Cipher algorithm anti-power consumption analysis realization method and device
A cryptographic algorithm and anti-power consumption technology, applied in the field of cryptography, can solve problems such as power consumption analysis, and achieve the effect of improving security and computing efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach
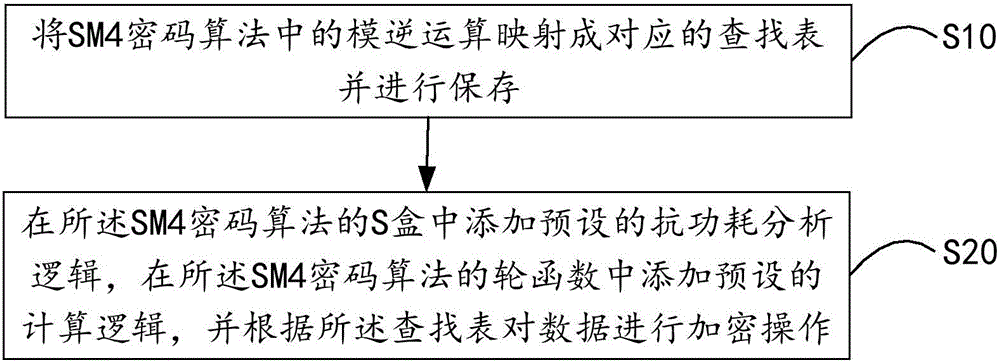
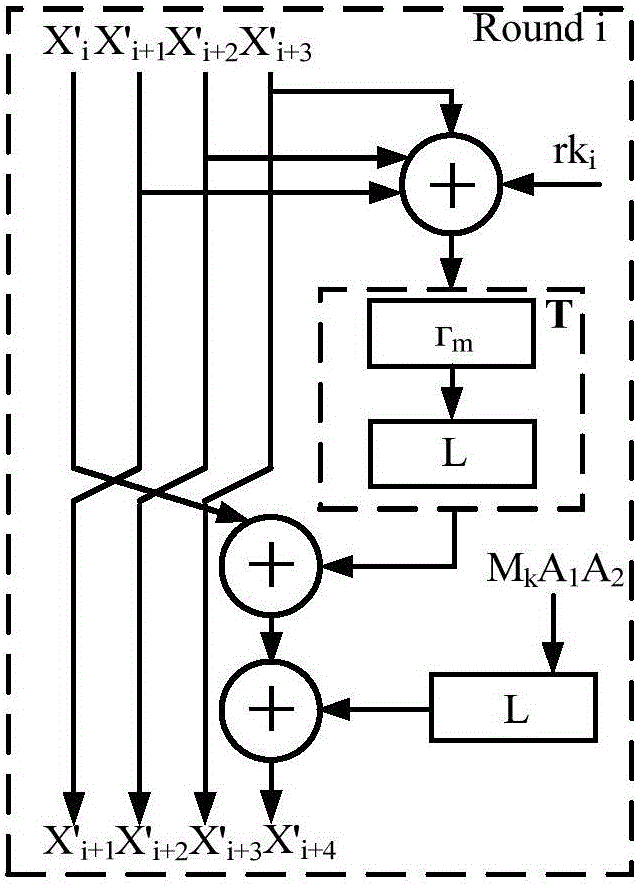
[0064] As an implementation manner, the above step S20 includes:
[0065] Step S21, adding anti-power consumption analysis logic in the S-box of the SM4 algorithm.
[0066] Specifically, after mapping the modular inversion operation in the SM4 encryption algorithm into a corresponding lookup table and saving it, the encryption device adds anti-power consumption analysis logic in the S-box of the SM4 algorithm.
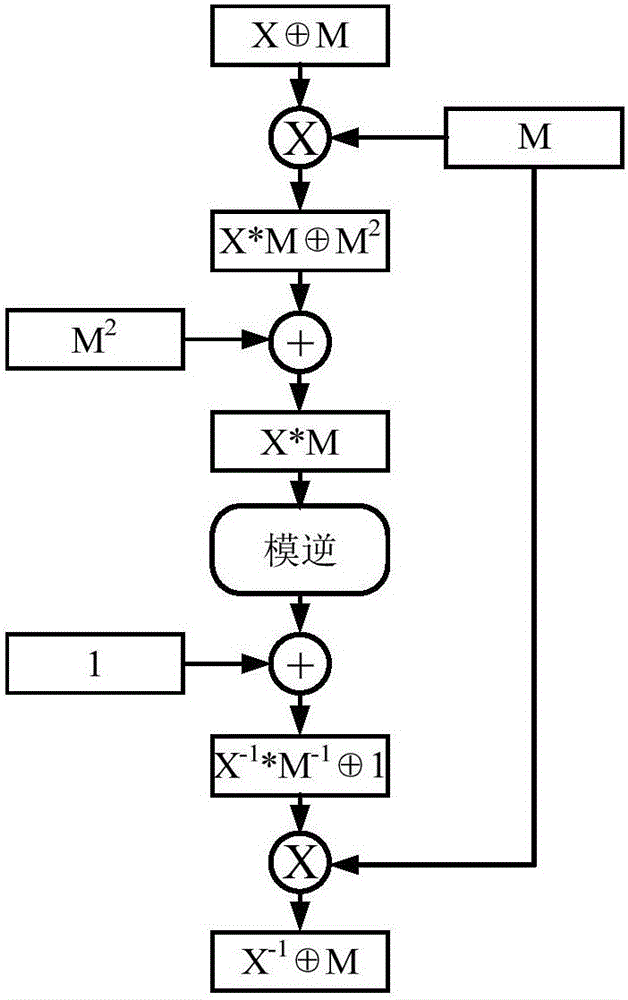
[0067] Among them, such as figure 2 As shown, in the specific implementation, the following methods can be adopted:
[0068] 1. The encryption device performs a multiplication operation: (XM)*M, and the result is X*MM 2 ;
[0069] 2. The encryption device performs XOR operation: (X*MM 2 ) M 2 , get the result X*M;
[0070] 3. The encryption device performs the modulo inverse operation: (X*M) -1 , get the result X -1 *M -1 ;
[0071] 4. The encryption device performs XOR operation: (X -1 *M -1 )1, get the result X -1 *M -1 1;
[0072] 5. The encryption d...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com