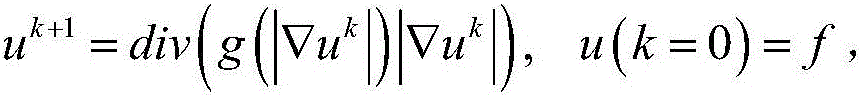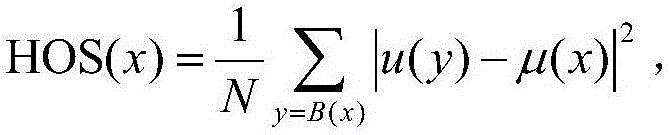Adaptive selection encryption method based on salient area
A technology of self-adaptive selection and encryption method, applied in the encryption device with shift register/memory, secure communication through chaotic signals, digital data protection, etc., can solve the problems of encryption redundancy and security instability, and achieve algorithmic Compatible formats, ensuring confidentiality, and improving the effect of attack resistance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0044] In order to make the purpose, technical solution and advantages of the present invention clearer, the specific implementation manners of the present invention will be clearly and completely described below.
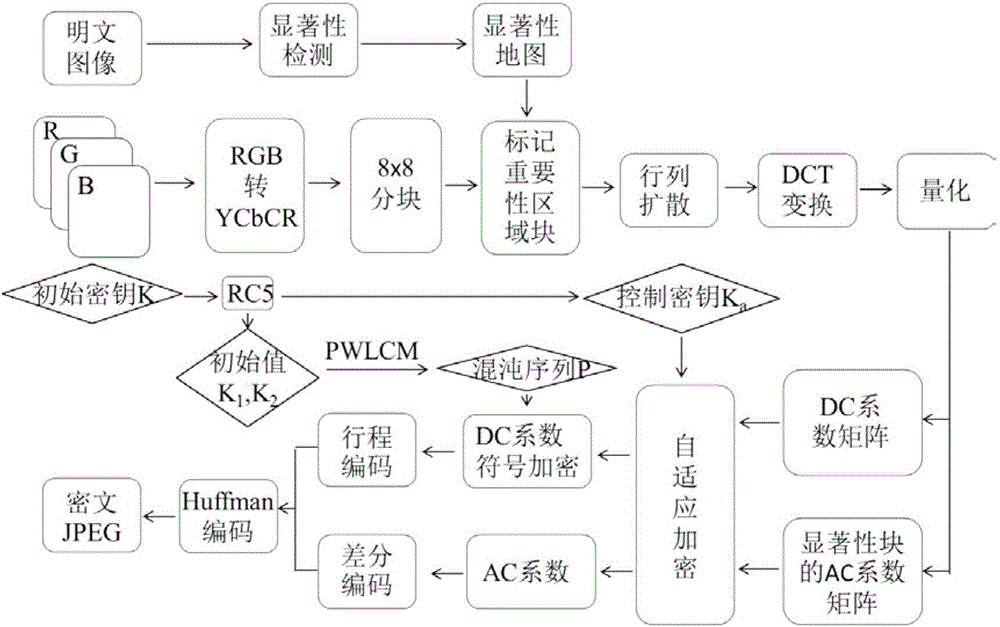
[0045] figure 1 A schematic diagram of the salient region-based adaptive selection encryption method provided by Embodiment 1 of the present invention. Such as figure 1 As shown, the method includes the following steps (1) to (8), and the above steps will be described in detail below.
[0046] (1) Perform saliency detection on the image and mark the saliency region.
[0047] This step performs saliency detection on the original image to obtain a saliency map, and marks the saliency region of the original image according to the saliency map. Specifically, this step uses the TASE saliency detection method to perform saliency detection on the image to obtain a saliency map. The method first performs non-linear diffusion on the image according to the total variation...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com