Encrypted data input method and encrypted data input device
A technology for encrypting data and input method, applied in the field of communication, can solve the problem of inability to ensure the security of data input, and achieve the effect of improving security and solving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
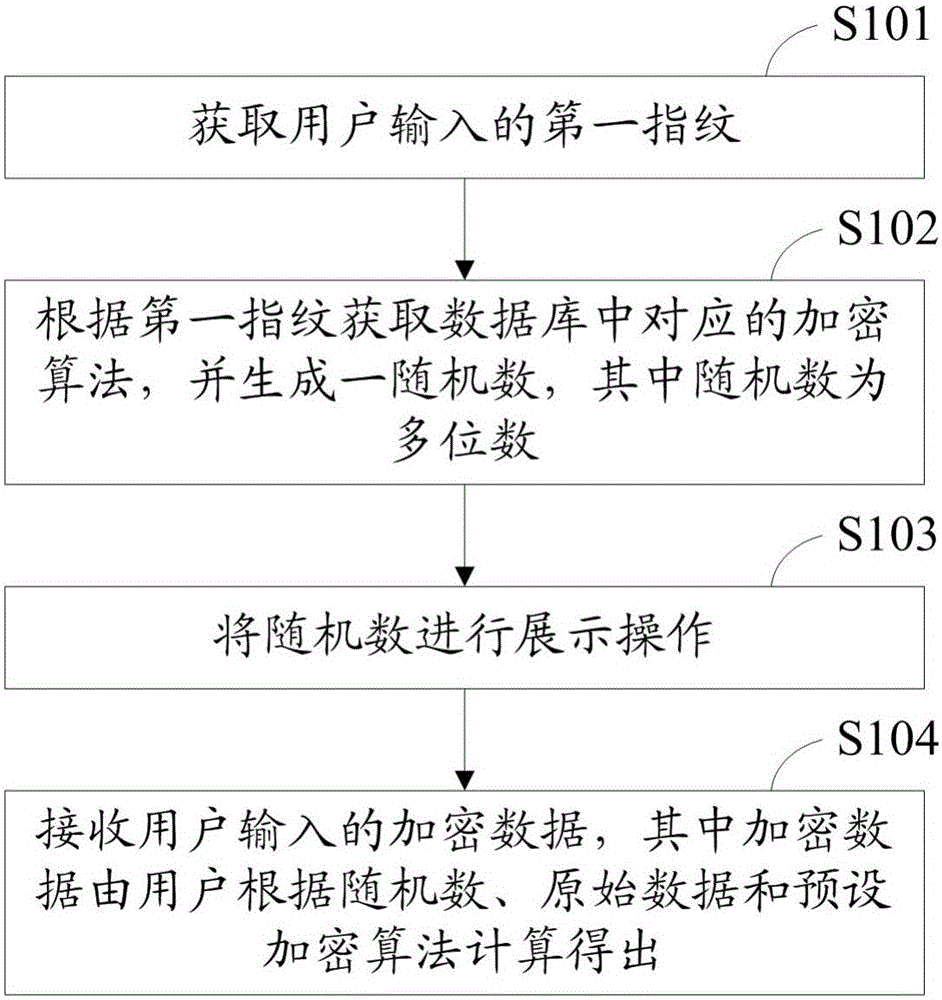
[0026] Please refer to figure 1 , figure 1 It is a flow chart of the first preferred embodiment of the encrypted data input method of the present invention. The encrypted data input method of this preferred embodiment includes:
[0027] Step S101, acquiring the first fingerprint input by the user;
[0028] Step S102, obtain the corresponding encryption algorithm in the database according to the first fingerprint, and generate a random number, wherein the random number has multiple digits;
[0029] Step S103, displaying the random number;
[0030] Step S104, receiving encrypted data input by the user, wherein the encrypted data is calculated by the user based on random numbers, original data and a preset encryption algorithm.
[0031] The specific flow of each step of the encrypted data input method in this preferred embodiment will be described in detail below.
[0032] In step S101, the terminal acquires a first fingerprint input by a user. The terminal obtains the firs...
