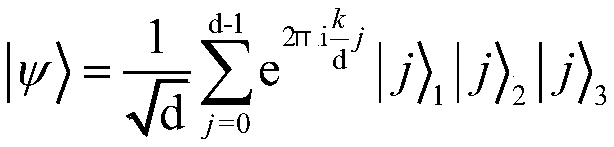Voting protocol method based on d-dimensional three-quantum entanglement state
A quantum entangled state and quantum entanglement technology, applied in key distribution, can solve the problems of only considering the security of voting information and low efficiency, and achieve the effect of ensuring security and high information efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
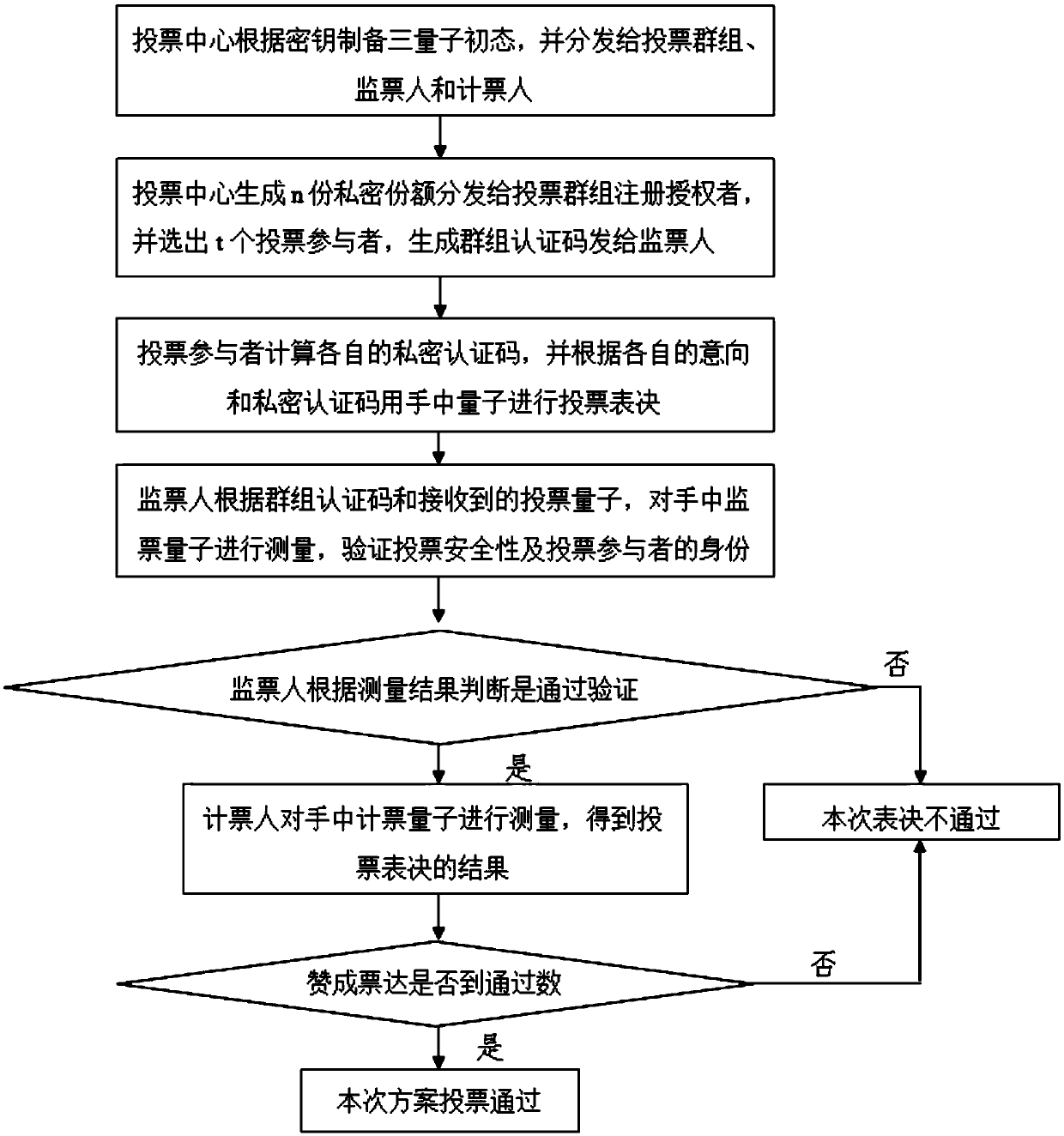
[0038] A d-dimensional three-quantum entangled state-based voting protocol method of the present invention will be further described below in conjunction with the accompanying drawings.
