "one identity at a time" authentication, and then prepares a key, generates a signature, and verifies the signature These several processes complete the quantum security verification of the authenticity of the sent message and complete the quantum digital signature. The CA certification center of the present invention needs to issue a trusted identity certificate to each user, but the certificate does not need to be bound with the key for verifying the signature, so the certificate management of the quantum-safe CA center is more convenient.
Owner:NANJING UNIV +1
A Quantum Swarm Authentication Method Based on Grover Algorithm
ActiveCN110336775BImprove applicabilityReduce the number of transfersKey distribution for secure communicationUser identity/authority verificationAlgorithmTheoretical computer science
The invention belongs to the technical field of quantum computing and quantum authentication, and relates to a quantum group authentication method based on the Grover algorithm. A private share is used as the identity information of the registered user and sent to the registered user through the classic channel, and a group identifier is generated for the network group and sent to the network group through the classic channel; in the authentication stage, each user participating in the authentication according to his own identity information Carry out unitary transformation to the authentication quantum state with the group identifier, and finally the group returns the authentication quantum state after the unitary transformation to the authentication management center for comparison to obtain the authentication result; the present invention uses the Grover operator, and the Grover operator The usage of the system has been extended, and the group user identity and the network group identifier can be authenticated at the same time, and the double authentication improves the security of the authentication method.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
A voting protocol method based on d-dimensional three-dimensional quantum entanglement
ActiveCN108737116BImprove information efficiencyEnsure safetyKey distribution for secure communicationUser identity/authority verificationQuantum entanglementTheoretical computer science
The invention provides a voting protocol method based on a d-dimensional three-quantum entanglement state, and belongs to the technical field of quantum computation and quantum authentication. The voting protocol method comprises the steps that a d-dimensional three-quantum entanglement system is prepared by a voting management center, three quanta are distributed to voting groups, a scrutineer and a vote counting person correspondingly, n private shares and group authentication codes a<0> are prepared simultaneously, the private shares are distributed to n voting group registered authorized persons, t persons with the voting