Monitoring message alarming method and system
An alarm system and message technology, applied in the field of information processing, can solve problems such as low operation and maintenance efficiency, lack of alarm mechanism, application business cannot be quickly located, etc., and achieve the effect of improving maintenance efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
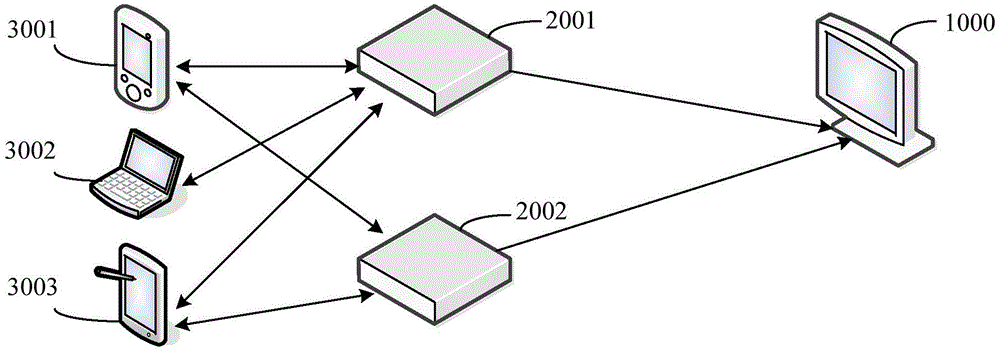
[0023] The alarm method for monitoring messages provided by the embodiments of the present invention can be applied to such as figure 2 shown in the application environment, please refer to the figure 2 As shown, the application environment may specifically include one or more clients ( figure 2 Take three clients as an example, that is, clients 3001~3003), one or more application platforms ( figure 2 Two application platforms are taken as an example, namely, application platforms 2001 and 2002), and a computer system 1000 capable of executing specified operations of the alarm method for monitoring messages according to the embodiment of the present invention. The client interacts with the application platform, and the application platform interacts with the computer system; the client may include smart devices, mobile terminals, personal computers, and similar devices. The application program can be run on the client, and a service request is initiated to the applicatio...
Embodiment 2
[0034] Such as Figure 4 As shown, an alarm method for monitoring messages is provided, and the method is illustrated by being applied to a computer system, including the following steps:
[0035] S41. Collect monitoring messages of each application platform; wherein, the monitoring messages include a service request identifier and a response status identifier of the service request;
[0036] S42. According to the service request identifier and the response status identifier of the service request, obtain the response status of the monitoring message with the same service request identifier;
[0037] S43. When it is judged that the response state of the monitoring message of the same service request identifier satisfies a preset alarm standard, search for a preset alarm object corresponding to the service request identifier, and send an alarm notification to the alarm object.
[0038] In the alarm method of the monitoring message in the embodiment of the present invention, the ...
Embodiment 3
[0049] see Figure 5 , Figure 5 It is a schematic flowchart of the third embodiment of the alarm method for monitoring messages of the present invention.
[0050] The main difference between the alarm method of the monitoring message in this embodiment and the second embodiment is that the step of obtaining the response status of the monitoring message with the same service request ID according to the service request ID and the response status ID of the service request, May include:
[0051] S51. Read the service request identifier, the response status identifier of the service request, and the processing time of the service request in each of the monitoring messages;
[0052] S52. Record the total number of service requests, successful service requests, or service request timeouts of the monitoring messages with the same service request identifier within the preset monitoring time;
[0053] S53. Determine the response status of the monitoring message according to the prop...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com