Encryption and decryption algorithm based on Chinese hash
An encryption and decryption algorithm, Chinese technology, applied in the field of encryption and decryption algorithms based on Chinese hash, can solve problems such as inconvenience for users to remember, and achieve the effects of fast encryption, security protection, and privacy protection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
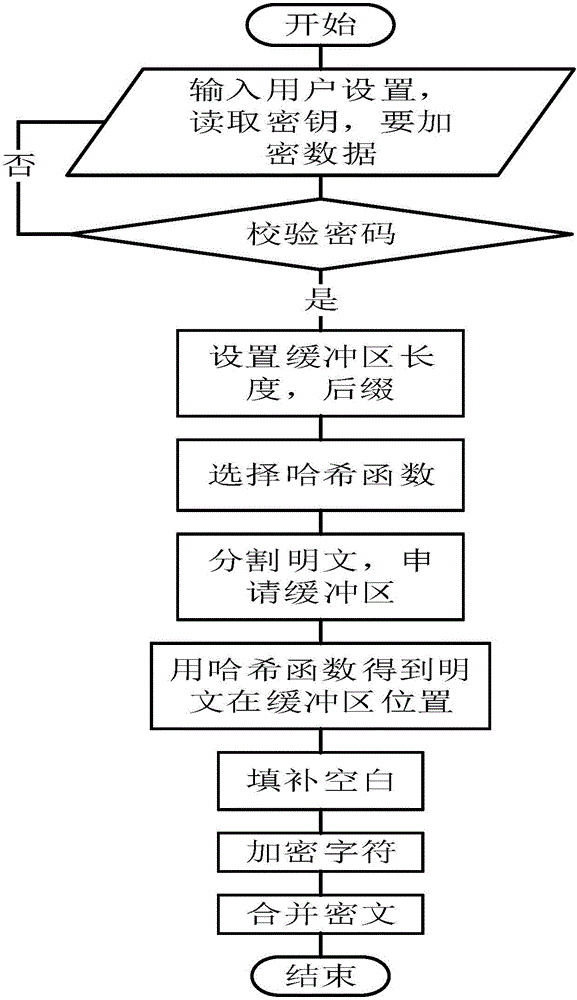
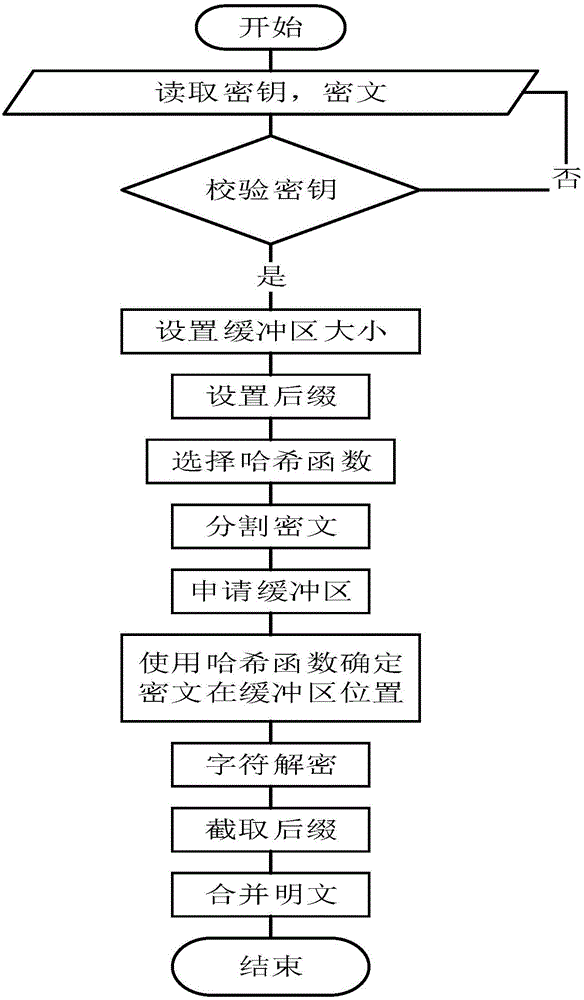
[0030] The encryption and decryption algorithm of the present invention uses a hash function to encrypt, and the key can use Chinese. The encryption process is as figure 1 shown, including the following steps:
[0031] S11, first process the input data: input user settings, read the key and the data to be encrypted; check whether the key (also called password) is correct, and then execute step S12 if it is correct;
[0032] S12. Apply for a buffer from the memory, and set the length and suffix of the buffer;
[0033] S13, select a hash function to process the data, and obtain the corresponding position of each plaintext character in the ciphertext; the hash function can be selected: a one-way n-th degree equation method, a method of dividing and leaving a remainder, a random number generation method or a key sorting Law.
[0034] S14. Split the plaintext and apply for a buffer zone;
[0035] S15. Store the temporary value obtained after the data is processed by the hash fu...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com