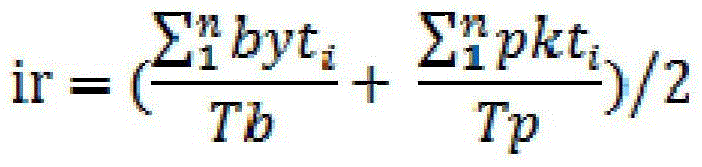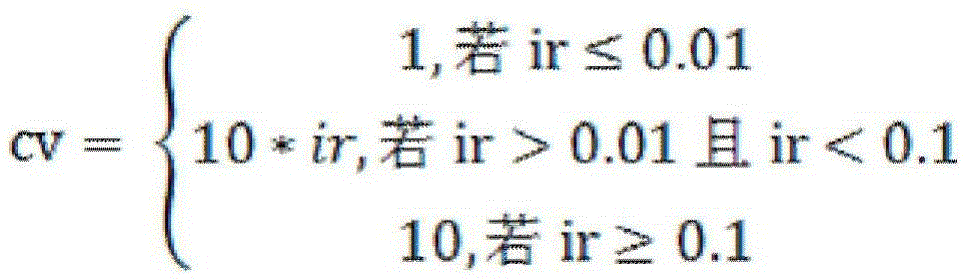Realizing method of network attack event quantitative hierarchical algorithm
A network attack and implementation method technology, applied to electrical components, transmission systems, etc., can solve problems such as inconsistency and inaccurate classification of security events
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
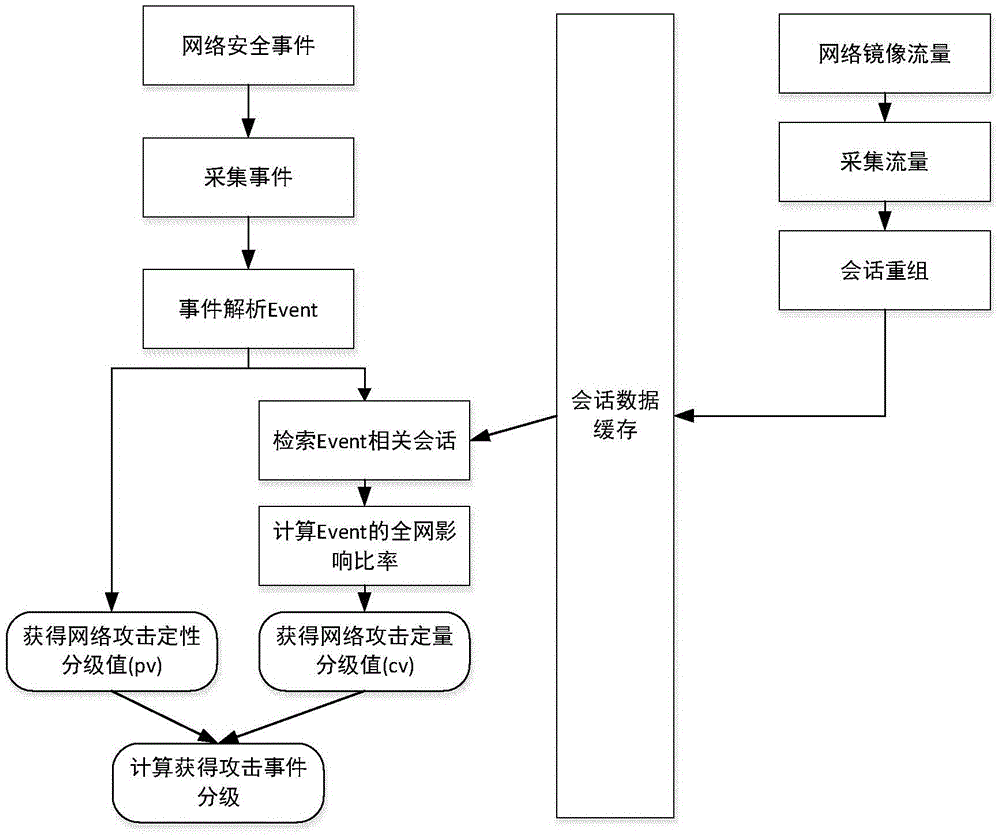
[0037] A method for implementing a fault-tolerant distributed security event data transmission protocol, characterized in that:
[0038] A. Obtain network attack events by means of Syslog protocol or log text reading. Each network attack event is called Event, and the regular expression algorithm is used to analyze the quintuple information of the network attack event. The quintuple information includes: attack Source IP, attack destination IP, attack start time, attack end time, attack severity level, the attack severity level includes qualitative expressions of "serious" and "slight";
[0039] B. Map the attack severity level of the network attack event into values of 1, 2, 3, 4, 5, 6, 7, and 8 through the event level mapping table, and this value is called the network attack qualitative rating value pv;
[0040] C. Collect the traffic packet data of the attacked network through the mirror traffic technology, and use the traffic analysis algorithm to obtain the network ses...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com