Secure transmission method based on Key assistance
A safe transmission and security technology, applied in the direction of security devices, advanced technology, electrical components, etc., can solve the problems of users without data transmission and waste of secure transmission opportunities
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0068] The present invention will be further described in detail below in conjunction with specific embodiments, which are explanations of the present invention rather than limitations.
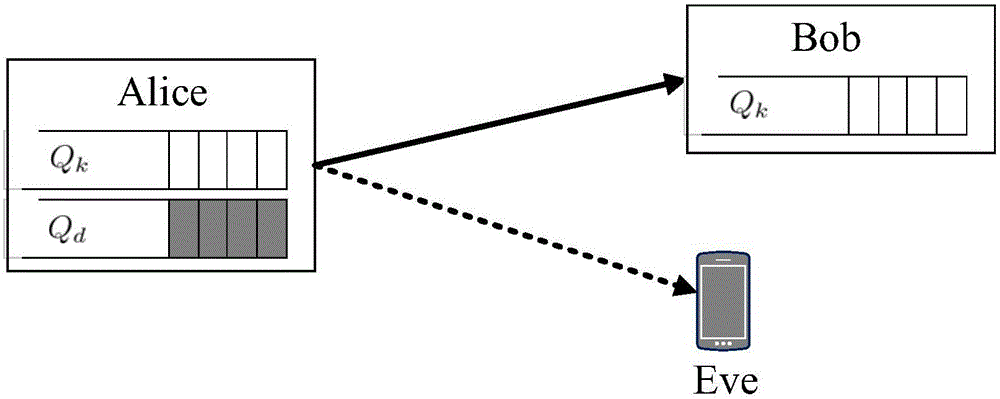
[0069] The present invention considers a three-node transmission network, such as figure 1 shown. The legal user Alice wants to transmit information to Bob safely and reliably, and Eve will eavesdrop on Alice's transmitted data. Alice has a data queue and a key queue. Bob also has a key queue, and this key queue is the same as Alice's. When the channel is not secure, Alice uses the Key packet to XOR securely encrypt the information.
[0070] It is assumed that the network experiences independent and smooth Rayleigh fading, that is, the channel state remains unchanged in each frame, and the channel state changes independently between different frames. In addition, each data frame is divided into two time slots, corresponding to the first transmission and retransmission of authorized users ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com