qualification are selected from the voting groups to participate in voting, and the group authentication codes are issued to the scrutineer; the voting groups calculate the private authentication codes of the voting groups, and vote according to the voting intentions and the private authentication codes of the voting groups; after voting is completed, the scrutineer conducts unitary operation on the quanta in the hands through the group authentication codes in the hands, and authenticate safety through measuring; and after authentication is qualified, the votecounting person obtains a voting result. Compared with other protocols, the number of the quanta required to be prepared by the voting protocol method is much less, and thus the efficiency is improved, and the protocol flexibility and universality are enhanced by using any d-dimensional quantum state.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
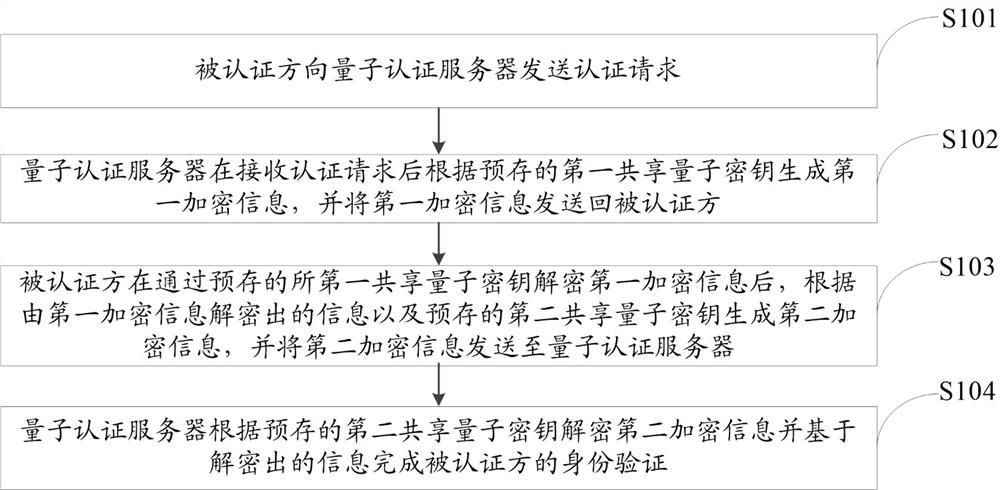
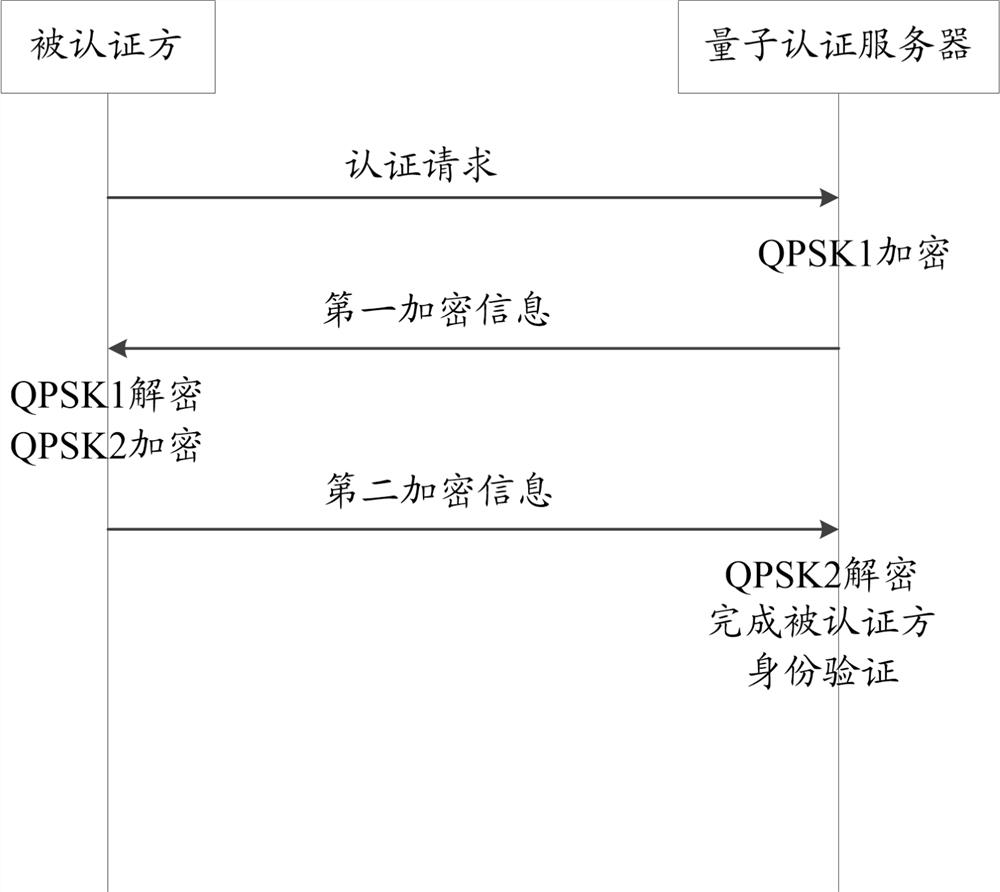
Authentication method, device and storage medium
ActiveCN114362967BImprove securityHigh anti-quantum computing abilityKey distribution for secure communicationUser identity/authority verificationInternet privacyQuantum authentication
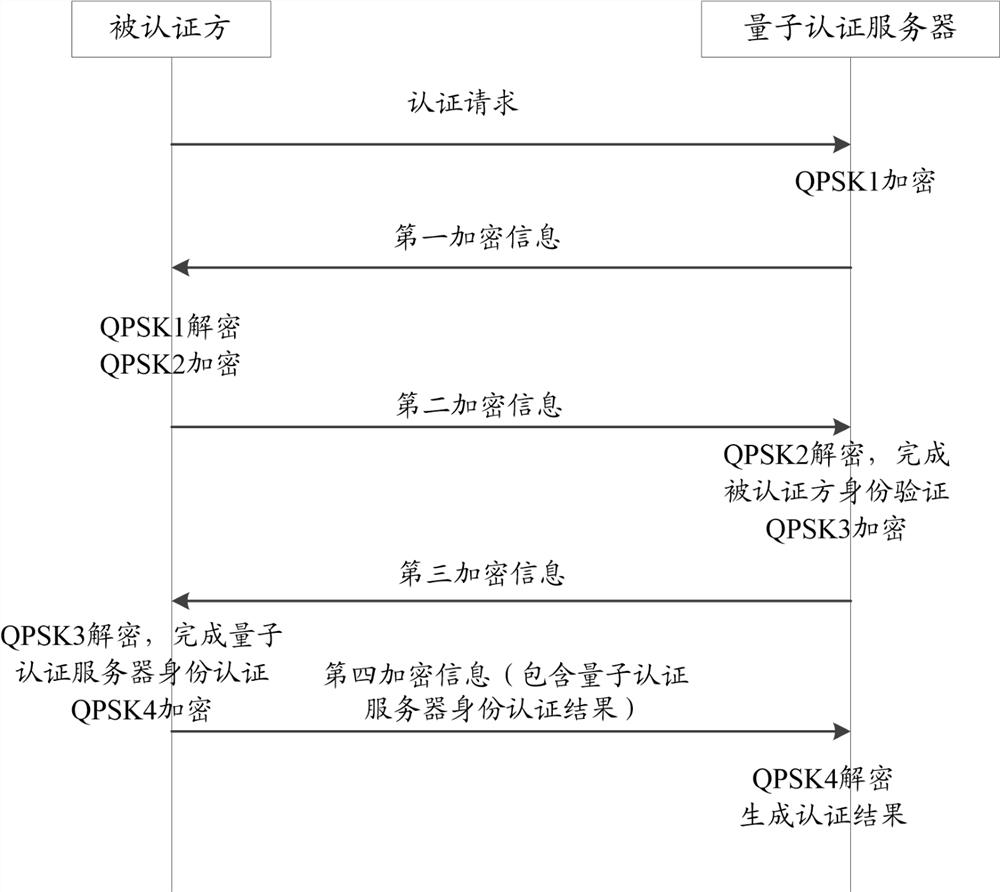
The invention discloses an authentication method, device, and storage medium, wherein the method includes: the authenticated party sends an authentication request to a quantum authentication server, and the quantum authentication server generates a second quantum authentication according to a prestored first shared quantum key after receiving the authentication request. Encrypted information, and send the first encrypted information back to the authenticated party, after the authenticated party decrypts the first encrypted information through the pre-stored first shared quantum key, according to the information decrypted by the first encrypted information and the pre-stored The second shared quantum key generates the second encrypted information, and sends the second encrypted information to the quantum authentication server, and the quantum authentication server decrypts the second encrypted information according to the prestored second shared quantum key and completes the encrypted information based on the decrypted information. Authentication of the authenticating party. In the technical solution disclosed in the present invention, the mutual information is encrypted and decrypted through the pre-stored shared quantum key, thereby significantly improving the security of information mutual exchange.
Owner:南京易科腾信息技术有限公司
Quantum authentication method for access control among three elements of cloud computing
ActiveCN105337727BImprove securityImprove reliabilityKey distribution for secure communicationUser identity/authority verificationService provisionQuantum authentication
