Method for solving key collision problem of combined public key (CPK)
A technology that combines public keys and keys, applied in the field of cryptography, and can solve problems such as difficulty in key replacement and user key collision
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
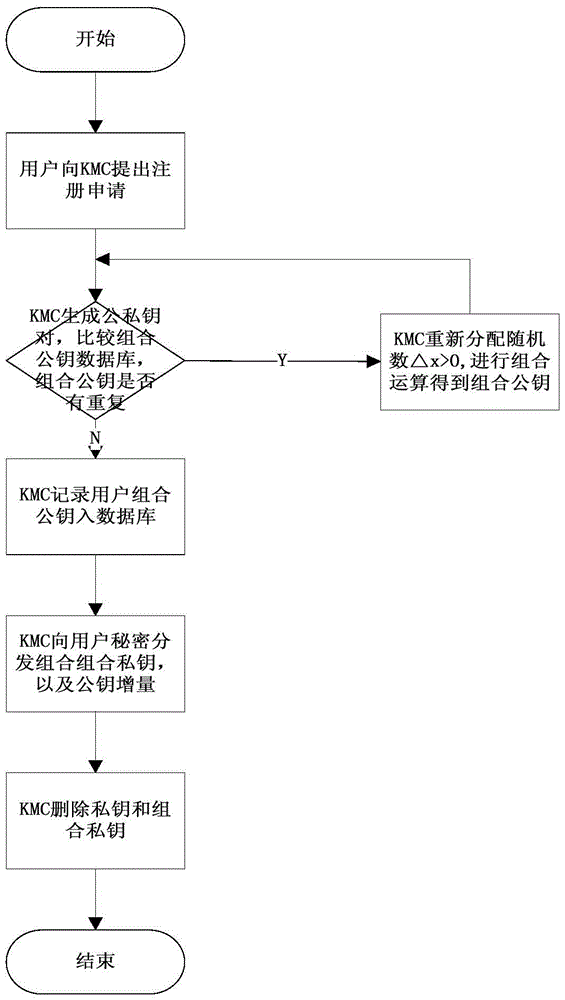
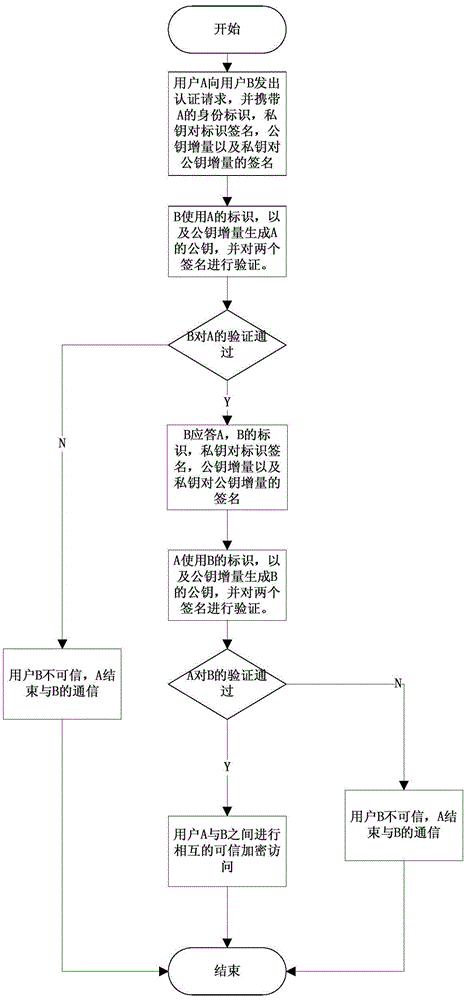
[0025] Below in conjunction with accompanying drawing, technical scheme of the present invention is described in further detail:
[0026] To generate the identification key of CPK, firstly, the selection sequence of public-private key factors is generated through the hash operation of user identification and the row mapping algorithm, and then the corresponding elements are selected in the public-private key matrix, and combined to generate a public-private key pair. The factors corresponding to the positions in the public-private key matrix satisfy the elliptic curve discrete logarithm problem ECDLP. There are two reasons for the collision of user keys: the mapping coordinates are the same as the selected coefficients, which are generated by the hash operation, and the result of the modulo addition operation is the same. The CPK review report of the 2007 European Cryptography Annual Conference believes that the security problem of hash should not be regarded as the security p...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com