Message reverse push method, network management system alarm method and state update method
A message and reverse technology, applied in transmission systems, digital transmission systems, data exchange networks, etc., can solve problems such as performance consumption
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
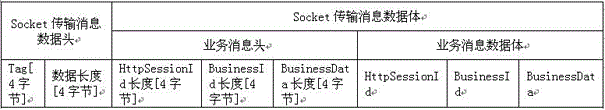
Image
Examples
specific Embodiment
[0063] 1. The browser client establishes a socket connection with the server. The process of establishing a connection includes the following steps: First, the flex plug-in encapsulated in the browser will first send a string " ", to request a security policy file, and the server will return the security policy file directly in XML format after receiving this string;
[0064] The client sends a connection request to the server again according to the access rights described in the security policy file returned by the server. The connection request includes the request ID, server IP, and port number. After the server receives the connection request from the client, the server Save the connection request ID of the client, establish a long socket connection with the client, and complete the establishment of the connection with the browser server, as shown in the connection establishment process.
[0065] 2. Message reception: Complete the reception of the push message from the se...
Embodiment 2
[0069] Pushing messages from the server to the browser is a business model with better user experience. According to different business requirements, the push messages can be displayed in real time and in various ways. In the network management system, this message push technology is fully utilized to complete various tasks. Such business functions better meet the network maintenance requirements of network administrators.
[0070] Real-time alarm monitoring
[0071] The main function of real-time alarm monitoring is to present the alarm information generated by the managed equipment in the system in real time, which is convenient for network maintenance personnel to locate and deal with network faults. If the level has changed, the different functional pages in the system should be able to reflect this change in a timely manner, which is convenient for network maintenance personnel to find and deal with faults. It is the push process after an alarm occurs. After the server c...
Embodiment 3
[0081] 1) The user accesses the network management system through a browser. After successful login, the flex plug-in in the browser will request the security policy file from the server.
[0082] 2) After receiving the command requesting the security policy file, the network management server returns the security policy file to the flex plug-in in the browser.
[0083] 3) The flex plug-in in the browser requests the server to establish a socket connection again according to the permission constraints in the security policy file.
[0084] 4) After receiving the connection request, the network management server establishes a socket connection with the flex plug-in in the browser, and records the mapping relationship between the connection request identifier and the socket connection identifier.
[0085] 5) The network management collection server will detect whether the management device is online in real time. After the detection is completed, it will get the online and offlin...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com