The invention discloses a quantum authentication method for access control between three elements of cloud computing, the three elements of cloud computing are data owner DOwner, data user DUser and cloud service provider CSP, including setting CSP and DUser as ERP entanglement pair and legally have the same ID number, conduct mutual quantum authentication between CSP and DUser; set DOwner and CSP as ERP entangled pairs and legally have the same ID number, and perform mutual quantum authentication between DOwner and CSP; when CSP and CSP When the mutual quantum authentication between DUser and the mutual quantum authentication between DOwner and CSP is successful, the quantum authentication between DOwner, DUser and CSP is successful; otherwise, the quantum authentication between DOwner, DUser and CSP fails .
Owner:QINGDAO TECHNOLOGICAL UNIVERSITY
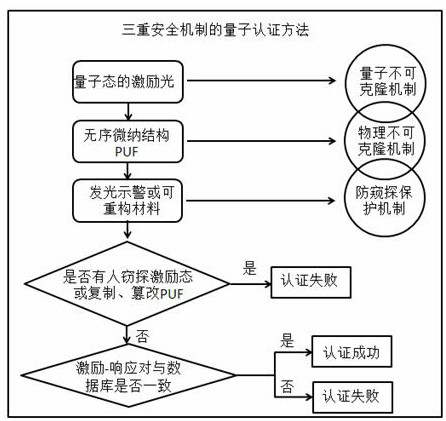
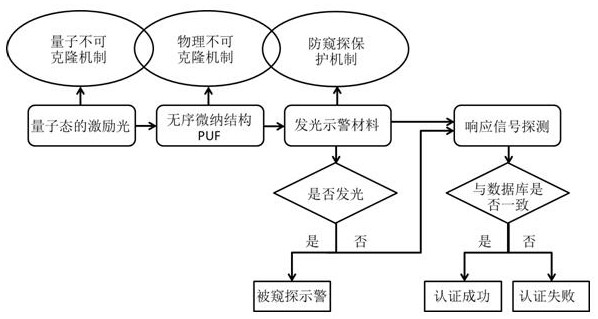
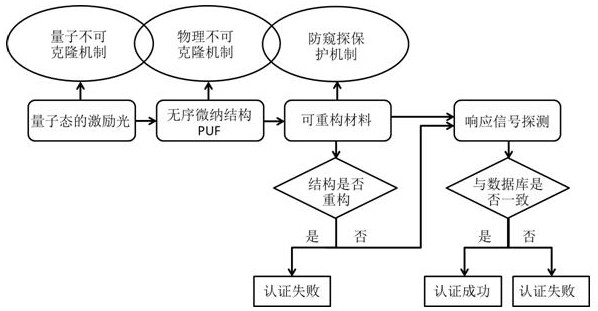
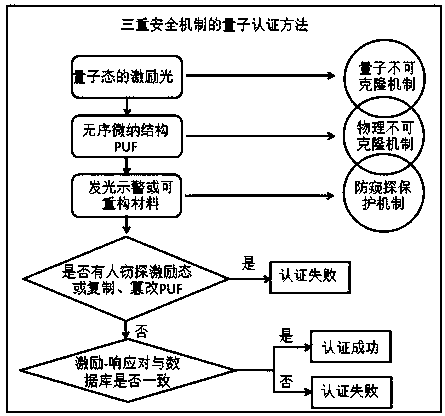
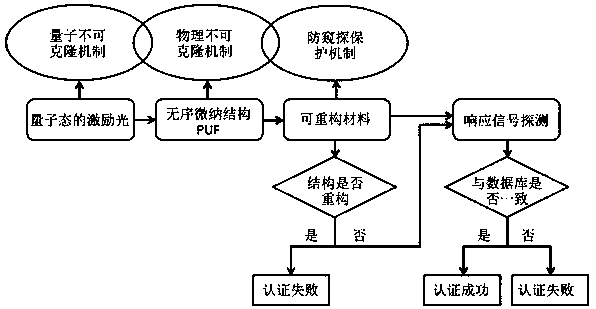
A quantum authentication method with triple security mechanism
InactiveCN108075898BProtection securityImprove security and credibilityUser identity/authority verificationPhotonic quantum communicationComputer hardwareProtection mechanism
The invention discloses a quantum authentication method of a triple security mechanism, which particularly relates to a quantum unclonable mechanism, a physical unclonable mechanism and an anti-peeping protection mechanism. The method comprises the following steps: firstly, quantum light is adopted as excitation, a collapse principle is measured according to a quantum state, an eavesdropper cannotknow the excitation state under an unchanging condition, and the quantum unclonable mechanism is followed; secondly, a quantum key composed of millions of disordered nano particles is adopted, cloning cannot be realized on a technology, and physical no-cloning is realized; a light-emitting warning or a reconfigurable material is added into the quantum key, illegal copying or tampering can enablethe quantum key to give out a warning or structure reconstruction, so that a legal user can be known, and timely abandon is realized to ensure the security of the legal user to form the anti-peeping protection mechanism. The quantum authentication method based on the triple security mechanism can be widely applied to the fields with extremely high requirements on identity authentication such as security authentication, quantum encryption, banks, finance and the like.
Owner:INST OF ELECTRONICS ENG CHINA ACAD OF ENG PHYSICS
Mobile phone token identity authentication system and method based on quantum cryptography network
ActiveCN106712931BUnconditionally safeEnsure safetyKey distribution for secure communicationUser identity/authority verificationDomain nameApplication server
Owner:QUANTUMCTEK SHANGHAI CO LTD