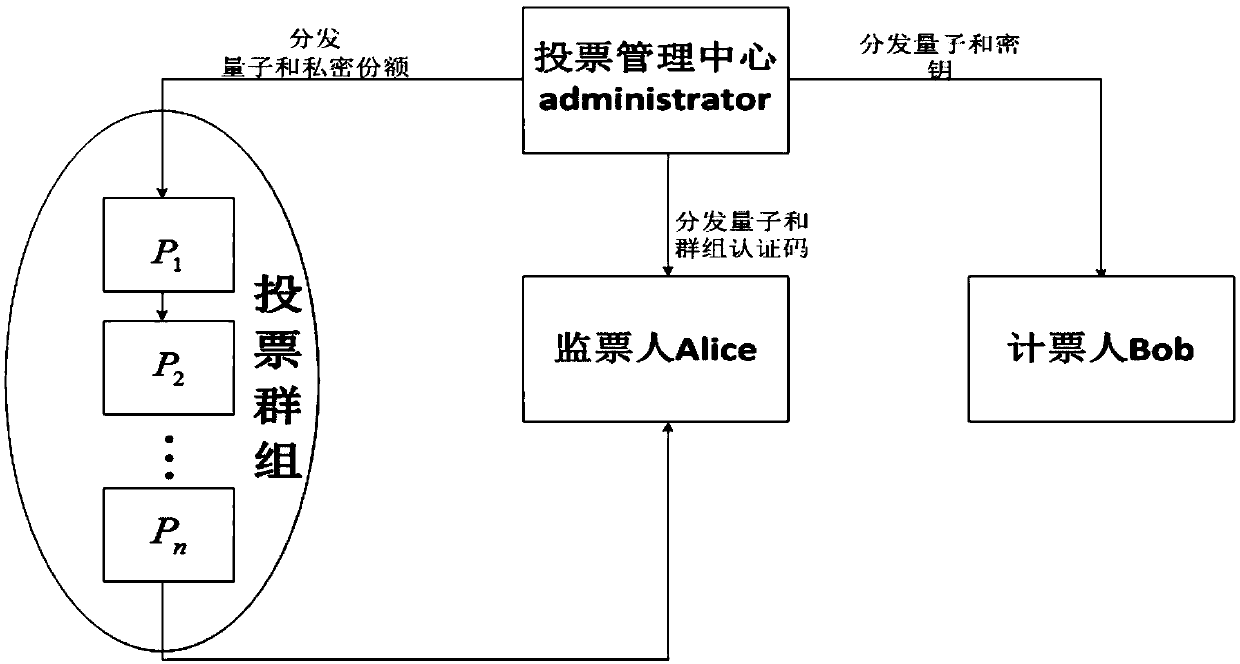
[0039] This example is a quantum voting protocol based on the d-dimensional three-quantum entangled state and using the idea of the shamir(t,n) threshold secret sharing scheme. This example is divided into the following parties according to the traditional voting model: voting management center administrator, voting group P 1 ,P 2 ...P n , the scrutineer Alice and the voter Bob. refer to figure 1 The method flowchart of the present invention can be roughly divided into an initialization stage, a group voting stage, a verification stage and a vote counting stage. A secure quantum channel can be established between the voting management center, voting groups, scrutineers and vote counters, and the voting management center transmits information such as initial quantum states, keys and auth...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com