Privacy space processing method and privacy space processing device
An information processing device and privacy technology, which is applied in the field of network information security, can solve problems such as cumbersome system attribute setting process, user privacy information hidden setting, and user inconvenience, so as to improve business experience, simplify cumbersome operations, and improve security. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0024] Embodiment 1. A method for processing a private space.
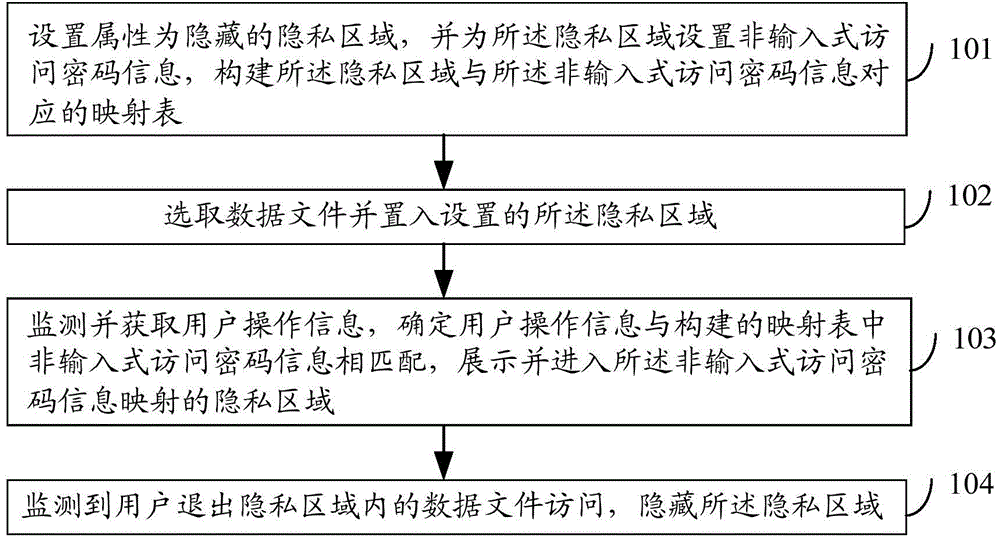
[0025] figure 1 is a schematic flowchart of a method for processing a private space provided by an embodiment of the present invention. see figure 1 , the process includes:
[0026] Step 101, setting the attribute as a hidden privacy area, setting non-input access password information for the privacy area, and constructing a mapping table corresponding to the privacy area and the non-input access password information;
[0027] In this step, the content in the private space includes but is not limited to: the user's private information, applications, materials, pictures, videos, etc. Data files include but are not limited to: applications, pictures, etc.
[0028] The set privacy area can be one, and in subsequent applications, all data files that need privacy protection are put into this privacy area. In the embodiment of the present invention, in order to prevent other users from knowing all the data files th...
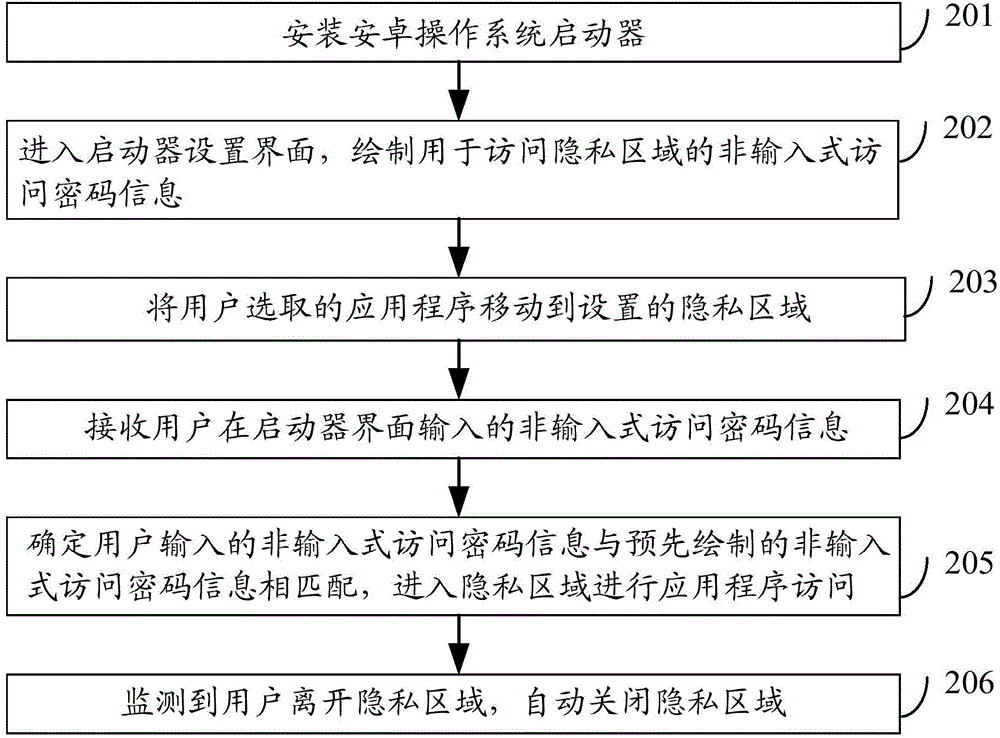
Embodiment 2
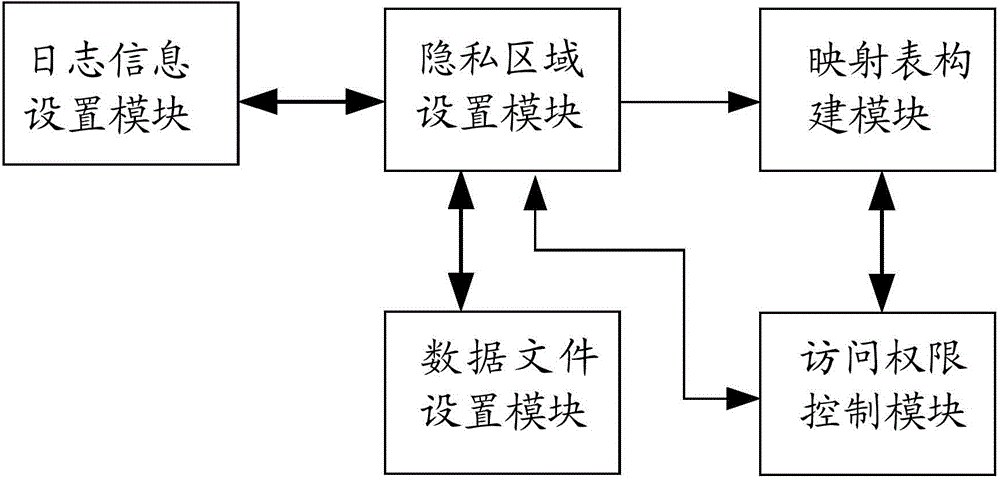
[0119] Embodiment 2, a privacy space processing device.
[0120] image 3 It is a schematic structural diagram of a privacy space processing device provided by an embodiment of the present invention. see image 3 , the device includes: a privacy area setting module, a mapping table building module, a data file setting module and an access control module, wherein,
[0121] The privacy area setting module is used to set the property as a hidden privacy area;
[0122] In the embodiment of the present invention, one or more privacy areas are set.
[0123] As an optional embodiment, storage path information used to identify the location of the privacy area may also be set. Multiple privacy areas may correspond to the same storage path information, or may correspond to different storage path information, which may be set according to the actual needs of the user.
[0124] A mapping table construction module, configured to set non-input access password information for the privac...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com