Quantum authentication encryption method based on two-photon entanglement state suitable for quantum email
Owner:杭州百城科技有限公司
Quantum authentication method of triple security mechanism
InactiveCN108075898AProtection securityImprove security and credibilityUser identity/authority verificationPhotonic quantum communicationProtection mechanismQuantum gate
The invention discloses a quantum authentication method of a triple security mechanism, which particularly relates to a quantum unclonable mechanism, a physical unclonable mechanism and an anti-peeping protection mechanism. The method comprises the following steps: firstly, quantum light is adopted as excitation, a collapse principle is measured according to a quantum state, an eavesdropper cannotknow the excitation state under an unchanging condition, and the quantum unclonable mechanism is followed; secondly, a quantum key composed of millions of disordered nano particles is adopted, cloning cannot be realized on a technology, and physical no-cloning is realized; a light-emitting warning or a reconfigurable material is added into the quantum key, illegal copying or tampering can enablethe quantum key to give out a warning or structure reconstruction, so that a legal user can be known, and timely abandon is realized to ensure the security of the legal user to form the anti-peeping protection mechanism. The quantum authentication method based on the triple security mechanism can be widely applied to the fields with extremely high requirements on identity authentication such as security authentication, quantum encryption, banks, finance and the like.
Owner:INST OF ELECTRONICS ENG CHINA ACAD OF ENG PHYSICS
A quantum key automatic filling method and system adapted to electric power business
ActiveCN109412794BImplement updateImprove the level of practicalityKey distribution for secure communicationStationEngineering
The invention discloses a quantum key automatic charging method and system adapted to electric power business, complies with the deployment architecture of power business master station convergence and power business terminal access, and divides quantum key into quantum authentication key, quantum encryption key key and quantum update key, the quantum authentication key is used for identity authentication during communication interaction, the quantum encryption key is used for encryption and decryption of data during communication interaction, and the quantum update key is used to update the quantum authentication key and quantum encryption key And / or when the quantum key is updated, the encryption and decryption of the new quantum key in the communication interaction. Quantum authentication, encryption and / or updating keys are updated through quantum updating keys, so as to realize automatic filling and updating of quantum keys.
Owner:南京南瑞网络安全技术有限公司 +2
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com