A quantum authentication method with triple security mechanism
A technology of authentication method and security mechanism, applied in secure communication devices, photon quantum communication, user identity/authority verification, etc., can solve problems such as hidden dangers, inability to know hackers' quantum keys, illegal snooping, and limited detection accuracy of authentication systems. Achieving the effect of security protection and improving security and credibility
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
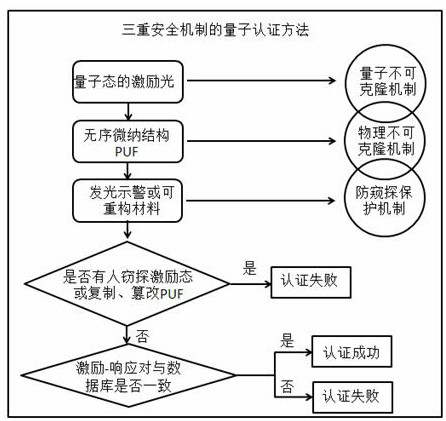
[0022] A quantum authentication method based on the triple security mechanism of fluorescent anti-spy PUF, such as figure 2 As shown, the authentication process is as follows:
[0023] First, an attenuation of the quantum light source by a pulsed laser produces excitation light in an unclonable quantum state. Different excitation states can be generated by adjusting the spatial intensity or spatial phase of the quantum excitation source.
[0024] Secondly, the excitation light in the quantum state passes through the physically unclonable function (PUF) entity composed of disordered micro-nano structures, and a long-lasting luminescent warning material is added to the PUF entity. When the PUF is peeped by an external illegal excitation light, it will emit light to warn, so that the authentication cannot pass; otherwise, continue to the next step.
[0025] Finally, the detector decodes and detects the generated disordered scattering response signal, and compares it with the s...
Embodiment 2
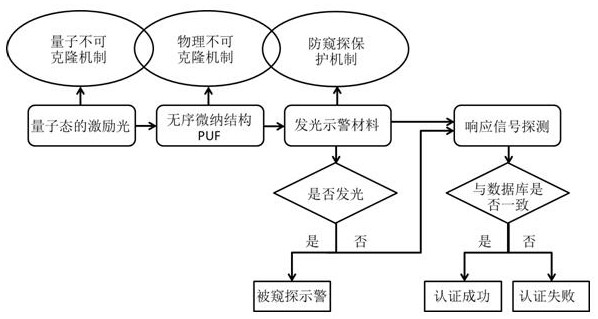
[0027] A quantum authentication method based on the triple security mechanism of reconfigurable PUF, such as image 3 As shown, the authentication process is as follows:
[0028] First, an unclonable quantum state of excitation light is generated by a quantum dot single-photon source. Different excitation states can be generated by adjusting the spatial intensity or spatial phase of the quantum excitation source.
[0029] Secondly, the excitation light of the quantum state passes through the physical unclonable function (PUF) entity composed of disordered micro-nano structure, and the reconfigurable material is added to the PUF entity by adding low melting point metal nanoparticles. When the PUF is spied on by external illegal excitation light, if the wavelength is inconsistent with the set wavelength, it will generate localized heating to the low-melting point metal nanoparticles to melt and deform, so that the disordered micro-nano structure is reconstructed, so that the ex...
Embodiment 3
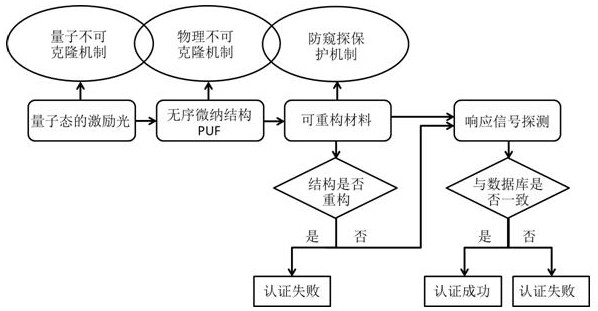
[0033] A quantum authentication method based on fluorescent anti-spying and reconfigurable PUF triple security mechanism, such as Figure 4 As shown, the authentication process is as follows:
[0034] A fluorescent anti-spying and reconfigurable PUF is used, so on the basis of Embodiment 1 and Embodiment 2, if someone spy on the quantum excitation state, the excitation photon will collapse due to the collapse of the quantum state during the measurement of the excitation state. If the PUF cannot be reached or the number of photons decreases, the authentication will fail and play a role of security protection.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com