Digital virtual asset access control method based on attribute password under cloud environment
A technology of attribute cryptography and virtual assets, applied in the field of information security, can solve the problems of low decryption efficiency, inability to modify and limit users' digital virtual assets, and achieve the effect of reducing computational overhead and improving decryption and signature efficiency.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0024] The utility model will be further described in detail below in conjunction with the accompanying drawings and embodiments.
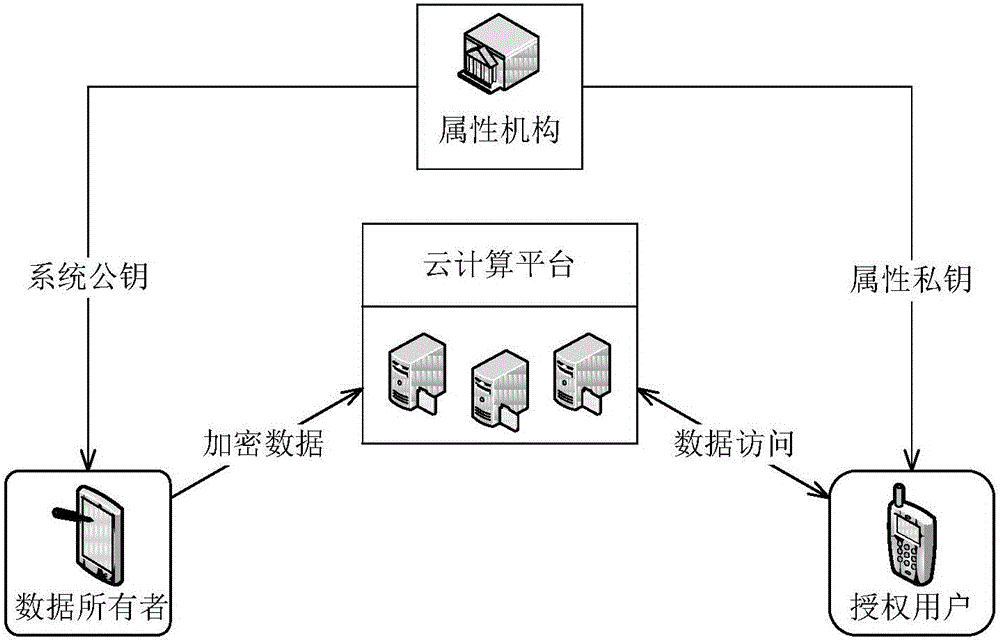
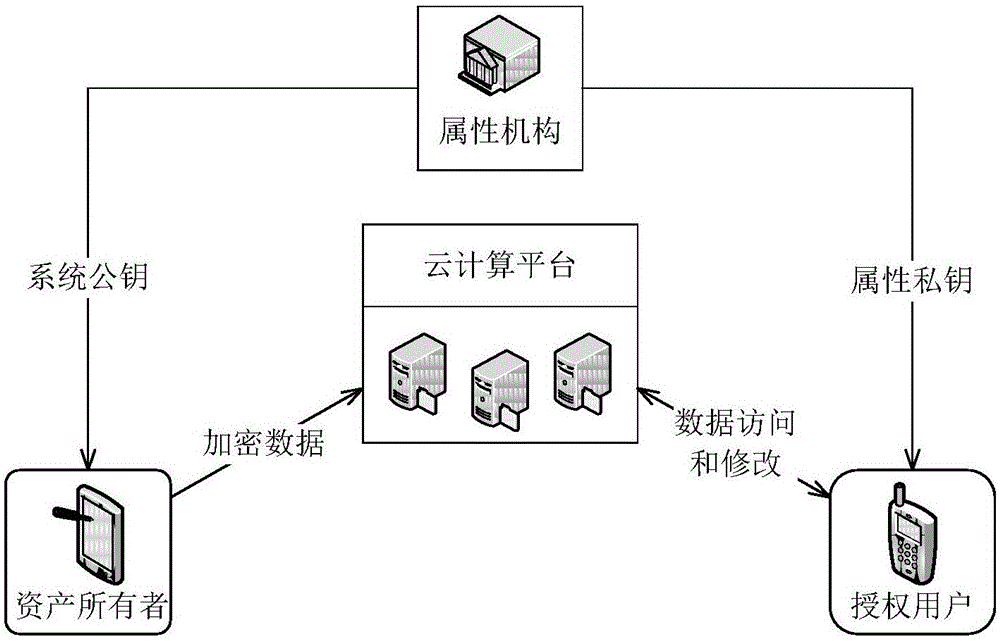
[0025] The present invention proposes a data virtual asset access control method based on attribute passwords in a cloud environment. The entities involved include: attribute organizations, cloud computing platforms, asset owners and authorized users, such as figure 2 As shown, the attribute authority is a trusted third party, which is used to establish the system public key and system master key; at the same time, the attribute authority assigns attributes to users, generates attribute private keys, and provides them to authorized users. The system public key is provided to the asset owner. The cloud computing platform is a semi-trusted third party for storing and managing digital virtual assets uploaded by asset owners. In addition, the cloud computing platform performs partial decryption and signature operations for the user, and at the same ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com