User fraud suspiciousness degree calculation method and suspiciousness degree calculation system
A calculation method and technology of a calculation system, applied in the field of communication, can solve problems such as loss of income, potential information security risks, and fraudulent users, and achieve the effects of increasing call charges, improving network information security, and increasing operating income
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
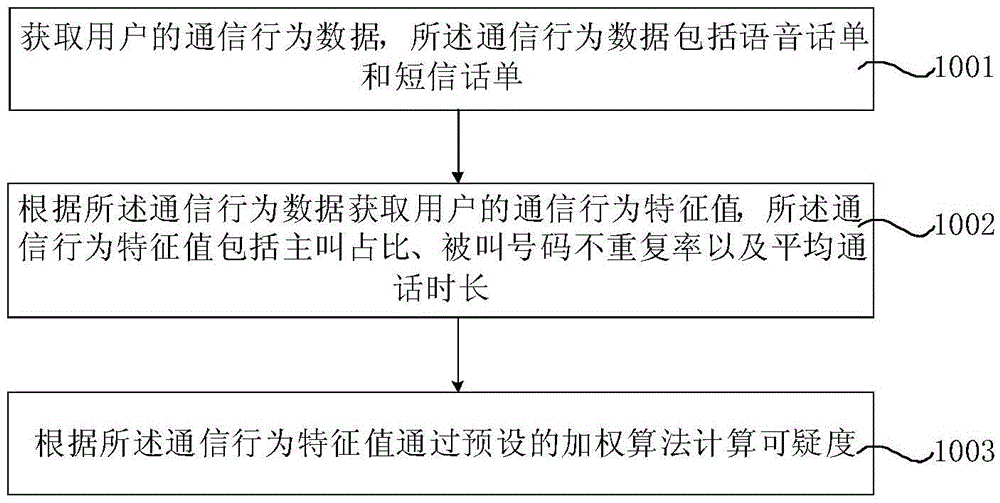
[0052] figure 1 It is a flow chart of a method for calculating the suspiciousness of fraudulent users provided by Embodiment 1 of the present invention. Such as figure 1 As shown, the method for calculating the suspicious degree of the fraudulent user includes:
[0053] Step 1001. Obtain communication behavior data of a user, the communication behavior data including voice bills and short message bills.
[0054] Step 1002: Obtain the characteristic value of the user's communication behavior according to the communication behavior data, and the characteristic value of the communication behavior includes the proportion of callers, the non-repetition rate of called numbers, and the average call duration.
[0055]In this embodiment, the characteristic value of communication behavior may also include effective call duration, LAC / Cellid change frequency, and number of short messages sent. Specifically, the proportion of calling calls is defined as: within a unit time, the ratio o...
Embodiment 2
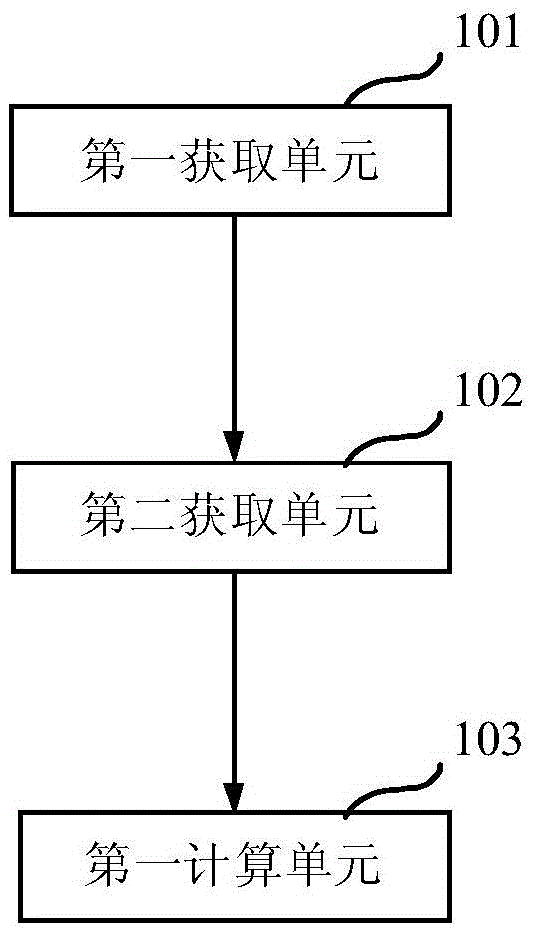
[0069] figure 2 It is a schematic structural diagram of a system for calculating the suspiciousness of fraudulent users provided by Embodiment 2 of the present invention. Such as figure 2 As shown, the system for calculating the suspiciousness of fraudulent users includes a first acquisition unit 101 , a second acquisition unit 102 and a first calculation unit 103 . The first acquiring unit 101 is configured to acquire communication behavior data of a user, and the communication behavior data includes voice bills and short message bills. The second acquiring unit 102 is configured to acquire the characteristic value of the user's communication behavior according to the communication behavior data, and the characteristic value of the communication behavior includes the percentage of calling, the non-repetition rate of the called number and the average call duration. The first calculation unit 103 is configured to calculate the suspiciousness through a preset weighting algor...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com