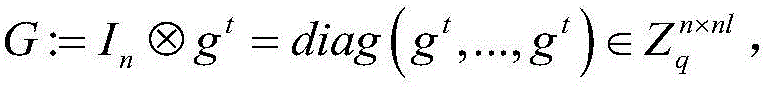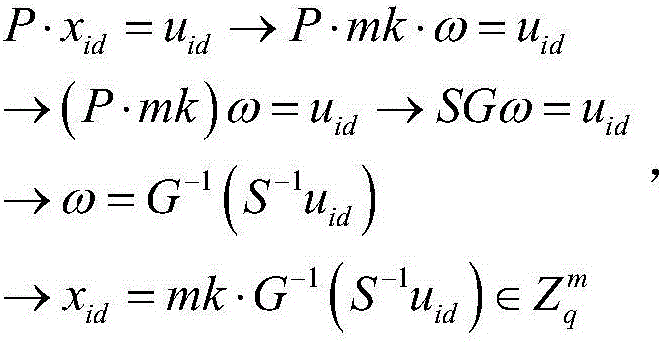Identity-based and hidden matrix-constructed fully homomorphic encryption method
A fully homomorphic encryption and secret matrix technology, applied in the field of information security, can solve the problem of indistinguishable encryption, and achieve the effect of saving time and space cost
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
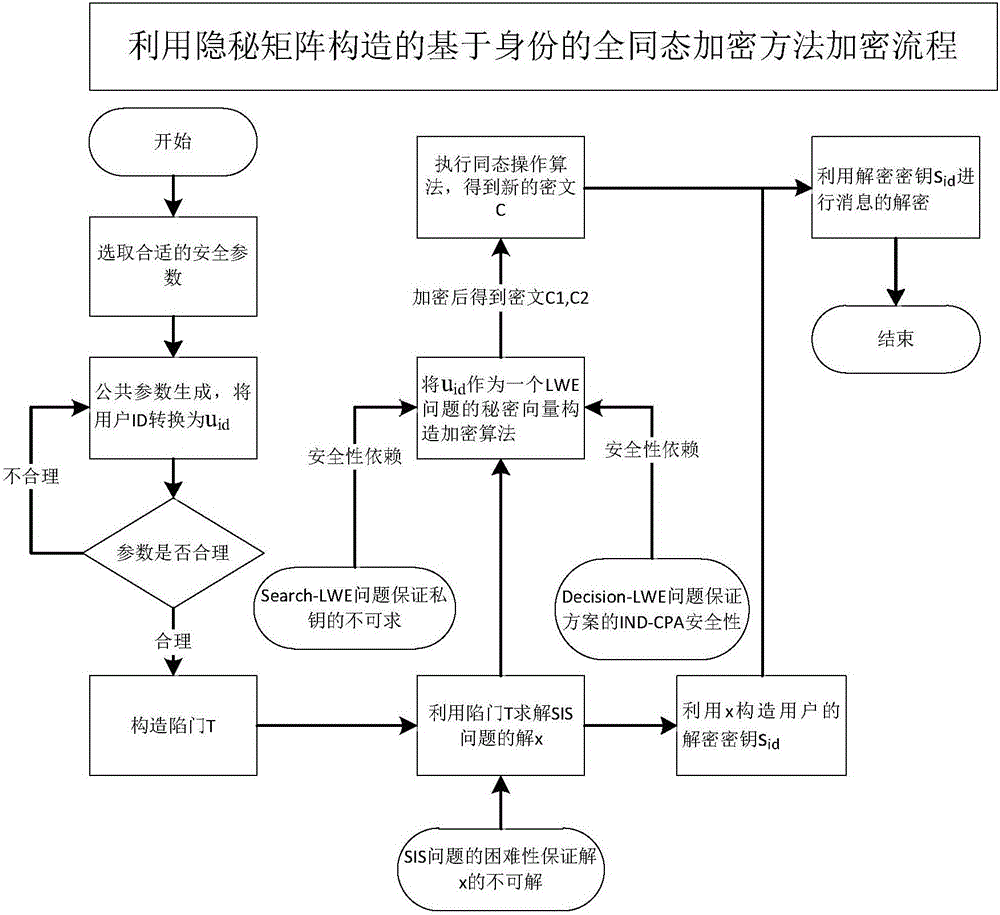
[0049] Use lowercase letters to represent vectors, all vectors default to column vectors, such as a, and the transpose (row vector) of vector a is represented as a t , the i-th element of vector a is denoted as a i . Matrices are represented by capital letters, such as M n × m , the i-th column of the matrix is denoted as M i , the transpose of matrix A is expressed as A T . Represents the ring of integers in n-dimensional modulo q.
[0050] The algorithm flow designed by the present invention is specifically as follows, firstly construct an identity-based encryption scheme LIBE on a grid:
[0051] parameter generation algorithm randomly generated matrix secret invertible matrix Trapdoor flag matrix Convert the ID representing the user's identity to a fixed-length finite ring using a hash function
[0052] Trapdoor Generation Algorithm output master key (trapdoor T) and parameters m=2nl, there is P·mk=SG here;
[0053] Key generation algorithm LIBE....
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com