A secure printing audit system based on facial recognition
A face recognition and secure printing technology, applied in the direction of digital output to printing unit, calculation, data processing input/output process, etc., can solve the problems of low recognition rate, unrecognizable, unstable identification of biological characteristics, etc., to reduce control The effects of risk, complexity, humanization, and simplicity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
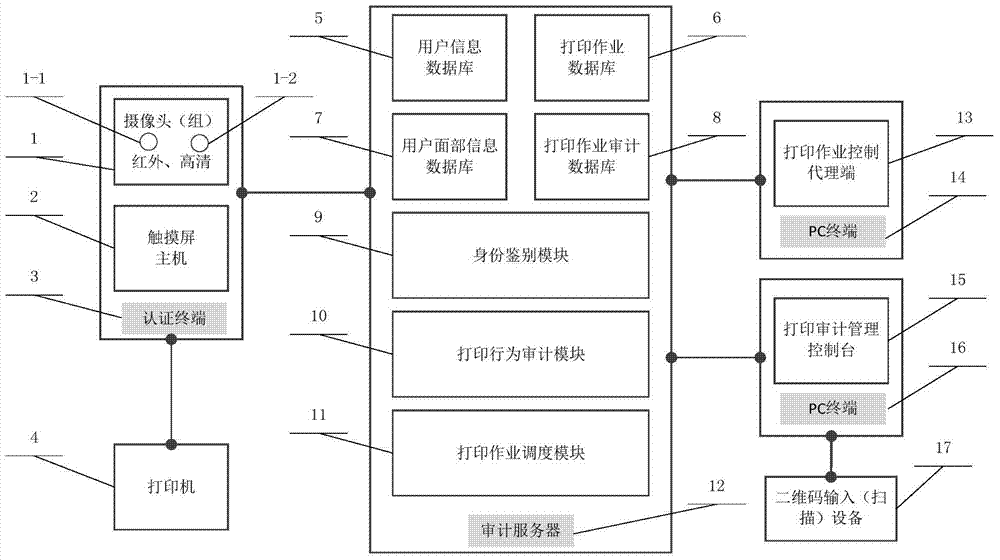
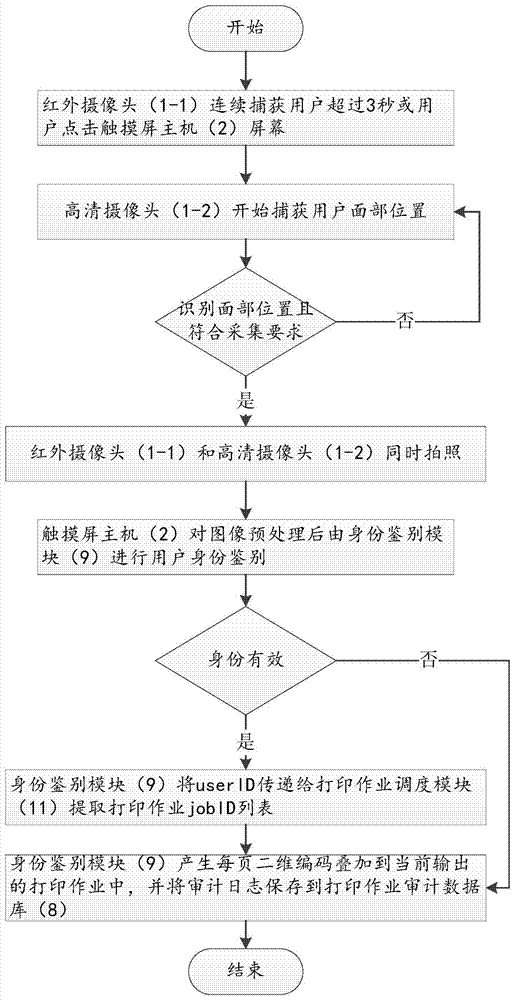
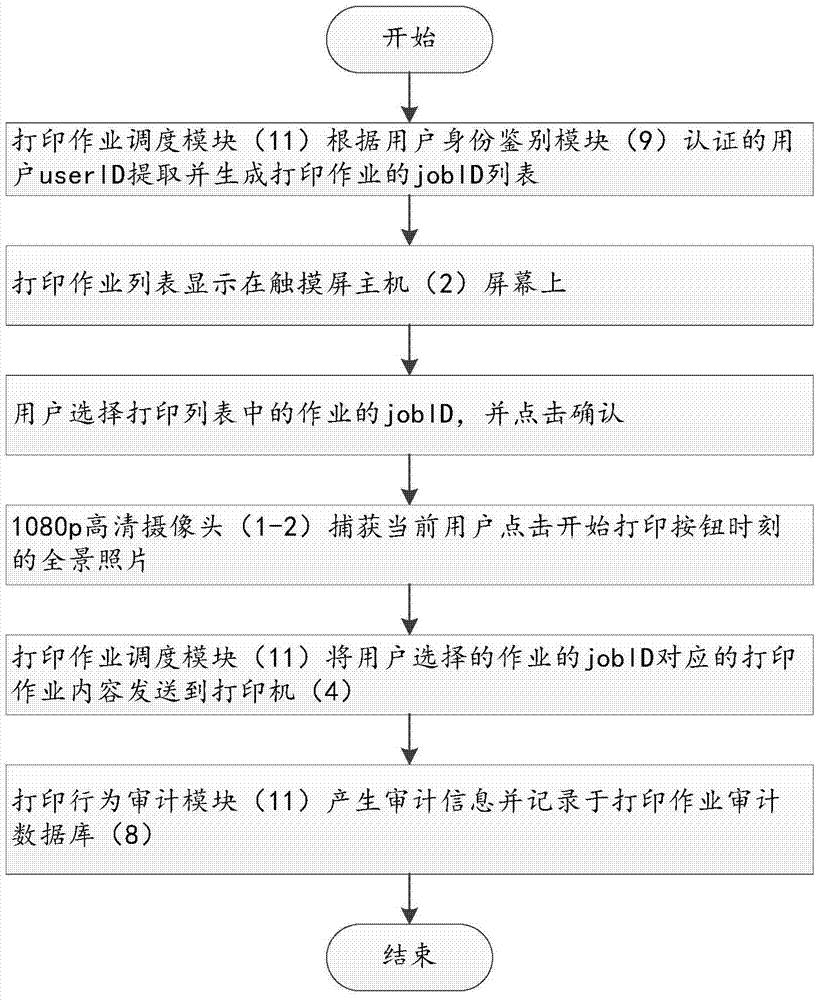
[0024] Such as figure 1 As shown, the present invention includes a camera group 1, an infrared camera 1-1, a high-definition camera 1-2, a touch screen host 2, an authentication terminal 3, a printer 4, a user information database 5, a print job database 6, a user facial information database 7, a printing Job audit database 8, identity authentication module 9, print behavior audit module 10, print job scheduling module 11, audit server 12, print job control agent 13, PC terminal 14, print audit management console 15, PC terminal 16, two-dimensional Code input (scanning) device 17. The camera group 1 is connected to the authentication terminal 3, the authentication terminal 3 is connected to the printer 4, the authentication terminal 3 is connected to the audit server 12, the PC terminal 14 is connected to the audit server 12, the PC terminal 16 is connected to the audit server 12, and the PC terminal 16 is connected to the two-dimensional Code input (scanning) device 17 is co...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com