Mobile phone token identity authentication system and method based on quantum cipher network
A technology of quantum cryptography and identity authentication, applied in the field of mobile phone token identity authentication system
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0092] This embodiment constructs a specific mobile phone token identity authentication system based on the quantum cryptography network, and provides a specific protocol of the system implementation process.
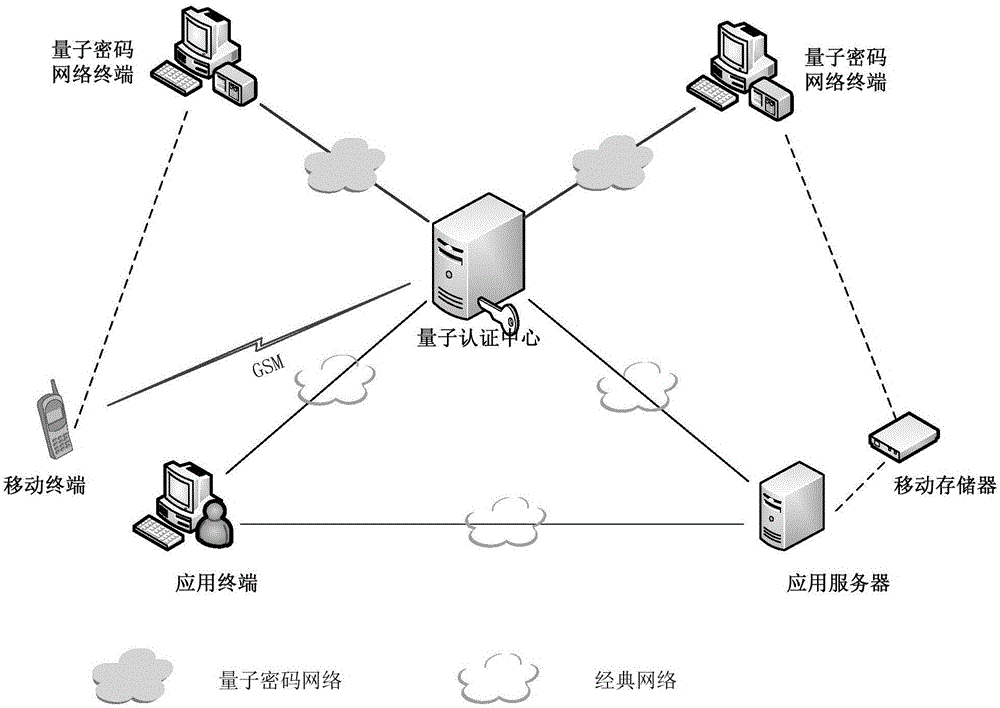
[0093] System structure such as figure 1 As shown, it includes a quantum authentication center, a quantum cryptography network terminal, a mobile terminal, an application terminal, an application server and a mobile memory. There can be one or more application servers. Quantum key encrypted communication is used between the quantum cryptography network terminal and the quantum authentication center. The quantum authentication center, the application server, and the application terminal use the classical network communication method to communicate.
[0094] The functions of each component of the system are briefly described as follows:
[0095] The Quantum Authentication Center provides identity authentication services for mobile terminals and application servers, and...
specific example
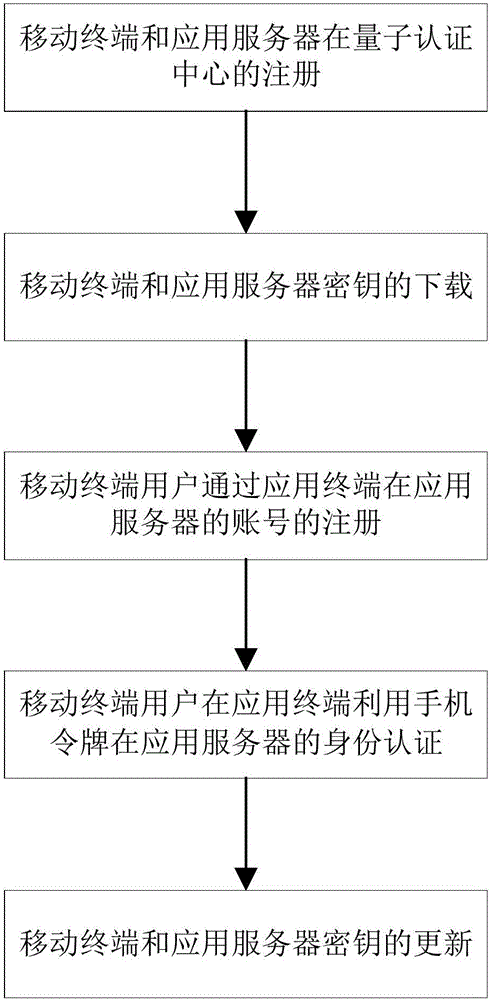
[0106] 1. The registration process of the mobile terminal and the application server in the Quantum Certification Center (hereinafter referred to as QCA).