Embodiment 2
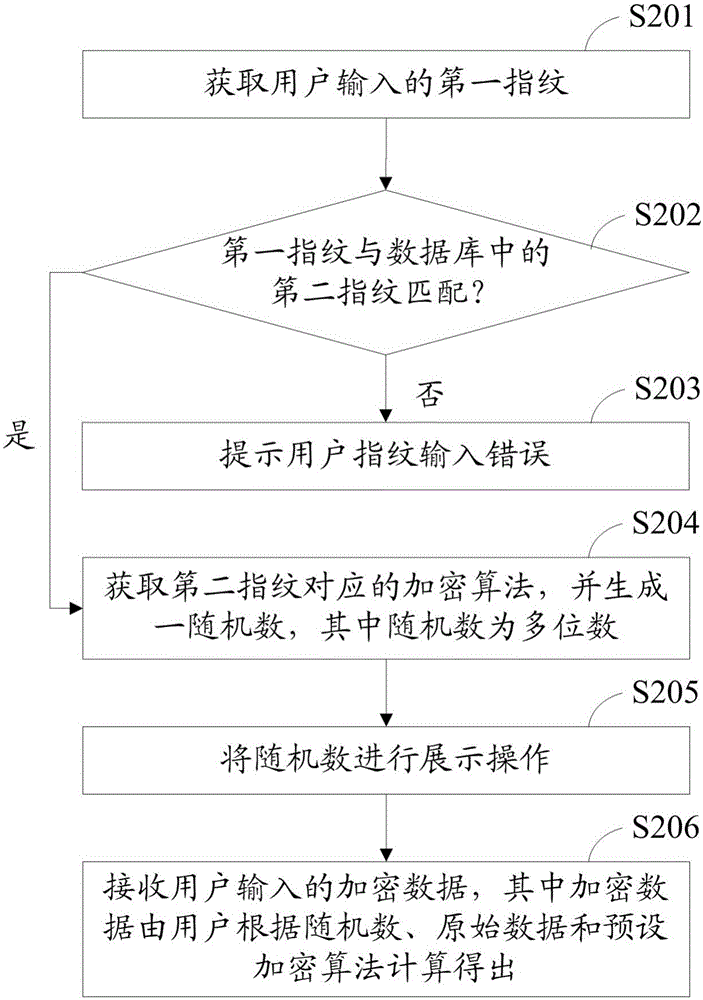
[0043] Please refer to figure 2 , figure 2 It is a flow chart of the second preferred embodiment of the encrypted data input method of the present invention. The encrypted data input method of this preferred embodiment includes:
[0044] Step S201, acquiring the first fingerprint input by the user;
[0045] Step S202, judging whether the first fingerprint matches the second fingerprint in the database;
[0046] Step S203, if the first fingerprint does not match the second fingerprint in step S202, prompting the user to input wrong fingerprint;
[0047] Step S204, if the first fingerprint matches the second fingerprint in step S202, then obtain the encryption algorithm corresponding to the second fingerprint, and generate a random number, wherein the random number is a multi-digit number;
[0048] Step S205, displaying the random number;
[0049] Step S206, receiving the encrypted data input by the user, wherein the encrypted data is calculated by the user according to the...
Embodiment 3
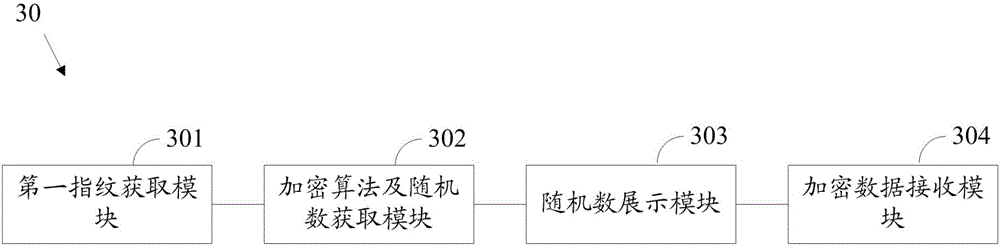
[0076] Please refer to image 3 , image 3 It is a structural diagram of the first preferred embodiment of the encrypted data input device of the present invention. The encrypted data input device 30 of this preferred embodiment includes a first fingerprint acquisition module 301 , an encryption algorithm and random number acquisition module 302 , a random number display module 303 and an encrypted data receiving module 304 . Wherein, the first fingerprint acquisition module 301 is used to acquire the first fingerprint input by the user; the encryption algorithm and random number acquisition module 302 is used to acquire the corresponding encryption algorithm in the database according to the first fingerprint, and generate a random number, wherein the random number is Multiple digits; the random number display module 303 is used to display the random number; the encrypted data receiving module 304 is used to receive the encrypted data input by the user, wherein the encrypted ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com