Access control method of user private data of online social networks
A social network and access control technology, which is applied in the direction of data exchange network, digital transmission system, electrical components, etc., can solve the problems that cannot meet the needs of customization, use control strategies are not applicable, and social network users are not applicable, etc., to achieve the method Novel and practical, reasonable method and humanized effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0023] The present invention will be further described below in conjunction with the accompanying drawings and embodiments.
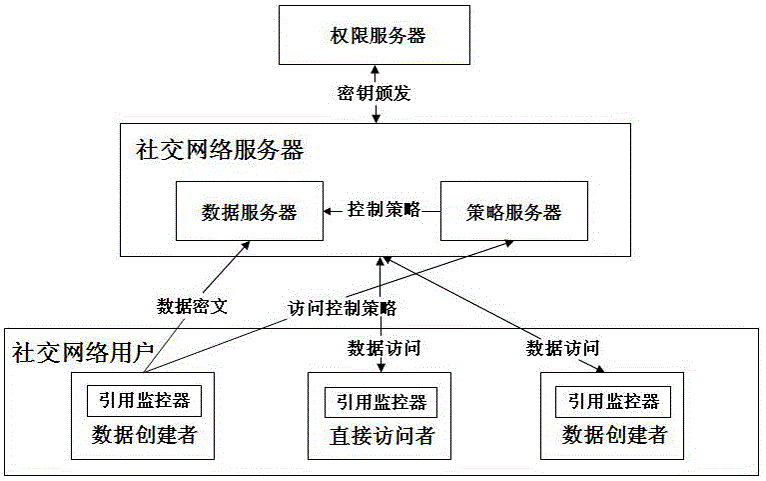
[0024] figure 1 It is a model schematic diagram of an embodiment of an access control method for online social network user private data in the present invention. Such as figure 1 , the model of an embodiment of the present invention mainly includes:
[0025] (1) Social network server: a semi-trusted service platform for managing registered users, including a data server and a policy server. The data server is responsible for storing encrypted object data uploaded by users, and the policy server is responsible for storing user-defined access control policies.
[0026] (2) Authority server: a trusted third-party platform that grants different access rights to network users by issuing keys based on network user attributes to network users.
[0027](3) OSNs network users: registered users of social network servers, and download and install reference mon...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com