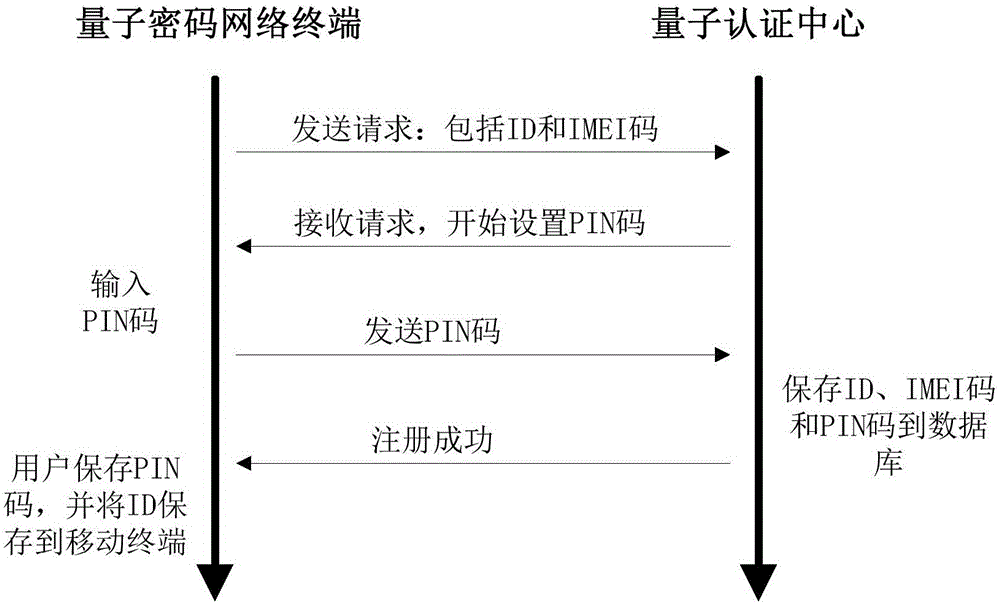
[0107] image 3 is the flow chart of mobile terminal registration in QCA through quantum cryptography network terminal, from image 3 You can clearly understand each step of mobile terminal registration in QCA. The mobile terminal realizes the registration in QCA through the quantum cryptography network terminal. During the registration process, the communication information between the quantum cryptography network terminal and QCA is encrypted and transmitted using the quantum key to ensure the security of the registration information. Preferably, in order to ensure the unconditional security of the registration information, a quantum key is used for one-time pad encryption. During the registration process, the mobile terminal user (hereinafter referred to as the user) first sets the user name (ID) to be registered, and...
Embodiment 2
[0142] This embodiment specifically describes the generation of the dynamic password of the mobile terminal and the method for verifying the dynamic password of the user by the quantum authentication center.
[0143] The dynamic password generation process is as follows: Figure 8 As shown, it is divided into the following steps:
[0144] Step 1: Divide the number of the unit quantum key.
[0145] The quantum key downloaded by the mobile terminal is logically divided into unit quantum keys according to the data length required for each dynamic password generation, and the unit quantum keys are numbered sequentially; the quantum authentication center adopts the same division and numbering method , and divide and number it with the corresponding shared quantum key between mobile terminals. The corresponding unit quantum keys between the mobile terminal and the quantum authentication center have the same number.
[0146] In this embodiment, the selected key-related hash operat...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com